homework - Kendriya Vidyalaya Dhanpuri
... Hub: Hub is a device used to connect several computers together. It is a multi-port card. Hubs forward any data packets including e-mail, word processing documents or print request – they receive over one port from one workstation to all of their remaining ports Switches : Switches are smart hubs th ...
... Hub: Hub is a device used to connect several computers together. It is a multi-port card. Hubs forward any data packets including e-mail, word processing documents or print request – they receive over one port from one workstation to all of their remaining ports Switches : Switches are smart hubs th ...
Internetworking - University of Maine System
... In another light, internetworking is the glue behind the Internet. ...
... In another light, internetworking is the glue behind the Internet. ...
photo.net Introduction - ADUni.org: ArsDigita University
... Each server registers a service and a version Service - typically implemented as an integer; a set of well-known services exist Version - a number used to select which server to use Who decides which server to return to the client? Key issue: Load Balancing ...
... Each server registers a service and a version Service - typically implemented as an integer; a set of well-known services exist Version - a number used to select which server to use Who decides which server to return to the client? Key issue: Load Balancing ...
UNIX for Programmers and Users
... along with a destination address; Only the Ethernet card whose address matches the destination address accepts the message. ...
... along with a destination address; Only the Ethernet card whose address matches the destination address accepts the message. ...
The Infrastructure Technologies
... Agent process on client Network client’s link to network operating system Network Examples Novell NetWare Windows Server 2000, 2003, NT Server Peer to Peer Networks NOS is installed on each attached workstation Runs on top of the local operating system ...
... Agent process on client Network client’s link to network operating system Network Examples Novell NetWare Windows Server 2000, 2003, NT Server Peer to Peer Networks NOS is installed on each attached workstation Runs on top of the local operating system ...
Chapter 5 : The Internet: Addressing & Services
... – Routers can’t keep track of every network path ...
... – Routers can’t keep track of every network path ...
Policy Development Worksheet
... The rationale or purpose statement expresses “why” the policy is being written. The rationale or purpose may also contain or cross-reference “background” materials or more explanatory details regarding legal, regulatory, or other factors that led to the development of the policy. ...
... The rationale or purpose statement expresses “why” the policy is being written. The rationale or purpose may also contain or cross-reference “background” materials or more explanatory details regarding legal, regulatory, or other factors that led to the development of the policy. ...
Slides
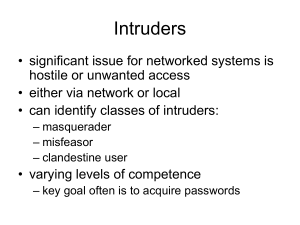
... • viral attacks exploit lack of integrity control on systems • to defend need to add such controls • typically by one or more of: – prevention - block virus infection mechanism – detection - of viruses in infected system – reaction - restoring system to clean state ...
... • viral attacks exploit lack of integrity control on systems • to defend need to add such controls • typically by one or more of: – prevention - block virus infection mechanism – detection - of viruses in infected system – reaction - restoring system to clean state ...
Connected Devices Interfacing (CDI)
... services the means to optimally exploit the network capabilities, by means of the implementation of APIs towards networking elements NetIC will provide an abstraction of the physical network resources, as well as the capability to control them (up to certain limitations given by the physical resour ...
... services the means to optimally exploit the network capabilities, by means of the implementation of APIs towards networking elements NetIC will provide an abstraction of the physical network resources, as well as the capability to control them (up to certain limitations given by the physical resour ...
attacks
... occurs when more data is sent to a buffer than it can handle AND the programmer did not specify what happens in that special case ...
... occurs when more data is sent to a buffer than it can handle AND the programmer did not specify what happens in that special case ...
Network Protocols
... Instead of sharing a common network medium, all nodes in the network can be connected directly to a router/switch ...
... Instead of sharing a common network medium, all nodes in the network can be connected directly to a router/switch ...
NETWORKING I
... Protocols Protocols generally do not describe how to accomplish a particular function. By describing only what functions are required of a particular communication rule but not how they are to be carried out, the implementation of a particular protocol can be technology-independent. ...
... Protocols Protocols generally do not describe how to accomplish a particular function. By describing only what functions are required of a particular communication rule but not how they are to be carried out, the implementation of a particular protocol can be technology-independent. ...
Network Planning Technical Sub
... DNSOne for entering DNS records for the Medical School while continuing to use their existing DHCP servers and will contact ITSS to get started. Network updates Barry – There is still a shortage of available IP addresses at the Medical School. Setting shorter lease times has helped to get by, but th ...
... DNSOne for entering DNS records for the Medical School while continuing to use their existing DHCP servers and will contact ITSS to get started. Network updates Barry – There is still a shortage of available IP addresses at the Medical School. Setting shorter lease times has helped to get by, but th ...
