Internet Study 2008/2009
... For the third year in a row, after 2006 and 2007, ipoque has conducted a comprehensive study measuring and analyzing Internet traffic in eight regions of the world. The study includes statistical data about popularity and user behavior for all common network protocols. This covers most applications ...
... For the third year in a row, after 2006 and 2007, ipoque has conducted a comprehensive study measuring and analyzing Internet traffic in eight regions of the world. The study includes statistical data about popularity and user behavior for all common network protocols. This covers most applications ...
PowerPoint - Surendar Chandra
... • Therefore, the sender must maintain normal TCP timeouts. A segment cannot be considered received until an ACK is received for it. The sender must retransmit the segment at the left window edge after a retransmit timeout, even if the SACK bit is on for that segment. • A segment cannot be removed fr ...
... • Therefore, the sender must maintain normal TCP timeouts. A segment cannot be considered received until an ACK is received for it. The sender must retransmit the segment at the left window edge after a retransmit timeout, even if the SACK bit is on for that segment. • A segment cannot be removed fr ...
Accurate Real-time Identification of IP Prefix
... Another way to avoid MOAS conflicts is to announce a subnet of an existing prefix. For example, an attacker may hijack 129.222.32.0/19 given the existence of 129.222.0.0/16 in the routing table. If there are no other advertisements for this prefix and no filtering for this route, the route is likely ...
... Another way to avoid MOAS conflicts is to announce a subnet of an existing prefix. For example, an attacker may hijack 129.222.32.0/19 given the existence of 129.222.0.0/16 in the routing table. If there are no other advertisements for this prefix and no filtering for this route, the route is likely ...
Computer Networking Tutorial - ECE, Rutgers
... An important attribute of a communication link is how many bitstreams can be transmitted on it at the same time. If a link allows transmitting only a single bitstream at a time, then the nodes connected to the link must coordinate their transmissions to avoid data collisions. Such links are known as ...
... An important attribute of a communication link is how many bitstreams can be transmitted on it at the same time. If a link allows transmitting only a single bitstream at a time, then the nodes connected to the link must coordinate their transmissions to avoid data collisions. Such links are known as ...
Chap 11 Routing
... router uses the network portion of the address to make path selections The switching function: accept a packet on one interface and forward it through a second interface ...
... router uses the network portion of the address to make path selections The switching function: accept a packet on one interface and forward it through a second interface ...
Network Layer
... reason not to put the complexity in the hosts. 2. The subnet is a major international investment that will last for decades, so it should not be cluttered up with features that may become obsolete quickly. 3. Some applications, such as digitized voice and real-time data collection may regard speedy ...
... reason not to put the complexity in the hosts. 2. The subnet is a major international investment that will last for decades, so it should not be cluttered up with features that may become obsolete quickly. 3. Some applications, such as digitized voice and real-time data collection may regard speedy ...
Dante Troubleshooting FAQ
... Firmware updates are handled through device manufacturers. Please contact the device manufacturer’s technical support department for additional information regarding your particular products. ...
... Firmware updates are handled through device manufacturers. Please contact the device manufacturer’s technical support department for additional information regarding your particular products. ...
CS610 Final term MAGA file.. all paperz are in 1 file
... NEXT HEADER field in the base header defines type of header and it appears at end of fixed-size base header. ► True ► False Question No: 21 ( Marks: 1 ) - Please choose one Although message exchange can be used to bind addresses, sending a request for each binding is hopelessly inefficient. ► True ► ...
... NEXT HEADER field in the base header defines type of header and it appears at end of fixed-size base header. ► True ► False Question No: 21 ( Marks: 1 ) - Please choose one Although message exchange can be used to bind addresses, sending a request for each binding is hopelessly inefficient. ► True ► ...
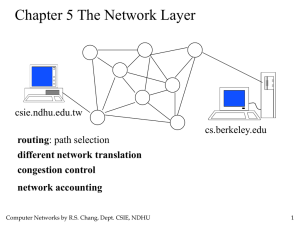
3rd Edition, Chapter 5
... 802.3 Ethernet Standards: Link & Physical Layers many different Ethernet standards common MAC protocol and frame format different speeds: 2 Mbps, 10 Mbps, 100 Mbps, ...
... 802.3 Ethernet Standards: Link & Physical Layers many different Ethernet standards common MAC protocol and frame format different speeds: 2 Mbps, 10 Mbps, 100 Mbps, ...
4 Measuring Network Delay
... approximately how many router hops the packet has gone through. Let us imagine the TTL is set to 255. In this situation it is 255 minus N hops, where N is the TTL of the returning Echo Replies. If the TTL field varies in successive pings, it could indicate that the successive reply packets are going ...
... approximately how many router hops the packet has gone through. Let us imagine the TTL is set to 255. In this situation it is 255 minus N hops, where N is the TTL of the returning Echo Replies. If the TTL field varies in successive pings, it could indicate that the successive reply packets are going ...
