powerpoint
... lab (and all of the ICT I labs) are considered LAN segments because the computers in each lab are connected together in a kind of smaller network. • The computer workstations in each ICT I lab and each ICT II lab are connected by ethernet cables. The cables plug into the network card in each compute ...
... lab (and all of the ICT I labs) are considered LAN segments because the computers in each lab are connected together in a kind of smaller network. • The computer workstations in each ICT I lab and each ICT II lab are connected by ethernet cables. The cables plug into the network card in each compute ...
Special Workshop on Intelligence at the Network Edge Call for Papers
... Until now, the network core sustained a large percentage of the processing necessary for network control, but as the power of embedded systems increases, control processing will naturally migrate toward the network edge. This trend may open up opportunities to correct deficiencies in current network ...
... Until now, the network core sustained a large percentage of the processing necessary for network control, but as the power of embedded systems increases, control processing will naturally migrate toward the network edge. This trend may open up opportunities to correct deficiencies in current network ...
Logic Programming for Software-Defined Networks Naga Praveen Katta Jennifer Rexford David Walker
... In the past, most networks were built out of a collection of specialpurpose devices running distributed algorithms that process topology information, define routing and access control policies, perform traffic monitoring and execute other services. These networks were usually managed through a set o ...
... In the past, most networks were built out of a collection of specialpurpose devices running distributed algorithms that process topology information, define routing and access control policies, perform traffic monitoring and execute other services. These networks were usually managed through a set o ...
01-Intro
... 5. Try user’s phone number, social security number, street address, etc. 6. Try all license plate numbers (123XYZ). These can be automated and run off-line if the password hash file is obtained. Prevention: Enforce good password selection (e.g., “c0p31an6-liKe5=Alvakad05” or “3Bm1ce-c-htr”) ...
... 5. Try user’s phone number, social security number, street address, etc. 6. Try all license plate numbers (123XYZ). These can be automated and run off-line if the password hash file is obtained. Prevention: Enforce good password selection (e.g., “c0p31an6-liKe5=Alvakad05” or “3Bm1ce-c-htr”) ...
SNMPv3 Fundamentals
... Base (MIB), which stores network information, is organized and also how the protocol works to collect and store network information. The RMON standard uses SNMP with its own MIB format to collect statistics about a network. The detailed descriptions on this information, along with RMON filters and a ...
... Base (MIB), which stores network information, is organized and also how the protocol works to collect and store network information. The RMON standard uses SNMP with its own MIB format to collect statistics about a network. The detailed descriptions on this information, along with RMON filters and a ...
3 - Computer Network - Basic Concepts
... The Internet consists of a worldwide interconnection of governmental, academic, public, and private networks based upon the networking technologies of the Internet Protocol Suite. It is the successor of the Advanced Research Projects Agency Network (ARPANET) developed by DARPA of the U.S. Department ...
... The Internet consists of a worldwide interconnection of governmental, academic, public, and private networks based upon the networking technologies of the Internet Protocol Suite. It is the successor of the Advanced Research Projects Agency Network (ARPANET) developed by DARPA of the U.S. Department ...
Proposal Student Competition Enhancement
... CIFS network file-system to both Linux and Windows nodes. • Requires package samba.x86_64 • /etc/samba/smb.conf is the main configuration file • /etc/init.d/smb is the samba server service ...
... CIFS network file-system to both Linux and Windows nodes. • Requires package samba.x86_64 • /etc/samba/smb.conf is the main configuration file • /etc/init.d/smb is the samba server service ...
Survey: Distributed Operating Systems Introduction 1 Network
... • Redundancy Techniques: N-version programming helps avoid software bugs (in addition to hardware faults) by running different versions of the program on different nodes. Will this work better or worse now? ...
... • Redundancy Techniques: N-version programming helps avoid software bugs (in addition to hardware faults) by running different versions of the program on different nodes. Will this work better or worse now? ...
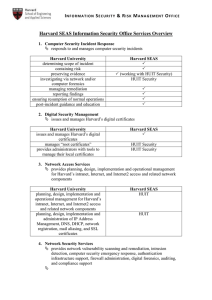
Harvard SEAS Information Security Office Services Overview
... (working with HUIT Security) HUIT Security ...
... (working with HUIT Security) HUIT Security ...
document
... • Identify compatibility issues of operating systems installed and applications running on them • Ensure hardware is secure • Determine methods to use to secure data that will be transmitted over network ...
... • Identify compatibility issues of operating systems installed and applications running on them • Ensure hardware is secure • Determine methods to use to secure data that will be transmitted over network ...
Distributed Systems
... The distributed system has a clear rules controls its services Open distributed system is flexible means easy to configure system for ...
... The distributed system has a clear rules controls its services Open distributed system is flexible means easy to configure system for ...
Quality of Service (QoS)
... • The work to ensure that IP can operate over ATM networks is done, and proven to work well • ATM's Available Bit Rate (ABR) service is intended to provide a service similar to ...
... • The work to ensure that IP can operate over ATM networks is done, and proven to work well • ATM's Available Bit Rate (ABR) service is intended to provide a service similar to ...
Ch10
... A security policy is a document or series of documents that clearly defines the defense mechanisms an organization will employ to keep information secure. It also outlines how the organization will respond to attacks as well as the duties and responsibilities of its employees for information securit ...
