procedure name - Siskiyou Central Credit Union
... o The credit union has all devices assigned a static IP address, DHCP (Dynamic Host Configuration Protocol) is not enabled on the internal network. The use of DHCP is setup on the credit unions Linksys Firewall. The credit union uses a Linksys wireless router / firewall in conjunction with it‘s Link ...
... o The credit union has all devices assigned a static IP address, DHCP (Dynamic Host Configuration Protocol) is not enabled on the internal network. The use of DHCP is setup on the credit unions Linksys Firewall. The credit union uses a Linksys wireless router / firewall in conjunction with it‘s Link ...
Network Traversal
... • Gaining root access to /etc/shadow (previously /etc/passwd) leads to obtaining password hashes • John the Ripper or other password brute forcing techniques can then be used to retrieve the clear text password. • The clear text password can be used to login to other computers. • Users tend to use t ...
... • Gaining root access to /etc/shadow (previously /etc/passwd) leads to obtaining password hashes • John the Ripper or other password brute forcing techniques can then be used to retrieve the clear text password. • The clear text password can be used to login to other computers. • Users tend to use t ...
William Stallings, Cryptography and Network Security 3/e
... • however there are security concerns that cut across protocol layers • would like security implemented by the network for all applications ...
... • however there are security concerns that cut across protocol layers • would like security implemented by the network for all applications ...
pptx
... DoS, needs hypervisor SideCar: Protection w/o hypervisors Sample packets, spot-check against policy Quarantine violators ...
... DoS, needs hypervisor SideCar: Protection w/o hypervisors Sample packets, spot-check against policy Quarantine violators ...
Professional Malware is a Pandemic
... Can detect illegal modifications to the system Is the only way to detect some of the latest threats ...
... Can detect illegal modifications to the system Is the only way to detect some of the latest threats ...
that enables communication and transmission of data between
... decade, and packet-switching networks such as Telenet (1974), Scannet (1976) and Tymnet (1977) were set up, particularly for remote-terminal access to databases. In 1980s much of the growth resulted from several distinct efforts to create computer networks linking universities together basically thr ...
... decade, and packet-switching networks such as Telenet (1974), Scannet (1976) and Tymnet (1977) were set up, particularly for remote-terminal access to databases. In 1980s much of the growth resulted from several distinct efforts to create computer networks linking universities together basically thr ...
Pathways and the Pioneering Spirit
... Pathways also wanted to introduce the concept of 'anytime, anywhere' learning. Students can sit anywhere in the campus (park, amphitheatre, dining room or their own rooms) and do their projects, submit assignments, send e-mail to teachers, access library resources over the intranet, research papers ...
... Pathways also wanted to introduce the concept of 'anytime, anywhere' learning. Students can sit anywhere in the campus (park, amphitheatre, dining room or their own rooms) and do their projects, submit assignments, send e-mail to teachers, access library resources over the intranet, research papers ...
02-design
... • Yes, but only to improve performance • If network is highly unreliable • Adding some level of reliability helps performance, not correctness • Don’t try to achieve perfect reliability! • Implementing a functionality at a lower level should have minimum performance impact on the applications that d ...
... • Yes, but only to improve performance • If network is highly unreliable • Adding some level of reliability helps performance, not correctness • Don’t try to achieve perfect reliability! • Implementing a functionality at a lower level should have minimum performance impact on the applications that d ...
Lecture 5
... Class sizes were too large Did not allow administrators to control the routing very well A division of the network required the intervention of InterNIC ...
... Class sizes were too large Did not allow administrators to control the routing very well A division of the network required the intervention of InterNIC ...
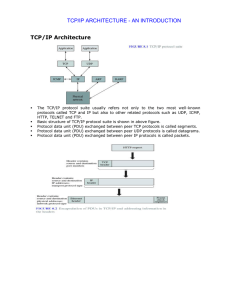
TCP/IP Architecture TCP/IP ARCHITECTURE
... IP address needs to be resolved to physical address at each IP network interface Example: Ethernet uses 48-bit addresses o Each Ethernet network interface card (NIC) has globally unique Medium Access Control (MAC) or physical address o First 24 bits identify NIC manufacturer; second 24 bits are ...
... IP address needs to be resolved to physical address at each IP network interface Example: Ethernet uses 48-bit addresses o Each Ethernet network interface card (NIC) has globally unique Medium Access Control (MAC) or physical address o First 24 bits identify NIC manufacturer; second 24 bits are ...
