HotView Pro™ Mesh Management Software
... internetworking, and more. The software’s MultiMesh™ capability enables an authorized administrator to manage multiple mesh networks from a single screen. These networks can be independent, or integrated with MeshBridge™ to form a single mesh environment with up to 1000 nodes. Real-time monitoring d ...
... internetworking, and more. The software’s MultiMesh™ capability enables an authorized administrator to manage multiple mesh networks from a single screen. These networks can be independent, or integrated with MeshBridge™ to form a single mesh environment with up to 1000 nodes. Real-time monitoring d ...
Embedded Solutions
... share the health and status of wireless links. As a result, the router finds out within milliseconds when new network nodes arrive or depart. It uses this information as it continually looks for a lower cost or higher quality link. During the transition to a new wireless link, voice, video, and data ...
... share the health and status of wireless links. As a result, the router finds out within milliseconds when new network nodes arrive or depart. It uses this information as it continually looks for a lower cost or higher quality link. During the transition to a new wireless link, voice, video, and data ...
Designing AirPort Extreme Networks
... You can separate your wireless network from the outside world with firewall protection. The AirPort Extreme Base Station has a built-in firewall that creates a barrier between your network and the Internet, protecting data from Internet-based IP attacks. The firewall is automatically turned on when ...
... You can separate your wireless network from the outside world with firewall protection. The AirPort Extreme Base Station has a built-in firewall that creates a barrier between your network and the Internet, protecting data from Internet-based IP attacks. The firewall is automatically turned on when ...
paper
... from which it explores vertices 5 and 6. Vertex 6 is also leaf of the DFS tree. The DFS returns to vertex 5, then 2, and, finally, to vertex 1. The collection route is thus (1, 2, 3, 4, 3, 2, 5, 6, 5, 2, 1), and appears in the figure with thin lines. The collection route defines a walk that traverse ...
... from which it explores vertices 5 and 6. Vertex 6 is also leaf of the DFS tree. The DFS returns to vertex 5, then 2, and, finally, to vertex 1. The collection route is thus (1, 2, 3, 4, 3, 2, 5, 6, 5, 2, 1), and appears in the figure with thin lines. The collection route defines a walk that traverse ...
Slides
... use existing telephone line to central office DSLAM data over DSL phone line goes to Internet voice over DSL phone line goes to telephone net < 2.5 Mbps upstream transmission rate (typically < 1 Mbps) < 24 Mbps downstream transmission rate (typically < 10 Mbps) Introduction 1-13 ...
... use existing telephone line to central office DSLAM data over DSL phone line goes to Internet voice over DSL phone line goes to telephone net < 2.5 Mbps upstream transmission rate (typically < 1 Mbps) < 24 Mbps downstream transmission rate (typically < 10 Mbps) Introduction 1-13 ...
3 What is MMS? - ECO Documentation Database
... between mobiles, where the recipient is addressed by their E.164 number between mobiles and other messaging systems such as email, where the recipient is addressed by their email address. The choice of identifier for the recipient (eg E.164 number or email address) determines the method of deliv ...
... between mobiles, where the recipient is addressed by their E.164 number between mobiles and other messaging systems such as email, where the recipient is addressed by their email address. The choice of identifier for the recipient (eg E.164 number or email address) determines the method of deliv ...
4th Edition: Chapter 1
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
4th Edition: Chapter 1
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
Networking Support For Mobile Computing
... stationary users, each user has a fixed address that is used to transfer information to them. Information is transferred by a process called routing, where a route is found to the user for information transfer. Many network protocols are optimized for a wired medium rather than a wireless medium. Th ...
... stationary users, each user has a fixed address that is used to transfer information to them. Information is transferred by a process called routing, where a route is found to the user for information transfer. Many network protocols are optimized for a wired medium rather than a wireless medium. Th ...
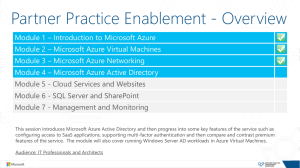
Azure AD
... Support development’s need to build secure directory integrated applications for the enterprise. ...
... Support development’s need to build secure directory integrated applications for the enterprise. ...
4th Edition: Chapter 1
... use existing telephone line to central office DSLAM data over DSL phone line goes to Internet voice over DSL phone line goes to telephone net < 2.5 Mbps upstream transmission rate (typically < 1 Mbps) < 24 Mbps downstream transmission rate (typically < 10 Mbps) Introduction 1-13 ...
... use existing telephone line to central office DSLAM data over DSL phone line goes to Internet voice over DSL phone line goes to telephone net < 2.5 Mbps upstream transmission rate (typically < 1 Mbps) < 24 Mbps downstream transmission rate (typically < 10 Mbps) Introduction 1-13 ...
Compensation of Asymmetrical Latency for Ethernet Clock
... measured within the system if all the available communication links are not mandatory symmetric. Algorithmic approaches like the ones presented in [9] are not feasible. In their particular approach the master must know the asymmetry and adjust its inter-packet gap exactly to this value. In practice, ...
... measured within the system if all the available communication links are not mandatory symmetric. Algorithmic approaches like the ones presented in [9] are not feasible. In their particular approach the master must know the asymmetry and adjust its inter-packet gap exactly to this value. In practice, ...
Chapter 7
... session initialization how does callee advertise its IP address, port number, encoding algorithms? Multimedia Networking ...
... session initialization how does callee advertise its IP address, port number, encoding algorithms? Multimedia Networking ...