An Overview on Ad Hoc Networks
... with supported infrastructure. Each infrastructure establishes a cell and every node in the cell can be reached by the infrastructure. So the node can send a packet to another node in the cell via infrastructure and without single- or multi-hop. If the destination node is in another cell, the infras ...
... with supported infrastructure. Each infrastructure establishes a cell and every node in the cell can be reached by the infrastructure. So the node can send a packet to another node in the cell via infrastructure and without single- or multi-hop. If the destination node is in another cell, the infras ...
Intel®10 Gigabit AF DA Dual Port Server Adapter
... (IPv4, IPv6) capabilities control protocol (TCP), user datagram protocol (UDP), Internet protocol (IP) ...
... (IPv4, IPv6) capabilities control protocol (TCP), user datagram protocol (UDP), Internet protocol (IP) ...
20100609-Tier3WS
... • All measurements (Netflow, SNMP, throughput, latency) are available or may be requested • Greatly simplifies requests to assist with performance problems ...
... • All measurements (Netflow, SNMP, throughput, latency) are available or may be requested • Greatly simplifies requests to assist with performance problems ...
Installation Guide Session Monitor Suite Release 3.3.0
... The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. ...
... The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. ...
Lecture 2
... • TCP provides these features (services), while UDP does not 3. Network layer (could be called the routing layer, but it isn’t) • The packets must find their way through the network. • Each packet has the IP address of the destination • By examining the IP address, routers decide where to send the p ...
... • TCP provides these features (services), while UDP does not 3. Network layer (could be called the routing layer, but it isn’t) • The packets must find their way through the network. • Each packet has the IP address of the destination • By examining the IP address, routers decide where to send the p ...
Self-organizing Name Resolution System for ICN
... Symphony[21]. It takes advantage of the idea of small world[22] which constructs a “small” distance topology using small number of links. For instance, when the number of nodes and network distance are given as conditions, Symphony can construct a topology which satisfies the conditions using only h ...
... Symphony[21]. It takes advantage of the idea of small world[22] which constructs a “small” distance topology using small number of links. For instance, when the number of nodes and network distance are given as conditions, Symphony can construct a topology which satisfies the conditions using only h ...
Immersive Media Delivery and Access Grid
... o Reliable networking of real-time media with reliable transport via ARQ, FEC, and their hybrid o Versatile display of stereo video in Left, Interlaced, Left & Right, and Above & Below views. ...
... o Reliable networking of real-time media with reliable transport via ARQ, FEC, and their hybrid o Versatile display of stereo video in Left, Interlaced, Left & Right, and Above & Below views. ...
NGN Architecture and main Elements
... provides the “service delivery control” within the network in charge of Call Control and handling of Media Gateways control (Access and/or Trunking) via H.248 protocol performs signalling gateway functionality or uses a signalling gateway for interworking with PSTN N7 signalling network provides con ...
... provides the “service delivery control” within the network in charge of Call Control and handling of Media Gateways control (Access and/or Trunking) via H.248 protocol performs signalling gateway functionality or uses a signalling gateway for interworking with PSTN N7 signalling network provides con ...
show ip route eigrp - Armstrong State University
... – Can be overridden by a loopback interface: Highest IP address of any active loopback interface – also called a logical interface ...
... – Can be overridden by a loopback interface: Highest IP address of any active loopback interface – also called a logical interface ...
Chapter 7: EIGRP
... – Can be overridden by a loopback interface: Highest IP address of any active loopback interface – also called a logical interface ...
... – Can be overridden by a loopback interface: Highest IP address of any active loopback interface – also called a logical interface ...
TeamSpeak 3 And Broadband
... TeamSpeak 3 provides this functionality, as well as lots of others, on IP based networks. ...
... TeamSpeak 3 provides this functionality, as well as lots of others, on IP based networks. ...
4th Edition: Chapter 1 - Simon Fraser University
... use existing telephone line to central office DSLAM data over DSL phone line goes to Internet voice over DSL phone line goes to telephone net < 2.5 Mbps upstream transmission rate (typically < 1 Mbps) < 24 Mbps downstream transmission rate (typically < 10 Mbps) Introduction 1-17 ...
... use existing telephone line to central office DSLAM data over DSL phone line goes to Internet voice over DSL phone line goes to telephone net < 2.5 Mbps upstream transmission rate (typically < 1 Mbps) < 24 Mbps downstream transmission rate (typically < 10 Mbps) Introduction 1-17 ...
Protection in General-Purpose Operating Systems
... CHAP Authentication The CHAP algorithm requires that the length of the secret MUST be at least 1 octet. The secret SHOULD be at least as large and unguessable as a well-chosen password. It is preferred that the secret be at least the length of the hash value for the hashing algorithm chosen (16 o ...
... CHAP Authentication The CHAP algorithm requires that the length of the secret MUST be at least 1 octet. The secret SHOULD be at least as large and unguessable as a well-chosen password. It is preferred that the secret be at least the length of the hash value for the hashing algorithm chosen (16 o ...