CS591
... Once we steal a legitimate ARP request, there’s absolutely nothing to keep us from spoofing our BSSID and retransmitting the exact same request as many times as we want. • We don’t know the values of the encrypted bytes we’re transmitting, but that’s ok. We don’t care. • We also won’t be able to rea ...
... Once we steal a legitimate ARP request, there’s absolutely nothing to keep us from spoofing our BSSID and retransmitting the exact same request as many times as we want. • We don’t know the values of the encrypted bytes we’re transmitting, but that’s ok. We don’t care. • We also won’t be able to rea ...
ppt1
... "Hagelslag is an implementation of GNUtella. The main goals for this implementation are flexibility, stability and performance. The development of Hagelslag was primarily aimed at i386 machines running Linux, as of version 0.8, FreeBSD is supported as well." /7 ...
... "Hagelslag is an implementation of GNUtella. The main goals for this implementation are flexibility, stability and performance. The development of Hagelslag was primarily aimed at i386 machines running Linux, as of version 0.8, FreeBSD is supported as well." /7 ...
Managing Routing Disruptions in Internet Service Provider Networks
... the new route is different; hence C must send a BGP update to its customer to report the change. Besides the impact of the egress change, this event may impact the upstream path. Sending BGP updates to neighbors may have unpredictable effects, because it may impact whether or where the neighbor choo ...
... the new route is different; hence C must send a BGP update to its customer to report the change. Besides the impact of the egress change, this event may impact the upstream path. Sending BGP updates to neighbors may have unpredictable effects, because it may impact whether or where the neighbor choo ...
Lecture06: IP Security
... Provide secure network access over the Internet An end-user whose system is equipped with IPSec can make a local call to ISP and gain secure access to her/his company Provide secure communications between organisations by ensuring authentication and confidentiality IPSec can be used to creat ...
... Provide secure network access over the Internet An end-user whose system is equipped with IPSec can make a local call to ISP and gain secure access to her/his company Provide secure communications between organisations by ensuring authentication and confidentiality IPSec can be used to creat ...
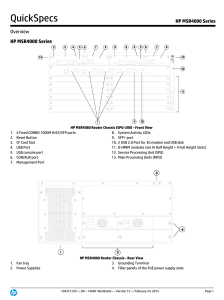
HP MSR4000 Series
... (SVCs), Martini draft, and Kompella-draft technologies Routing policy allows custom filters for increased performance and security; supports ACLs, IP prefix, AS paths, community lists, and aggregate policies ...
... (SVCs), Martini draft, and Kompella-draft technologies Routing policy allows custom filters for increased performance and security; supports ACLs, IP prefix, AS paths, community lists, and aggregate policies ...
Veroxity VPLS-Based Network Delivers High Availability Challenge EXECUTIVE SUMMARY
... interfaces, freeing up IT resources and bringing increased productivity to the enterprise. Historically there has been a large demand for traditional time-division ...
... interfaces, freeing up IT resources and bringing increased productivity to the enterprise. Historically there has been a large demand for traditional time-division ...
Implementation of IXP200 Network Processor Packet Filtering
... • 32-bit SRAM unit supporting upto 8 MB • 64-bit SDRAM unit supporting upto 256 MB • 8 KB of 32-bit Scratchpad Memory Shyamal Pandya ...
... • 32-bit SRAM unit supporting upto 8 MB • 64-bit SDRAM unit supporting upto 256 MB • 8 KB of 32-bit Scratchpad Memory Shyamal Pandya ...
Cisco 1 - Network Specialist Program
... c) When the command has finished execution, stop your Wireshark capture (Click Capture > Stop) and close the terminal window. Step 3: Analyze the Wireshark capture. The first thing you may notice is that a lot of extra packets were captured by Wireshark; you will likely have many more packets in the ...
... c) When the command has finished execution, stop your Wireshark capture (Click Capture > Stop) and close the terminal window. Step 3: Analyze the Wireshark capture. The first thing you may notice is that a lot of extra packets were captured by Wireshark; you will likely have many more packets in the ...
Traffic Engineering in IP over Optical Area Environments
... Figure 2: Evolution path towards data-optimized networks............................................................................... 3 Figure 3: Weekly incoming/outgoing traffic from the Catalan R&A Network, November 2004, 8-15 ........... 12 Figure 4: Weekly incoming/outgoing traffic from the Ca ...
... Figure 2: Evolution path towards data-optimized networks............................................................................... 3 Figure 3: Weekly incoming/outgoing traffic from the Catalan R&A Network, November 2004, 8-15 ........... 12 Figure 4: Weekly incoming/outgoing traffic from the Ca ...
THE TCP/IP PROTOCOL SUITE
... and necessary parameters for the lower layer to carry out the task. Layers on the same system provide and obtain services to and from adjacent layers. However, a peer-to-peer protocol process allows the same layers on different systems to communicate. The term peer means every implementation of some ...
... and necessary parameters for the lower layer to carry out the task. Layers on the same system provide and obtain services to and from adjacent layers. However, a peer-to-peer protocol process allows the same layers on different systems to communicate. The term peer means every implementation of some ...
TR 0006 - oneM2M
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
chapter5_1
... Deliver messages in the same order they are sent Deliver at most one copy of each message Support arbitrarily large messages Support synchronization Allow the receiver to flow control the sender Support multiple application processes on each host ...
... Deliver messages in the same order they are sent Deliver at most one copy of each message Support arbitrarily large messages Support synchronization Allow the receiver to flow control the sender Support multiple application processes on each host ...
