D3.2 Traffic Models
... Internet usage is evolving, from the traditional WWW usage (i.e. downloading web pages), to tripleplay usage where households may have all their communication services (telephony, data, TV) through their broadband access connection. The challenge is to design IP access networks so that they can deli ...
... Internet usage is evolving, from the traditional WWW usage (i.e. downloading web pages), to tripleplay usage where households may have all their communication services (telephony, data, TV) through their broadband access connection. The challenge is to design IP access networks so that they can deli ...
Quality of Service in mobile ad hoc networks: a
... therefore, transmission of a node are heard by nodes in its vicinity. This causes one more issue – nodes need to coordinate among themselves for transmissions through a shared channel. In other words, a node cannot decide on its alone about the time of the beginning of a transmission because the cha ...
... therefore, transmission of a node are heard by nodes in its vicinity. This causes one more issue – nodes need to coordinate among themselves for transmissions through a shared channel. In other words, a node cannot decide on its alone about the time of the beginning of a transmission because the cha ...
IP Multicast
... • Steiner Tree: minimum cost tree connecting all routers with attached group members. • Problem is NP-complete. • Excellent heuristics exist. • Not used in practice: – computational complexity. – information about entire network needed. – monolithic: rerun whenever a router needs to ...
... • Steiner Tree: minimum cost tree connecting all routers with attached group members. • Problem is NP-complete. • Excellent heuristics exist. • Not used in practice: – computational complexity. – information about entire network needed. – monolithic: rerun whenever a router needs to ...
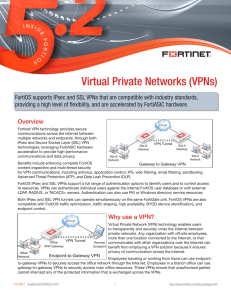
Virtual Private Networks (VPNs)
... and redundant configurations where a single VPN must connect multiple networks through a single gateway or concentrator. SSL VPN configurations are usually simpler than IPsec VPN configurations. All the complex networking is handled by the network infrastructure and the VPN configuration can focus o ...
... and redundant configurations where a single VPN must connect multiple networks through a single gateway or concentrator. SSL VPN configurations are usually simpler than IPsec VPN configurations. All the complex networking is handled by the network infrastructure and the VPN configuration can focus o ...
Week_Nine
... An interior gateway protocol (IGP) is a routing protocol that is used within an autonomous system (AS). Two types of IGP. Distance-vector routing protocols each router does not possess information about the full network topology. It advertises its distances to other routers and receives similar adve ...
... An interior gateway protocol (IGP) is a routing protocol that is used within an autonomous system (AS). Two types of IGP. Distance-vector routing protocols each router does not possess information about the full network topology. It advertises its distances to other routers and receives similar adve ...
Week_Nine
... An interior gateway protocol (IGP) is a routing protocol that is used within an autonomous system (AS). Two types of IGP. Distance-vector routing protocols each router does not possess information about the full network topology. It advertises its distances to other routers and receives similar adve ...
... An interior gateway protocol (IGP) is a routing protocol that is used within an autonomous system (AS). Two types of IGP. Distance-vector routing protocols each router does not possess information about the full network topology. It advertises its distances to other routers and receives similar adve ...
Print Version The Internet and the World Wide Web
... Bandwidth is the amount of data that can be transmitted over a network in a certain amount of time. Bandwidth is measured in Mbit/s (megabits per second), Kbit/s (kilobits per second), or bit/s (bits per second). If the bandwidth of a network is 1 Mbit/s, then 1 megabit of data can be transmitted ov ...
... Bandwidth is the amount of data that can be transmitted over a network in a certain amount of time. Bandwidth is measured in Mbit/s (megabits per second), Kbit/s (kilobits per second), or bit/s (bits per second). If the bandwidth of a network is 1 Mbit/s, then 1 megabit of data can be transmitted ov ...
Tarzan: A Peer-to-Peer Anonymizing Network
... and these relays provide obvious targets for attacking or blocking. Few of these systems attempt to provide anonymity against an adversary that can passively observe all network traffic. Such protection requires fixing traffic patterns or using cover traffic to make such traffic analysis more diffic ...
... and these relays provide obvious targets for attacking or blocking. Few of these systems attempt to provide anonymity against an adversary that can passively observe all network traffic. Such protection requires fixing traffic patterns or using cover traffic to make such traffic analysis more diffic ...
PowerPoint - ECSE - Rensselaer Polytechnic Institute
... airplane routing from source to destination ...