Reference Models - UT School of Information
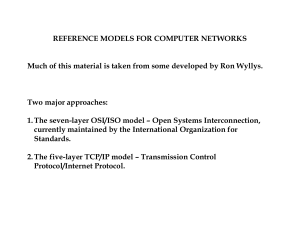
... 4. Transport layer – deals with data transfer between end systems and determines flow control. 5. Session layer – creates and manages sessions when one application process requests access to another applications process, e.g., MSWord importing a spread sheet from Excel. 6. Presentation layer – dete ...
... 4. Transport layer – deals with data transfer between end systems and determines flow control. 5. Session layer – creates and manages sessions when one application process requests access to another applications process, e.g., MSWord importing a spread sheet from Excel. 6. Presentation layer – dete ...
Top 100 Network Security Tools
... • Ping/telnet/dig/traceroute/whois/netstat : While there are many whiz-bang high-tech tools out there to assist in security auditing, don't forget about the basics! Everyone should be very familiar with these tools as they come with most operating systems (except that Windows omits whois and uses th ...
... • Ping/telnet/dig/traceroute/whois/netstat : While there are many whiz-bang high-tech tools out there to assist in security auditing, don't forget about the basics! Everyone should be very familiar with these tools as they come with most operating systems (except that Windows omits whois and uses th ...
CISSP – Chapter 7 - Paladin Group, LLC
... Transport/Host to Host = OSI layer 4, 5 – defines a communication session between two applications on one or two hosts Application = OSI layers 6,7 the application data that is being sent across a network ...
... Transport/Host to Host = OSI layer 4, 5 – defines a communication session between two applications on one or two hosts Application = OSI layers 6,7 the application data that is being sent across a network ...
Lecture 3a
... What is the Internet? • A network of networks, joining many government, university and private computers together and providing an infrastructure for the use of E-mail, bulletin boards, file archives, hypertext documents, databases and other computational resources • The vast collection of computer ...
... What is the Internet? • A network of networks, joining many government, university and private computers together and providing an infrastructure for the use of E-mail, bulletin boards, file archives, hypertext documents, databases and other computational resources • The vast collection of computer ...
Measuring Application Performance with the Fluke Networks
... devices are becoming more intelligent with the inclusion of policy or protocol based packet forwarding mechanisms. With this increased functionality comes the need for advanced network monitoring hardware that can aid network engineers in diagnosing, troubleshooting and monitoring these devices, as ...
... devices are becoming more intelligent with the inclusion of policy or protocol based packet forwarding mechanisms. With this increased functionality comes the need for advanced network monitoring hardware that can aid network engineers in diagnosing, troubleshooting and monitoring these devices, as ...
The Enterprise Network Partner
... Contact Center Update: integrated customer/client interface and service delivery solution using multiple communication media, intelligent routing and business work flow in a converged network environment. Enterprise Security Refresh: comprehensive expert assessment of enterprise security implementat ...
... Contact Center Update: integrated customer/client interface and service delivery solution using multiple communication media, intelligent routing and business work flow in a converged network environment. Enterprise Security Refresh: comprehensive expert assessment of enterprise security implementat ...
Internet Addressing A Brief Introduction and History
... – a routing portion, known as the network part – a name portion known as the host part ...
... – a routing portion, known as the network part – a name portion known as the host part ...
Z - Aidan Hogan
... Can a distributed system guarantee consistency (all nodes have the same up-to-date view), availability (every read/write is acted upon) and partition-tolerance (the system works even if messages are lost) at the same time? ...
... Can a distributed system guarantee consistency (all nodes have the same up-to-date view), availability (every read/write is acted upon) and partition-tolerance (the system works even if messages are lost) at the same time? ...
ppt
... • Implementing a functionality at a lower level should have minimum performance impact on the applications that do not use the functionality ...
... • Implementing a functionality at a lower level should have minimum performance impact on the applications that do not use the functionality ...
Should SIP be modified for per call billing?
... Feedback on a call per call basis, What of mid-call congestion? Need to derive network data from application data (fragile!). INVITE to Chat Room, Video Game Need decision for each media? ...
... Feedback on a call per call basis, What of mid-call congestion? Need to derive network data from application data (fragile!). INVITE to Chat Room, Video Game Need decision for each media? ...
r for A Building
... ipHelpers List of lP-Helper addresses for doing fancy things with IP broadcasts. Use none or noHelpers to specify an emptyJist' List elements are separated with ' ,'s. ...
... ipHelpers List of lP-Helper addresses for doing fancy things with IP broadcasts. Use none or noHelpers to specify an emptyJist' List elements are separated with ' ,'s. ...