Routing - La Salle University
... • A router determines where to forward “internet” traffic (messages whose source is on one network and destination is on another network). • It also filters out local traffic. CSIT 220 (Blum) ...
... • A router determines where to forward “internet” traffic (messages whose source is on one network and destination is on another network). • It also filters out local traffic. CSIT 220 (Blum) ...
Routing - La Salle University
... router determines where to forward “internet” traffic (messages whose source is on one network and destination is on another network). ...
... router determines where to forward “internet” traffic (messages whose source is on one network and destination is on another network). ...
Distributed Pub/Sub
... Simple process for matching an event to subscriptions. However, limited expressiveness. Event filtering is easy, event routing is difficult (Heavy load on the network). The challenge is to multicast event effectively to subscribers. ...
... Simple process for matching an event to subscriptions. However, limited expressiveness. Event filtering is easy, event routing is difficult (Heavy load on the network). The challenge is to multicast event effectively to subscribers. ...
The Network Layer
... received a packet to be forwarded, it looks at this table to find the route to the final destination. c) However, this simple solution is impossible in today’s Internet world because the number of entries in the routing table makes the table lookups inefficient. d) Need to make the size of table man ...
... received a packet to be forwarded, it looks at this table to find the route to the final destination. c) However, this simple solution is impossible in today’s Internet world because the number of entries in the routing table makes the table lookups inefficient. d) Need to make the size of table man ...
Understanding Network Failures in Data Centers: Measurement, Analysis, and Implications
... operators want to mask all failures before applications experience any disruption. Current data center networks typically provide 1:1 redundancy to allow traffic to flow along an alternate route when a device or link becomes unavailable [1]. However, this redundancy comes at a high cost—both monetar ...
... operators want to mask all failures before applications experience any disruption. Current data center networks typically provide 1:1 redundancy to allow traffic to flow along an alternate route when a device or link becomes unavailable [1]. However, this redundancy comes at a high cost—both monetar ...
Understanding Network Failures in Data Centers: Measurement
... center networks. Motivated by issues encountered by network operators, we study network reliability along three dimensions: • Characterizing the most failure prone network elements. To achieve high availability amidst multiple failure sources such as hardware, software, and human errors, operators n ...
... center networks. Motivated by issues encountered by network operators, we study network reliability along three dimensions: • Characterizing the most failure prone network elements. To achieve high availability amidst multiple failure sources such as hardware, software, and human errors, operators n ...
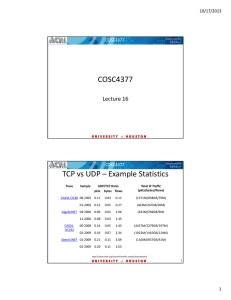
COSC4377 TCP vs UDP – Example Statistics
... – 2) Availability of IPv6 from access network providers. Over the past year, some of the largest growth ia coming from major ISPs within the U.S., as they roll out production IPv6 support to their end‐users, including Verizon Wireless, AT&T, and Comcast. This is on top of some ISPs in Europe and ...
... – 2) Availability of IPv6 from access network providers. Over the past year, some of the largest growth ia coming from major ISPs within the U.S., as they roll out production IPv6 support to their end‐users, including Verizon Wireless, AT&T, and Comcast. This is on top of some ISPs in Europe and ...
KMBE - RADProductsOnline, Buy RAD Products Online at Great Prices
... intellectual property or other proprietary rights relating to this manual and to the KMBE and any software components contained therein are proprietary products of RAD protected under international copyright law and shall be and remain solely with RAD. KMBE is a registered trademark of RAD. No right ...
... intellectual property or other proprietary rights relating to this manual and to the KMBE and any software components contained therein are proprietary products of RAD protected under international copyright law and shall be and remain solely with RAD. KMBE is a registered trademark of RAD. No right ...