... A security policy is a document or series of documents that clearly defines the defense mechanisms an organization will employ to keep information secure. It also outlines how the organization will respond to attacks as well as the duties and responsibilities of its employees for information securit ...
Centre for Defence Communications and Information Networking
... of Adelaide is Australia’s leading university based concentration of defence network analysis capability. CDCIN focusses on the modelling, measurement and management of networked systems, enhancing the robustness, efficiency and effectiveness of existing and future networks. Combining outstanding ex ...
... of Adelaide is Australia’s leading university based concentration of defence network analysis capability. CDCIN focusses on the modelling, measurement and management of networked systems, enhancing the robustness, efficiency and effectiveness of existing and future networks. Combining outstanding ex ...
Computer Networks
... The Internet consists of a worldwide interconnection of governmental, academic, public, and private networks based upon the networking technologies of the Internet Protocol Suite. It is the successor of the Advanced Research Projects Agency Network (ARPANET) developed by DARPA of the U.S. Department ...
... The Internet consists of a worldwide interconnection of governmental, academic, public, and private networks based upon the networking technologies of the Internet Protocol Suite. It is the successor of the Advanced Research Projects Agency Network (ARPANET) developed by DARPA of the U.S. Department ...
Secure Network Routing: Ariadne and Skipchains
... • Need (generally) at least 3 APs passively scan all channels order all APs based on their RSSIs: R1 >= R2 >= … >= Rn exists R1-Ri-1<20 dB & R1-Ri>20 dB? ...
... • Need (generally) at least 3 APs passively scan all channels order all APs based on their RSSIs: R1 >= R2 >= … >= Rn exists R1-Ri-1<20 dB & R1-Ri>20 dB? ...
slides 1
... Allows a whole set of distributed applications A whole set of future problems need machine communication • Collaboration: Much easier for users to collaborate through network resources (such as network file systems) ...
... Allows a whole set of distributed applications A whole set of future problems need machine communication • Collaboration: Much easier for users to collaborate through network resources (such as network file systems) ...
Press release Warsaw, August 30th, 2013 Exatel is preparing the
... and jointly with PGE S.A. we have over 30 thousand. The company has interconnections with about 80 of the largest domestic operators and about 70 foreign operators allowing for data transfer, transit and termination of voice traffic through Central Europe. Exatel has also its own data centre, and as ...
... and jointly with PGE S.A. we have over 30 thousand. The company has interconnections with about 80 of the largest domestic operators and about 70 foreign operators allowing for data transfer, transit and termination of voice traffic through Central Europe. Exatel has also its own data centre, and as ...
1998-10-16-MAEDS-NetSecurity
... done by a technical elite, now programs of mass destruction are widely available • People with little or no actual knowledge can use powerful tools to compromise security • If you haven’t been scanned yet, it is just a matter of time • You NEED to know if your security is good before they find out f ...
... done by a technical elite, now programs of mass destruction are widely available • People with little or no actual knowledge can use powerful tools to compromise security • If you haven’t been scanned yet, it is just a matter of time • You NEED to know if your security is good before they find out f ...
MAIDOH_CONNECT._1
... topology to extend the maximum distance that can be spanned on a cable run. It is a network device to replicate a signal as it weakens when travelling across a network. A repeater will receive a digital signal on one of its ports, amplify it, and transmit it out the other side. Repeaters function si ...
... topology to extend the maximum distance that can be spanned on a cable run. It is a network device to replicate a signal as it weakens when travelling across a network. A repeater will receive a digital signal on one of its ports, amplify it, and transmit it out the other side. Repeaters function si ...
Understanding Networks
... Look up the seven types of Network Topologies shown below – Provide the definition and then explain the advantages and disadvantages of each in your own words! DO NOT COPY AND PASTE! YOU WILL NEED TO BE ABLE TO EXPLAIN & IDENTIFY THESE IN YOUR QUIZ ON FRIDAY! ...
... Look up the seven types of Network Topologies shown below – Provide the definition and then explain the advantages and disadvantages of each in your own words! DO NOT COPY AND PASTE! YOU WILL NEED TO BE ABLE TO EXPLAIN & IDENTIFY THESE IN YOUR QUIZ ON FRIDAY! ...
FIREWALLS
... 3. The firewall itself is immune to penetration. This implies the use of a hardened system with a secured operating system. Trusted computer systems are suitable for hosting a firewall and often required in government applications. [SMIT97] lists four general techniques that firewalls use to control ...
... 3. The firewall itself is immune to penetration. This implies the use of a hardened system with a secured operating system. Trusted computer systems are suitable for hosting a firewall and often required in government applications. [SMIT97] lists four general techniques that firewalls use to control ...
campus-area network
... illustrates how data flows within a network, regardless of its physical design. Distances between nodes, physical interconnections, transmission rates, or signal types may differ between two networks, yet their topologies may be identical. An example is a local area network (LAN): Any given node in ...
... illustrates how data flows within a network, regardless of its physical design. Distances between nodes, physical interconnections, transmission rates, or signal types may differ between two networks, yet their topologies may be identical. An example is a local area network (LAN): Any given node in ...