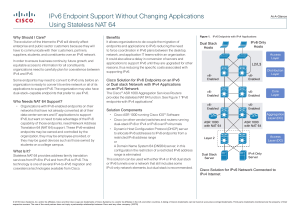
IPv6 Endpoint Support Without Changing Applications Using Stateless NAT 64
... With this solution an organization that wants to run IPv6 on a site or campus can still provide access to and from the IPv4 Internet. One important restriction of this solution is that it requires each host in the IPv6 network that needs to communicate with the IPv4 Internet to have a routable IPv4 ...
... With this solution an organization that wants to run IPv6 on a site or campus can still provide access to and from the IPv4 Internet. One important restriction of this solution is that it requires each host in the IPv6 network that needs to communicate with the IPv4 Internet to have a routable IPv4 ...
Routing
... • Best known algorithm to compute the shortest path between two nodes is Dijkstra (1959) —Each node is labeled with its distance from the source node along the best known path —Initially, no paths are known, so all nodes are labeled ...
... • Best known algorithm to compute the shortest path between two nodes is Dijkstra (1959) —Each node is labeled with its distance from the source node along the best known path —Initially, no paths are known, so all nodes are labeled ...
Prestige 645M
... Repair or replacement, as provided under this warranty, is the exclusive remedy of the purchaser. This warranty is in lieu of all other warranties, express or implied, including any implied warranty of merchantability or fitness for a particular use or purpose. ZyXEL shall in no event be held liable ...
... Repair or replacement, as provided under this warranty, is the exclusive remedy of the purchaser. This warranty is in lieu of all other warranties, express or implied, including any implied warranty of merchantability or fitness for a particular use or purpose. ZyXEL shall in no event be held liable ...
Multicast Basic Concept
... – Routers limit broadcasts to the local network or subnet, preventing broadcasts form reaching the Internet at large. ...
... – Routers limit broadcasts to the local network or subnet, preventing broadcasts form reaching the Internet at large. ...
Impact of Delay in Voice over IP Services
... The IP Network delay is generally the round trip delay for an IP packet within the IP network. This may be measured using tools such as “ping” or protocols such as RTCP. It is important to note that some IP networks treat the RTP packets used to transport voice with higher priority than other packet ...
... The IP Network delay is generally the round trip delay for an IP packet within the IP network. This may be measured using tools such as “ping” or protocols such as RTCP. It is important to note that some IP networks treat the RTP packets used to transport voice with higher priority than other packet ...
ICMP
... 3. Each router decreases the TTL value by one until it reaches zero. The datagram is then discarded and a destination unreachable message is sent to the source 4. If a router is unable to deliver a packet to its destination the router discards the original packet 5. A host or gateway may send the IC ...
... 3. Each router decreases the TTL value by one until it reaches zero. The datagram is then discarded and a destination unreachable message is sent to the source 4. If a router is unable to deliver a packet to its destination the router discards the original packet 5. A host or gateway may send the IC ...
mpls
... In MPLS Domain, all the traffic in a set of FECs might follow the same route. Example – a set of distinct address prefixes might all have the same egress node. In such case, the union of those FECs it itself a FEC. The procedure of binding a single label to a union of FECs which is itself a FEC, and ...
... In MPLS Domain, all the traffic in a set of FECs might follow the same route. Example – a set of distinct address prefixes might all have the same egress node. In such case, the union of those FECs it itself a FEC. The procedure of binding a single label to a union of FECs which is itself a FEC, and ...
The IETF is organized into 10 Areas with a number of Working
... the scope of the Routing Area. Traffic engineering routing and signaling protocols are in scope, as is the architecture and protocols for the Path Computation Element that helps to select end-to-end paths for traffic-engineered routing. The Routing Area also works on Generalized MPLS used in the con ...
... the scope of the Routing Area. Traffic engineering routing and signaling protocols are in scope, as is the architecture and protocols for the Path Computation Element that helps to select end-to-end paths for traffic-engineered routing. The Routing Area also works on Generalized MPLS used in the con ...
High-Performance Network Security Monitoring at the Lawrence
... Easily finds braid-dead internal scanners but also misconfigurations Some traffic is routed to a honeyfarm ...
... Easily finds braid-dead internal scanners but also misconfigurations Some traffic is routed to a honeyfarm ...
Chapter 6: Multimedia Networking
... A new class continuous media applications: ◦ Entertainment video, IP telephony, Internet radio, Multimedia WWW sites, teleconferencing, interactive games, virtual worlds, distance learning ... ...
... A new class continuous media applications: ◦ Entertainment video, IP telephony, Internet radio, Multimedia WWW sites, teleconferencing, interactive games, virtual worlds, distance learning ... ...
CCNA 2 Final Exam Answers v4.0 100%
... It is saved in the topology table for use if the primary route fails. It may be backed up by a feasible successor route. It is used by EIGRP to forward traffic to the destination. It is flagged as active in the routing table. After the discovery process has occurred, the successor route is stored in ...
