Chap32-PSWan
... • Dominated by the HDTV requirements – 600 Mb/s throughput to every home » Fiber to the home » Simple protocols implemented in hardware – Guaranteed Quality Of Service » Connection oriented protocol • General purpose network – HDTV, LDTV, Voice, Data » Different service classes – Very low data-rate ...
... • Dominated by the HDTV requirements – 600 Mb/s throughput to every home » Fiber to the home » Simple protocols implemented in hardware – Guaranteed Quality Of Service » Connection oriented protocol • General purpose network – HDTV, LDTV, Voice, Data » Different service classes – Very low data-rate ...
turbo 7 wireless gateway with voice (3g10wvt)
... Local (LAN) access (username: admin, password: admin) Remote (WAN) access (username: support, password: support) User access (username: user, password: user) LAN IP address: 10.0.0.138 Remote WAN access: disabled NAT and firewall: enabled Dynamic Host Configuration Protocol (DHCP) server on LAN inte ...
... Local (LAN) access (username: admin, password: admin) Remote (WAN) access (username: support, password: support) User access (username: user, password: user) LAN IP address: 10.0.0.138 Remote WAN access: disabled NAT and firewall: enabled Dynamic Host Configuration Protocol (DHCP) server on LAN inte ...
Ethernet Passive Optical Network (EPON)
... strength is lower at the OLT, which is most likely due to the longer distance. ...
... strength is lower at the OLT, which is most likely due to the longer distance. ...
PPT_ch05
... • PoE standard specifies two types of devices: – PSE (power sourcing equipment) – PD (powered devices) ...
... • PoE standard specifies two types of devices: – PSE (power sourcing equipment) – PD (powered devices) ...
Access Control Lists Lecture 1
... and/or deny statements that control the flow of particular protocols or protocol suits in or out of an interface to a specific host or group of hosts ...
... and/or deny statements that control the flow of particular protocols or protocol suits in or out of an interface to a specific host or group of hosts ...
OSI model (Wikipedia).
... to provide a unified data-carrying service for both and the scope of the direct links to other nodes on the circuit-based clients and packet-switching clients local network.[18] which provide a datagram-based service model. It can be used to carry many different kinds of traf- Despite using a different ...
... to provide a unified data-carrying service for both and the scope of the direct links to other nodes on the circuit-based clients and packet-switching clients local network.[18] which provide a datagram-based service model. It can be used to carry many different kinds of traf- Despite using a different ...
manual de fabricante del cablerouter Technicolor TC7210
... Turning on the Wireless Voice Gateway After installing the Wireless Voice Gateway and turn it on for the first time (and each time the modem is reconnected to the power), it goes through several steps before it can be used. Each of these steps is represented by a different pattern of flashing lights ...
... Turning on the Wireless Voice Gateway After installing the Wireless Voice Gateway and turn it on for the first time (and each time the modem is reconnected to the power), it goes through several steps before it can be used. Each of these steps is represented by a different pattern of flashing lights ...
Tomorrow’s In-Car Interconnect? A Competitive Evaluation of IEEE 802.1 AVB
... are highly application specific, and inter-domain coordination requires gateways that translate the messages from one technology to the other. New in-car network architectures feature a flat backbone that allows intra- and inter-domain communication on a single access layer using switched Ethernet. ...
... are highly application specific, and inter-domain coordination requires gateways that translate the messages from one technology to the other. New in-car network architectures feature a flat backbone that allows intra- and inter-domain communication on a single access layer using switched Ethernet. ...
1 - Salisbury University
... use existing telephone line to central office DSLAM data over DSL phone line goes to Internet voice over DSL phone line goes to telephone net < 2.5 Mbps upstream transmission rate (typically < 1 Mbps) < 24 Mbps downstream transmission rate (typically < 10 Mbps) Introduction 1-15 ...
... use existing telephone line to central office DSLAM data over DSL phone line goes to Internet voice over DSL phone line goes to telephone net < 2.5 Mbps upstream transmission rate (typically < 1 Mbps) < 24 Mbps downstream transmission rate (typically < 10 Mbps) Introduction 1-15 ...
Queuing Disciplines
... As part of the resource allocation mechanisms, each router must implement some queuing discipline that governs how packets are buffered while waiting to be transmitted. Various queuing disciplines can be used to control which packets get transmitted (bandwidth allocation) and which packets get dropp ...
... As part of the resource allocation mechanisms, each router must implement some queuing discipline that governs how packets are buffered while waiting to be transmitted. Various queuing disciplines can be used to control which packets get transmitted (bandwidth allocation) and which packets get dropp ...
ABLELink - automa.it
... GW51C-MAXI Serial Server is a gateway between Ethernet (TCP/IP) and RS-232/RS-485 communications. The information transmitted by GW51C-MAXI Serial Server is transparent to both host computers (Ethernet) and devices (RS-232/RS-485). Data coming from the Ethernet (TCP/IP) is sent to the designated RS- ...
... GW51C-MAXI Serial Server is a gateway between Ethernet (TCP/IP) and RS-232/RS-485 communications. The information transmitted by GW51C-MAXI Serial Server is transparent to both host computers (Ethernet) and devices (RS-232/RS-485). Data coming from the Ethernet (TCP/IP) is sent to the designated RS- ...