ICN`12 ~ Coexist: A Hybrid Approach for Content Oriented Publish
... paradigm that fills the gap between the content-centric needs of a customer and the current location-centric network architecture. Named Data Networking (NDN) [20] is a popular example of CCN, aiming to transform content as a first-class entity. With CCN, an end host can therefore issue a query for ...
... paradigm that fills the gap between the content-centric needs of a customer and the current location-centric network architecture. Named Data Networking (NDN) [20] is a popular example of CCN, aiming to transform content as a first-class entity. With CCN, an end host can therefore issue a query for ...
Computer Communications
... (1) http://stats.bls/gov/opub/mlr/1999/11/art4full.pdf (2) http://stats.bls.gov/news.release/ecopro.t06.htm Note: Jobs are stated in thousands ...
... (1) http://stats.bls/gov/opub/mlr/1999/11/art4full.pdf (2) http://stats.bls.gov/news.release/ecopro.t06.htm Note: Jobs are stated in thousands ...
Case Studies on IP-based Interconnection for Voice Services
... operators therefore demand IP-based interconnection for voice services (IPvIC) instead of TDM-based interconnection for voice services (TDMvIC). If there is a mutual commercial interest, operators will migrate from TDMvIC to IPvIC on a voluntary basis. However, in other cases regulatory intervention ...
... operators therefore demand IP-based interconnection for voice services (IPvIC) instead of TDM-based interconnection for voice services (TDMvIC). If there is a mutual commercial interest, operators will migrate from TDMvIC to IPvIC on a voluntary basis. However, in other cases regulatory intervention ...
Attacks to the IDS
... Detection The dynamic update problem is unsolved. – You can train these systems successfully to handle static environments, but computer networks are dynamic. – If you try to retrain an existing system to deal with new events, it will usually forget its old training. You have to give it the old trai ...
... Detection The dynamic update problem is unsolved. – You can train these systems successfully to handle static environments, but computer networks are dynamic. – If you try to retrain an existing system to deal with new events, it will usually forget its old training. You have to give it the old trai ...
Introduction to SDN and OpenFlow
... The flow tables of a switch are sequentially numbered, starting at 0 A packet is processed sequentially in multiple flow tables (version 1.1) • If a flow entry is found, the instruction set included in that flow entry is executed • Instructions may explicitly direct the packet to another flow ta ...
... The flow tables of a switch are sequentially numbered, starting at 0 A packet is processed sequentially in multiple flow tables (version 1.1) • If a flow entry is found, the instruction set included in that flow entry is executed • Instructions may explicitly direct the packet to another flow ta ...
Dynamic addressing
... • TCP/IP transport layer using UDP does not always guarantee reliable delivery of packets as the transport layer in the OSI model does. Dr. L. Christofi ...
... • TCP/IP transport layer using UDP does not always guarantee reliable delivery of packets as the transport layer in the OSI model does. Dr. L. Christofi ...
Attacks to the IDS
... Detection The dynamic update problem is unsolved. – You can train these systems successfully to handle static environments, but computer networks are dynamic. – If you try to retrain an existing system to deal with new events, it will usually forget its old training. You have to give it the old trai ...
... Detection The dynamic update problem is unsolved. – You can train these systems successfully to handle static environments, but computer networks are dynamic. – If you try to retrain an existing system to deal with new events, it will usually forget its old training. You have to give it the old trai ...
slides - Network and Systems Laboratory
... What do they want to know? What makes Skype so successful? Compare with File-sharing P2P network ...
... What do they want to know? What makes Skype so successful? Compare with File-sharing P2P network ...
TIE Breaking: Tunable Interdomain Egress Selection
... Although consistent forwarding is clearly an important property for any routing system, routers now have other ways of achieving this goal. In particular, the greater availability of tunneling technology allows for more sophisticated egress-selection rules, which are not tied to the IGP metrics. Int ...