Understanding Firewall Basics
... for instructions” printed on both sides. He’s not going to fall for that. Letting the second and subsequent fragments pass the firewall may be the solution, but this strategy also has a disadvantage. The first fragment can be inspected and is possibly blocked. The final-destination computer on the i ...
... for instructions” printed on both sides. He’s not going to fall for that. Letting the second and subsequent fragments pass the firewall may be the solution, but this strategy also has a disadvantage. The first fragment can be inspected and is possibly blocked. The final-destination computer on the i ...
The Second Internet
... This book is published under a Creative Commons License, which can be referenced at http://creativecommons.org/licenses/by-nd/3.0/us/. In short, the terms of this license are as follows: You can share (copy, distribute and/or transmit) machine readable copies of this work. At most there should be mi ...
... This book is published under a Creative Commons License, which can be referenced at http://creativecommons.org/licenses/by-nd/3.0/us/. In short, the terms of this license are as follows: You can share (copy, distribute and/or transmit) machine readable copies of this work. At most there should be mi ...
network
... use existing telephone line to central office DSLAM data over DSL phone line goes to Internet voice over DSL phone line goes to telephone net < 2.5 Mbps upstream transmission rate (typically < 1 Mbps) < 24 Mbps downstream transmission rate (typically < 10 Mbps) Introduction 1-13 ...
... use existing telephone line to central office DSLAM data over DSL phone line goes to Internet voice over DSL phone line goes to telephone net < 2.5 Mbps upstream transmission rate (typically < 1 Mbps) < 24 Mbps downstream transmission rate (typically < 10 Mbps) Introduction 1-13 ...
Integrating Cisco Press Resources into the Academy Classroom
... meters; 10BASE2 to a little less than 200 meters (185 meters) – hence their names (the 5 and the 2; the 10 is for 10Mbps) • To extend the distance of LANs, repeaters were ...
... meters; 10BASE2 to a little less than 200 meters (185 meters) – hence their names (the 5 and the 2; the 10 is for 10Mbps) • To extend the distance of LANs, repeaters were ...
Slide 1
... usually provided in an XML document called a Web Services Description Language (WSDL) document. – XML Web services are registered so that potential users can find them easily. This is done with Universal Discovery Description and Integration (UDDI). ...
... usually provided in an XML document called a Web Services Description Language (WSDL) document. – XML Web services are registered so that potential users can find them easily. This is done with Universal Discovery Description and Integration (UDDI). ...
GPSMAP® 800 and 1000 Series Installation Instructions
... Marine Network devices such as a GPSMAP 8000 series device. • This device is not compatible with legacy Garmin sounder modules such as the GSD™ 26. • If your device receives sonar data from a transducer connected to the SONAR port, it does not share the sonar data with other ETHERNET devices. • A ...
... Marine Network devices such as a GPSMAP 8000 series device. • This device is not compatible with legacy Garmin sounder modules such as the GSD™ 26. • If your device receives sonar data from a transducer connected to the SONAR port, it does not share the sonar data with other ETHERNET devices. • A ...
Re-ECN - Bob Briscoe
... manage evolution of new congestion control, even for liberal → conservative flows nets that allow their users to cause congestion in other nets, can be held accountable ...
... manage evolution of new congestion control, even for liberal → conservative flows nets that allow their users to cause congestion in other nets, can be held accountable ...
The TOPS Architecture for Signaling, Directory Services and Transport for Packet Telephony
... resolution query is handled. Users can customize access to their information. The directory service also helps callers by providing them with a flexible set of call appearances and options. Compared to existing telephony features such as “personal phone numbers” and “intelligent 800-number” services ...
... resolution query is handled. Users can customize access to their information. The directory service also helps callers by providing them with a flexible set of call appearances and options. Compared to existing telephony features such as “personal phone numbers” and “intelligent 800-number” services ...
32501-900
... The present document describes the concepts how self-configuration works and what IRP requirements need to be met to support this functionality. The document also captures if a requirement shall be met via the Itf-N interface or via other protocols. This version of the TS is restricted to self-confi ...
... The present document describes the concepts how self-configuration works and what IRP requirements need to be met to support this functionality. The document also captures if a requirement shall be met via the Itf-N interface or via other protocols. This version of the TS is restricted to self-confi ...
Linux_VPN - Goecke
... Virtual Private Network (VPN) The use of encryption in the lower protocol layers to provide a secure connection through an otherwise insecure network, typically the Internet. VPNs are generally cheaper than real private networks using private lines but rely on having the same encryption system at bo ...
... Virtual Private Network (VPN) The use of encryption in the lower protocol layers to provide a secure connection through an otherwise insecure network, typically the Internet. VPNs are generally cheaper than real private networks using private lines but rely on having the same encryption system at bo ...
end of section
... The Hardware Virtual Private Network (VPN) units shall be KBC Networks models THLK-S2-WB (ThruLink, Standard Capacity, Standalone operation) THLK-S3-WB (ThruLink Standard Capacity, Standalone operation) and THLK-H2-RB (ThruLink, High Capacity, Rack Mount operation). The units shall be either standal ...
... The Hardware Virtual Private Network (VPN) units shall be KBC Networks models THLK-S2-WB (ThruLink, Standard Capacity, Standalone operation) THLK-S3-WB (ThruLink Standard Capacity, Standalone operation) and THLK-H2-RB (ThruLink, High Capacity, Rack Mount operation). The units shall be either standal ...
Evolution of P2P file sharing
... P2P system without any central point of control decentralized and autonomous, robust and hard to shut down the latter one was extremely important ...
... P2P system without any central point of control decentralized and autonomous, robust and hard to shut down the latter one was extremely important ...