PDF
... When the switch starts up, it connects to the director. If the switch detects any new images or configuration files, it automatically restarts in factory-default mode and then downloads and installs the new images or configuration files. These are the supported types of image and configuration upgra ...
... When the switch starts up, it connects to the director. If the switch detects any new images or configuration files, it automatically restarts in factory-default mode and then downloads and installs the new images or configuration files. These are the supported types of image and configuration upgra ...
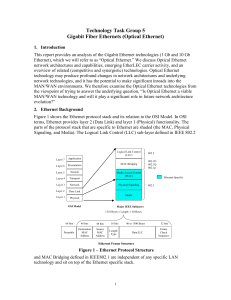
Gigabit Fiber Ethernets (Optical Ethernet)
... cuts. Various load-sharing techniques are used with priorities for different Class of Service (CoS) being indicated by the 3-bit user priority field in the VLAN tag. If insufficient capacity is provided to handle all of the traffic under failure conditions, the CoS indication can be used to allocate ...
... cuts. Various load-sharing techniques are used with priorities for different Class of Service (CoS) being indicated by the 3-bit user priority field in the VLAN tag. If insufficient capacity is provided to handle all of the traffic under failure conditions, the CoS indication can be used to allocate ...
Link Layer Topology Discovery in an Uncooperative Ethernet Environment by Johannes Petrus Delport
... or place and logos meaning study [1, 2]. In computer networking terms this study of location refers to the layout of and relationships between elements of a network. Topology discovery refers to the process whereby the topology information is extracted from the network. In particular, physical or li ...
... or place and logos meaning study [1, 2]. In computer networking terms this study of location refers to the layout of and relationships between elements of a network. Topology discovery refers to the process whereby the topology information is extracted from the network. In particular, physical or li ...
Glossary of z/OS terms and abbreviations
... application. A program or set of programs that performs a task; some examples are payroll, inventory management, and word processing applications. application layer. In the Open Systems Interconnection (OSI) reference model, the layer that provides means for application processes residing in open sy ...
... application. A program or set of programs that performs a task; some examples are payroll, inventory management, and word processing applications. application layer. In the Open Systems Interconnection (OSI) reference model, the layer that provides means for application processes residing in open sy ...
Ch1_Introduction
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
PPT Version
... 5. If the octets starting with T are 0x0001 (an indication of authentication data), T= T+13 plus the lengths of the client identifier and the authentication value, assuming T is the start of authentication data. 6. If E-T < 40, the packet is not Teredo. 7. If the octets starting with T are 0x0000 (a ...
... 5. If the octets starting with T are 0x0001 (an indication of authentication data), T= T+13 plus the lengths of the client identifier and the authentication value, assuming T is the start of authentication data. 6. If E-T < 40, the packet is not Teredo. 7. If the octets starting with T are 0x0000 (a ...
NetVM: High Performance and Flexible Networking Using
... businesses run network services on existing cloud platforms, bringing multiplexing and economy of scale benefits to network functionality. Once data can be moved to, from and between VMs at line rate for all packet sizes, we approach the long-term vision where the line between data centers and netwo ...
... businesses run network services on existing cloud platforms, bringing multiplexing and economy of scale benefits to network functionality. Once data can be moved to, from and between VMs at line rate for all packet sizes, we approach the long-term vision where the line between data centers and netwo ...
ROVANIEMI UNIVERSITY OF APPLIED SCIENCES SCHOOL OF TECHNOLOGY
... input cost and raise competitive ability. For these reasons, the two popular telecommunication technologies Voice over Internet Protocol (VoIP) and Voice over Asynchronous Transfer Mode (VoATM) compete with each other at present. By using advantages of both capital and technique, VMS is cable of lau ...
... input cost and raise competitive ability. For these reasons, the two popular telecommunication technologies Voice over Internet Protocol (VoIP) and Voice over Asynchronous Transfer Mode (VoATM) compete with each other at present. By using advantages of both capital and technique, VMS is cable of lau ...
ARP Spoofing and Man in the Middle attack
... MAC address (i.e., the address of the network card) to one that the attacker can monitor. Because the ARP replies have been forged, the target computer sends frames that were meant for the original destination to the attacker’s computer first so the frames can be read. A successful ARP attempt is in ...
... MAC address (i.e., the address of the network card) to one that the attacker can monitor. Because the ARP replies have been forged, the target computer sends frames that were meant for the original destination to the attacker’s computer first so the frames can be read. A successful ARP attempt is in ...
CH3-MPLS-Multiprotocol
... network protocol. It was originally developed in the late 1990s to provide faster packet forwarding for IP routers (see RFC 3031). Since then its capabilities have expanded massively, for example to support service creation (VPNs), traffic engineering, network convergence, and increased resiliency. ...
... network protocol. It was originally developed in the late 1990s to provide faster packet forwarding for IP routers (see RFC 3031). Since then its capabilities have expanded massively, for example to support service creation (VPNs), traffic engineering, network convergence, and increased resiliency. ...
Physical Topologies (cont.)
... populated segments that can be used on any 10 Mbps Ethernet network. (see Fig. 4-3) ...
... populated segments that can be used on any 10 Mbps Ethernet network. (see Fig. 4-3) ...
Model: IK-WB01A IK-WB11A
... B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not installed and used in accordance with the i ...
... B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not installed and used in accordance with the i ...