... Although consistent forwarding is clearly an important property for any routing system, routers now have other ways of achieving this goal. In particular, the greater availability of tunneling technology allows for more sophisticated egress-selection rules, which are not tied to the IGP metrics. Int ...
IPv6 based NGN
... packet-based network able to provide Telecommunication Services to users and able to make use of multiple broadband, QoS-enabled transport technologies and in which service-related functions are independent of the underlying transportrelated technologies. ...
... packet-based network able to provide Telecommunication Services to users and able to make use of multiple broadband, QoS-enabled transport technologies and in which service-related functions are independent of the underlying transportrelated technologies. ...
Router R1 in Figure 6.8 receives a packet with destination address
... address). Every packet with destination address in the range 145.14.0.0 to 145.14.255.255 is delivered to the interface m4 and distributed to the final destination subnet by the router. Second, we have used the address x.y.z.t/n for the interface m4 because we do not know to which network this route ...
... address). Every packet with destination address in the range 145.14.0.0 to 145.14.255.255 is delivered to the interface m4 and distributed to the final destination subnet by the router. Second, we have used the address x.y.z.t/n for the interface m4 because we do not know to which network this route ...
Basic Features of i-mode - San Jose State University
... • i-mode was developed by DoCoMo ( which means “anywhere” in Japanese) as a subsidiary of NTT (The Japan’s largest telecommunication service provider Nippon Telegraph and Telephone Corp.) in 1992. • i-mode (The “i” stands for information) is a wireless technology and service mark. • The i-mode servi ...
... • i-mode was developed by DoCoMo ( which means “anywhere” in Japanese) as a subsidiary of NTT (The Japan’s largest telecommunication service provider Nippon Telegraph and Telephone Corp.) in 1992. • i-mode (The “i” stands for information) is a wireless technology and service mark. • The i-mode servi ...
Measurement and Analysis of TCP Throughput Collapse in Cluster-based Storage Systems
... client increases past the ability of an Ethernet switch to buffer packets. As we explore further in §2, the problem arises from a subtle interaction between limited Ethernet switch buffer sizes, the communication patterns common in cluster-based storage systems, and TCP’s loss recovery mechanisms. B ...
... client increases past the ability of an Ethernet switch to buffer packets. As we explore further in §2, the problem arises from a subtle interaction between limited Ethernet switch buffer sizes, the communication patterns common in cluster-based storage systems, and TCP’s loss recovery mechanisms. B ...
mm_streaming - College of Engineering | Oregon State University
... how does callee advertise its IP address, port number, encoding algorithms? 7: Multimedia Networking ...
... how does callee advertise its IP address, port number, encoding algorithms? 7: Multimedia Networking ...
This chapter covers the following key topics: • Overview of routers
... route disappears, but the same route reappears with a higher metric (presumably emanating from another router, indicating a possible “good” alternative path), the route is still put into a hold-down state. Thus, the amount of time for the entire network to converge is still increased. Another major ...
... route disappears, but the same route reappears with a higher metric (presumably emanating from another router, indicating a possible “good” alternative path), the route is still put into a hold-down state. Thus, the amount of time for the entire network to converge is still increased. Another major ...
QoS - Rudra Dutta
... Buffer management: allocate buffers to user flows Packet scheduling: determine which packet to transmit next (Performance and fault management): monitor for defects that affect performance (Protection switching): protect traffic from failures by switching to alternate path – fault tolerance ...
... Buffer management: allocate buffers to user flows Packet scheduling: determine which packet to transmit next (Performance and fault management): monitor for defects that affect performance (Protection switching): protect traffic from failures by switching to alternate path – fault tolerance ...
csci5211: Computer Networks and Data Communications
... • Limited knowledge of network conditions – Members do not know delay to each other when they join – Members probe each other to learn network related information – Overlay must self-improve as more information available ...
... • Limited knowledge of network conditions – Members do not know delay to each other when they join – Members probe each other to learn network related information – Overlay must self-improve as more information available ...