Communications and networking history and background Internet
... – LANs may have different properties – may be far away ...
... – LANs may have different properties – may be far away ...
Torguard Ip Checker
... Torguard Ip Checker - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
... Torguard Ip Checker - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
COEN 350
... Thorough understanding of system at the level of Sys Ad or above. Can read OS source code. Understands network protocols. ...
... Thorough understanding of system at the level of Sys Ad or above. Can read OS source code. Understands network protocols. ...
r03-arpa - Computer Engineering
... • Implementing a functionality at a lower level should have minimum performance impact on the applications that do not use the functionality ...
... • Implementing a functionality at a lower level should have minimum performance impact on the applications that do not use the functionality ...
CISSP – Chapter 7
... format of how data “Frames”* will be sent over the physical medium, so that two network cards of the same network type will actually be able to communicate. These frames are sent to the “physical” level to actually be turned into the electronic signals that are sent over a specific network. (layer 2 ...
... format of how data “Frames”* will be sent over the physical medium, so that two network cards of the same network type will actually be able to communicate. These frames are sent to the “physical” level to actually be turned into the electronic signals that are sent over a specific network. (layer 2 ...
DRAFT DRAFT DRAFT Terremark Worldwide (NASDAQ:TMRK) is a
... coming from the Cyveillance network was indicative of a potential compromise. Subsequently Terremark was asked to provide an expert opinion in the form of an ‘intelligence risk assessment’ regarding the potential of a compromise at Cyveillance. If such a compromise was discovered than Terremark woul ...
... coming from the Cyveillance network was indicative of a potential compromise. Subsequently Terremark was asked to provide an expert opinion in the form of an ‘intelligence risk assessment’ regarding the potential of a compromise at Cyveillance. If such a compromise was discovered than Terremark woul ...
CHAPTER 6
... 1. NETWORK SWITCH – A device containing multiple ports that enable you to connect computers, printers, servers and other devices to a network. A switch serves as a controller, enabling networked devices to talk to each other efficiently within a local network. ...
... 1. NETWORK SWITCH – A device containing multiple ports that enable you to connect computers, printers, servers and other devices to a network. A switch serves as a controller, enabling networked devices to talk to each other efficiently within a local network. ...
Network Environments - Advanced
... The computer on the network that controls the printing – it will manage the queue where print jobs wait before they are printed ...
... The computer on the network that controls the printing – it will manage the queue where print jobs wait before they are printed ...
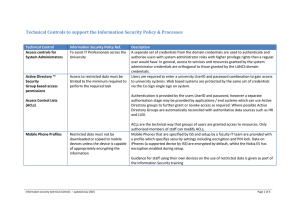
Technical Controls to support the Information
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
Introduction
... resources and information.[1] Where at least one process in one device is able to send/receive data to/from at least one process residing in a remote device, ...
... resources and information.[1] Where at least one process in one device is able to send/receive data to/from at least one process residing in a remote device, ...
Networking Vocabulary 2 Directions: 1. Go to Word. 2. Insert a Blank
... Client –Any part of the network that receives data such as a workstation Communications media – How nodes in a network are connected together (by cable, by fiber optics, radio waves, etc.) Computer network – Computers connected together for the purpose of sharing information and resources Host – Any ...
... Client –Any part of the network that receives data such as a workstation Communications media – How nodes in a network are connected together (by cable, by fiber optics, radio waves, etc.) Computer network – Computers connected together for the purpose of sharing information and resources Host – Any ...
Security Management System - Remote Client
... Security Management System – Remote Client In most of the deployment scenarios, the server application is hosted on a computer which is on the internal network of an enterprise. Hence it is not accessible from the client applications running on computers outside this internal enterprise network. Thi ...
... Security Management System – Remote Client In most of the deployment scenarios, the server application is hosted on a computer which is on the internal network of an enterprise. Hence it is not accessible from the client applications running on computers outside this internal enterprise network. Thi ...
William Stallings, Cryptography and Network Security 3/e
... • have considered some application specific security mechanisms – eg. S/MIME, PGP, Kerberos, SSL/HTTPS ...
... • have considered some application specific security mechanisms – eg. S/MIME, PGP, Kerberos, SSL/HTTPS ...
LAN design issues
... Communicate service requests to a server Needs to be robust Provide protection from programs that crash Provide a mechanism for file transfer Provide multi tasking Allow background processes to take place ...
... Communicate service requests to a server Needs to be robust Provide protection from programs that crash Provide a mechanism for file transfer Provide multi tasking Allow background processes to take place ...
Slide 1
... Measurement & feedback to programmer Is network power something that should be exposed for optimization in some way? ...
... Measurement & feedback to programmer Is network power something that should be exposed for optimization in some way? ...
DOS Defenses - Dr. Stephen C. Hayne
... Install patches to guard against TCP SYN flooding Disable any unused or unneeded network services Observe your system performance and establish baselines for ordinary activity Routinely examine your physical security with respect to your current needs ...
... Install patches to guard against TCP SYN flooding Disable any unused or unneeded network services Observe your system performance and establish baselines for ordinary activity Routinely examine your physical security with respect to your current needs ...
PPT
... • There are various network technologies that can be used to interconnect nodes. • In general, Local Area Networks (LANs) are used to connect hosts within a building. Wide Area Networks (WANs) are used across the country or planet. • We are at an interesting point, as network technology is about to ...
... • There are various network technologies that can be used to interconnect nodes. • In general, Local Area Networks (LANs) are used to connect hosts within a building. Wide Area Networks (WANs) are used across the country or planet. • We are at an interesting point, as network technology is about to ...
Security Risks - Bannerman High School
... • A firewall is a system designed to check the data coming into or going out of a network. • It : – only allows access to authorised users and applications – prevents unauthorised access to a network. ...
... • A firewall is a system designed to check the data coming into or going out of a network. • It : – only allows access to authorised users and applications – prevents unauthorised access to a network. ...
HP OpenView Network Node Manager
... • hp OpenView NNM is a robust network management platform that can provide a graphical look into your network and provide many benefits like Fault and Problem management, Performance management, etc • Makes network management proactive instead of reactive • NNM uses SNMP to discover devices on the n ...
... • hp OpenView NNM is a robust network management platform that can provide a graphical look into your network and provide many benefits like Fault and Problem management, Performance management, etc • Makes network management proactive instead of reactive • NNM uses SNMP to discover devices on the n ...
Preventative controls
... Types of Security Threats • Disruptions are the loss or reduction in network service. • Some disruptions may also be caused by or result in the destruction of data. • Natural (or manmade) disasters may occur that destroy host computers or large sections of the network. • Unauthorized access is ofte ...
... Types of Security Threats • Disruptions are the loss or reduction in network service. • Some disruptions may also be caused by or result in the destruction of data. • Natural (or manmade) disasters may occur that destroy host computers or large sections of the network. • Unauthorized access is ofte ...