VB120 – 64G Modular 1G/10G Network Packet
... and data access to a system-level architecture comprised of many participating devices and ports in a single logical system. ...
... and data access to a system-level architecture comprised of many participating devices and ports in a single logical system. ...
Social Network Graphs & Data - eScholarShare
... Chang A, Schyve PM, Croteau RJ, O'Leary DS, Loeb JM. The JCAHO patient sa event taxonomy: A standardized terminology and classification schema for near m and adverse events. International Journal for Quality in Health Care. 2005;17(2):9 ...
... Chang A, Schyve PM, Croteau RJ, O'Leary DS, Loeb JM. The JCAHO patient sa event taxonomy: A standardized terminology and classification schema for near m and adverse events. International Journal for Quality in Health Care. 2005;17(2):9 ...
Secure Key Agreement for Group Communication Team A
... Current Framework Key agreement protocol Goals accomplished Goals not accomplished ...
... Current Framework Key agreement protocol Goals accomplished Goals not accomplished ...
COS 217, Spring 2005 - Princeton University
... • Scaling Ethernet to a large enterprise • Routing-protocol support for mobile hosts • Network-layer support for overlay services • Piggybacking diagnostic data on packets •
• Multiple solutions to multiple problems…
...
... • Scaling Ethernet to a large enterprise • Routing-protocol support for mobile hosts • Network-layer support for overlay services • Piggybacking diagnostic data on packets •
02-design
... • Yes, but only to improve performance • If network is highly unreliable • Adding some level of reliability helps performance, not correctness • Don’t try to achieve perfect reliability! • Implementing a functionality at a lower level should have minimum performance impact on the applications that d ...
... • Yes, but only to improve performance • If network is highly unreliable • Adding some level of reliability helps performance, not correctness • Don’t try to achieve perfect reliability! • Implementing a functionality at a lower level should have minimum performance impact on the applications that d ...
Chapter01Outline
... 6. Client-Server Network a. One or more servers centrally control security. b. Servers run a network operating system (NOS). c. Administrators assign user names and passwords. d. Uses user-level security. e. Access to shared resources is granted to a user or group. ...
... 6. Client-Server Network a. One or more servers centrally control security. b. Servers run a network operating system (NOS). c. Administrators assign user names and passwords. d. Uses user-level security. e. Access to shared resources is granted to a user or group. ...
Chapter04
... An open mail relay occurs when a mail server processes mail messages when neither the sender nor the recipient is a local user. The mail server is used to “bounce” e-mail from one outside source to other sources. In this case the mail server becomes an entirely unrelated third party. Spammers use op ...
... An open mail relay occurs when a mail server processes mail messages when neither the sender nor the recipient is a local user. The mail server is used to “bounce” e-mail from one outside source to other sources. In this case the mail server becomes an entirely unrelated third party. Spammers use op ...
Midterm Test - 18Jul08 - Solutions
... d. client/server network 5. Most ____ consist of collections of typical end-user PCs linked by a common network medium. a. LANs c. peer-to-peer networks b. internetworks d. client/server networks 6. The emerging standard for WPANs is the IEEE ____ standard. a. 802.3 c. 802.11 b. 802.5 d. 802.15 7. _ ...
... d. client/server network 5. Most ____ consist of collections of typical end-user PCs linked by a common network medium. a. LANs c. peer-to-peer networks b. internetworks d. client/server networks 6. The emerging standard for WPANs is the IEEE ____ standard. a. 802.3 c. 802.11 b. 802.5 d. 802.15 7. _ ...
Slide 1
... ◦ Systems and servers, client support, identifying and organizing network elements, sharing applications and printers, managing system resources ...
... ◦ Systems and servers, client support, identifying and organizing network elements, sharing applications and printers, managing system resources ...
Network Measurement
... Depends on what interval you use!! Traffic may be self-similar: bursts exist across a wide range of time scales Defining burstiness (precisely) is difficult ...
... Depends on what interval you use!! Traffic may be self-similar: bursts exist across a wide range of time scales Defining burstiness (precisely) is difficult ...
Internet-based Research: Perspectives of IT
... • Two servers acting as one • If one fails, we can continue to function on other ...
... • Two servers acting as one • If one fails, we can continue to function on other ...
Device Security
... • Advantages: Allows auditing and tracking forensics (in case of an attack) performance tuning (maintenance) ...
... • Advantages: Allows auditing and tracking forensics (in case of an attack) performance tuning (maintenance) ...