... It is saved in the topology table for use if the primary route fails. It may be backed up by a feasible successor route. It is used by EIGRP to forward traffic to the destination. It is flagged as active in the routing table. After the discovery process has occurred, the successor route is stored in ...
COMPUTER NETWORKS
... life makes the role of the computer networks vital. Computer networks are used to transfer data between the communicating systems. Computer networks need to be designed using appropriate topology and network technologies in order to be fast, reliable and easy expandable. The transmitted data is divi ...
... life makes the role of the computer networks vital. Computer networks are used to transfer data between the communicating systems. Computer networks need to be designed using appropriate topology and network technologies in order to be fast, reliable and easy expandable. The transmitted data is divi ...
H04L - Cooperative Patent Classification
... ACK signaling see also H04L 5/0053)} . . . . {ARQ related signaling (H04L 1/1607 takes precedence)} . . . {Arrangements specific to the transmitter end} . . . . {Details of sliding window management} . . . . {Buffer management} . . . . . {for semi-reliable protocols, e.g. for less sensitive applicat ...
... ACK signaling see also H04L 5/0053)} . . . . {ARQ related signaling (H04L 1/1607 takes precedence)} . . . {Arrangements specific to the transmitter end} . . . . {Details of sliding window management} . . . . {Buffer management} . . . . . {for semi-reliable protocols, e.g. for less sensitive applicat ...
Networking the Internet - Part 1
... U.S.S.R. launching Sputnik, the first satellite. Out of this came the Internet, a way for computers to communicate from different parts of the world. These computers can be any type of computer using any type of operating system, as long as they are using the protocol TCP/IP. ...
... U.S.S.R. launching Sputnik, the first satellite. Out of this came the Internet, a way for computers to communicate from different parts of the world. These computers can be any type of computer using any type of operating system, as long as they are using the protocol TCP/IP. ...
Manual AV200-WME F-EU-ENG-May 31-07.indd
... product, or made available to you by CORINEX via download or otherwise, in whatever form or media, will constitute your acceptance of these terms, unless separate terms are provided by the software supplier, in which case certain additional or different terms may apply. If you do not agree with the ...
... product, or made available to you by CORINEX via download or otherwise, in whatever form or media, will constitute your acceptance of these terms, unless separate terms are provided by the software supplier, in which case certain additional or different terms may apply. If you do not agree with the ...
Management Information Systems 6/e
... networks serving areas not immediately contiguous Metropolitan Area Network (MAN) – a set of connected networks within the same city or metropolitan area but not in immediate proximity to ...
... networks serving areas not immediately contiguous Metropolitan Area Network (MAN) – a set of connected networks within the same city or metropolitan area but not in immediate proximity to ...
VROOM: Virtual ROuters On the Move
... 4]. Compared with their TDM counterparts, packetaware access networks allow for more efficient multiplexing (empty frames are not transmitted) and simplified router line cards (no need to terminate large numbers of low rate interfaces on routers). Of particular interest for the VROOM architecture is ...
... 4]. Compared with their TDM counterparts, packetaware access networks allow for more efficient multiplexing (empty frames are not transmitted) and simplified router line cards (no need to terminate large numbers of low rate interfaces on routers). Of particular interest for the VROOM architecture is ...
Measurement guide and report template
... Replace the <> texts with the corresponding screenshot required!
...
... Replace the <
Broadband Router BR6101
... The WAN “idle timeout” auto-disconnect function may not work due to abnormal activities of some network application software, computer virus or hacker attacks from the Internet. For example, some software sends network packets to the Internet in the background, even when you are not using the Intern ...
... The WAN “idle timeout” auto-disconnect function may not work due to abnormal activities of some network application software, computer virus or hacker attacks from the Internet. For example, some software sends network packets to the Internet in the background, even when you are not using the Intern ...
Transmission Control Protocol
... Congestion: informally: “too many sources sending too much data too fast for network to handle” Different from flow control! Manifestations: ...
... Congestion: informally: “too many sources sending too much data too fast for network to handle” Different from flow control! Manifestations: ...
Passport: Secure and Adoptable Source Authentication
... Passport is plausible for gigabit links, and can mitigate reflector attacks even without separate denial-of-service defenses. Our adoptability modeling shows that Passport provides stronger security and deployment incentives than alternatives such as ingress filtering. This is because the ISPs that ...
... Passport is plausible for gigabit links, and can mitigate reflector attacks even without separate denial-of-service defenses. Our adoptability modeling shows that Passport provides stronger security and deployment incentives than alternatives such as ingress filtering. This is because the ISPs that ...
ECE 467 Network Implementation Lab Manual
... Internal Gateway Routing protocol (IGRP).......................................................................... 51 The Routing Problem.................................................................................................................... 52 Summary of IGRP............................ ...
... Internal Gateway Routing protocol (IGRP).......................................................................... 51 The Routing Problem.................................................................................................................... 52 Summary of IGRP............................ ...