Alberto Santoro: Digital Divide Executive Report Outline to the ICFA
... The impact of solving the Digital Divide problem extends even beyond the bounds of the research community. In the twentieth century at least three basic infrastructures were needed for a modern city to be viable: Pervasive water distribution, drainage distribution, and electricity distribution throu ...
... The impact of solving the Digital Divide problem extends even beyond the bounds of the research community. In the twentieth century at least three basic infrastructures were needed for a modern city to be viable: Pervasive water distribution, drainage distribution, and electricity distribution throu ...
20061004-IMSP2P
... • Services are available on the edge, can spread virally • Internet is an “eat all you can” model based on flat fees • New applications are rolled out faster then ever • Free services attract naturally large amount of users to premium services ...
... • Services are available on the edge, can spread virally • Internet is an “eat all you can” model based on flat fees • New applications are rolled out faster then ever • Free services attract naturally large amount of users to premium services ...
Chapter 1
... • Used to connect routers to external networks, usually over a larger geographical distance. • The Layer 2 encapsulation can be different types (PPP, Frame Relay, HDLC (High-Level Data Link Control) ). • Similar to LAN interfaces, each WAN interface has its own IP address and subnet mask, making it ...
... • Used to connect routers to external networks, usually over a larger geographical distance. • The Layer 2 encapsulation can be different types (PPP, Frame Relay, HDLC (High-Level Data Link Control) ). • Similar to LAN interfaces, each WAN interface has its own IP address and subnet mask, making it ...
Exploration_LAN_Switching_Chapter5
... Layer 2 Loops When multiple paths exist between two devices on the network and STP has been disabled on those switches, a Layer 2 loop can occur. Ethernet frames do not have a time to live (TTL) like IP packets traversing routers. If they are not terminated properly on a switched network, th ...
... Layer 2 Loops When multiple paths exist between two devices on the network and STP has been disabled on those switches, a Layer 2 loop can occur. Ethernet frames do not have a time to live (TTL) like IP packets traversing routers. If they are not terminated properly on a switched network, th ...
TCP/IP Refresher
... An organization can subdivide it’s host address space into groups called subnets. The subnet ID is generally used to group hosts based on the physical network topology. It is possible to have a single wire network with multiple subnets. ...
... An organization can subdivide it’s host address space into groups called subnets. The subnet ID is generally used to group hosts based on the physical network topology. It is possible to have a single wire network with multiple subnets. ...
Network Operating System Evolution
... difference made by the choice of OS. It is still not uncommon to find routers or switches that started life under older, monolithic software and later migrated to more contemporary designs. The positive effect on stability and operational efficiency is easy to notice and appreciate. However, migrati ...
... difference made by the choice of OS. It is still not uncommon to find routers or switches that started life under older, monolithic software and later migrated to more contemporary designs. The positive effect on stability and operational efficiency is easy to notice and appreciate. However, migrati ...
DSU / CSU NETWORK DESIGN LAB INTRODUCTION
... show commands. As you will see later, these are very useful in troubleshooting a routing problem. Configuration changes must be made at enable level; they will not work at user level. The enable level allows you to actually change the configuration settings on the router, including set-up of interfa ...
... show commands. As you will see later, these are very useful in troubleshooting a routing problem. Configuration changes must be made at enable level; they will not work at user level. The enable level allows you to actually change the configuration settings on the router, including set-up of interfa ...
Snort - an network intrusion prevention and detection system
... malicious activity such as denial of service attacks, port scans or even attempts to crack into computers by monitoring network traffic. ...
... malicious activity such as denial of service attacks, port scans or even attempts to crack into computers by monitoring network traffic. ...
PowerPoint - DePaul University
... time, but when they don't, failures are generally catastrophic ...
... time, but when they don't, failures are generally catastrophic ...
A Proxy For All Your Semantic Needs Vladislav D. Veksler Alex Grintsvayg
... be redesigned if a need for using a new MSR arises. Second, it is not uncommon for researchers to compare various MSRs (e.g. Kaur & Hornof, 2005). Third, MSRs can be used in complement with each other. We are currently exploring the possibility that average MSR scores may actually be more accurate t ...
... be redesigned if a need for using a new MSR arises. Second, it is not uncommon for researchers to compare various MSRs (e.g. Kaur & Hornof, 2005). Third, MSRs can be used in complement with each other. We are currently exploring the possibility that average MSR scores may actually be more accurate t ...
Workgroup Systems
... Internet-enabled fax machines plug into your existing data network. They convert scanned documents into file formats that are easily transported over the Internet or your company intranet, sending data to e-mail address destinations or other I-fax-capable machines. Internet faxing bypasses the publi ...
... Internet-enabled fax machines plug into your existing data network. They convert scanned documents into file formats that are easily transported over the Internet or your company intranet, sending data to e-mail address destinations or other I-fax-capable machines. Internet faxing bypasses the publi ...
N51 , N52 EFM SHDSL.bis Modem User`s Manual V1.2
... You can view statistics regarding the processed packets that are transmitted and received through an interface. You will not typically need to view this data, but you may find it helpful when working with Your ISP when diagnosing network problems. The following table describes each type of interface ...
... You can view statistics regarding the processed packets that are transmitted and received through an interface. You will not typically need to view this data, but you may find it helpful when working with Your ISP when diagnosing network problems. The following table describes each type of interface ...