... airplane routing from source to destination ...
Tarzan: A Peer-to-Peer Anonymizing Network Layer
... and these relays provide obvious targets for attacking or blocking. Few of these systems attempt to provide anonymity against an adversary that can passively observe all network traffic. Such protection requires fixing traffic patterns or using cover traffic to make such traffic analysis more diffic ...
... and these relays provide obvious targets for attacking or blocking. Few of these systems attempt to provide anonymity against an adversary that can passively observe all network traffic. Such protection requires fixing traffic patterns or using cover traffic to make such traffic analysis more diffic ...
TCP, IGP, EGP etc. - La Salle University
... In hot potato routing, or deflection routing, the routers have no buffer to store packets in before forwarded on to their final predetermined destination. In normal routing, when many packets are destined for a given outgoing channel, packets are either buffered or dropped. But in hot potato routing ...
... In hot potato routing, or deflection routing, the routers have no buffer to store packets in before forwarded on to their final predetermined destination. In normal routing, when many packets are destined for a given outgoing channel, packets are either buffered or dropped. But in hot potato routing ...
Accurate Real-time Identification of IP Prefix
... significantly disrupt the stability and security of the Internet. Moreover, stolen IPs were also found to be sold or leased to networks in need of IP address spaces [27]. Note that the symptom of IP hijacking from victim’s perspective is similar to other outages, making it nontrivial to diagnose. Be ...
... significantly disrupt the stability and security of the Internet. Moreover, stolen IPs were also found to be sold or leased to networks in need of IP address spaces [27]. Note that the symptom of IP hijacking from victim’s perspective is similar to other outages, making it nontrivial to diagnose. Be ...
1.4 Flow of TD-LRAIC modelling
... costs which is caused by the provision of defined increment and allocating estimated costs to to one unit of service. Incremental costs for interconnection service can be defined as costs that can be avoided if interconnection service were no longer be provided1. In the short incremental costs can d ...
... costs which is caused by the provision of defined increment and allocating estimated costs to to one unit of service. Incremental costs for interconnection service can be defined as costs that can be avoided if interconnection service were no longer be provided1. In the short incremental costs can d ...
show route
... You configure user-defined routing instances at the [edit routing-instances] hierarchy level •Typically used for filter-based forwarding, VPN services, and system virtualization; routing instance types include: [edit routing-instances]
...
... You configure user-defined routing instances at the [edit routing-instances] hierarchy level •Typically used for filter-based forwarding, VPN services, and system virtualization; routing instance types include: [edit routing-instances
Arch Rock
... • Lack of broadcast capability impedes or, in some cases, renders some protocols inoperable (e.g. DHCP). Broadcast media can also allow efficient operation of multicast, a core mechanism of IPv6 • Link-layer error recovery often increases end-to-end performance. However, it should be lightweight and ...
... • Lack of broadcast capability impedes or, in some cases, renders some protocols inoperable (e.g. DHCP). Broadcast media can also allow efficient operation of multicast, a core mechanism of IPv6 • Link-layer error recovery often increases end-to-end performance. However, it should be lightweight and ...
About the Presentations
... • Rebuild the packet with new source IP information – Shields internal users from those on the outside ...
... • Rebuild the packet with new source IP information – Shields internal users from those on the outside ...
Impact of IPsec and 6to4 on VoIP Quality over IPv6
... client-to-client (i.e., IPsec transport mode for secure endto-end communication; although transport mode would typically be used when there is no VPN as we explain later, IPsec allows clients communicating through a VPN to use end-to-end security for added protection). We use ESP tunnel and transpor ...
... client-to-client (i.e., IPsec transport mode for secure endto-end communication; although transport mode would typically be used when there is no VPN as we explain later, IPsec allows clients communicating through a VPN to use end-to-end security for added protection). We use ESP tunnel and transpor ...
What`s New with vCloud Director 8.0
... VMware vCloud Director 8.0 introduces the concept of virtual data center templates, which provide a standard specification for new virtual data centers deployed by approved users within tenant organizations. Virtual data center templates are created by systems administrators with pre-defined charact ...
... VMware vCloud Director 8.0 introduces the concept of virtual data center templates, which provide a standard specification for new virtual data centers deployed by approved users within tenant organizations. Virtual data center templates are created by systems administrators with pre-defined charact ...
A New Service for Increasing the Effectiveness of Network Address Blacklists
... slightly favored. Finally, while v1 shares no overlap attacker with any other victim, v2 and v3 who are correlated with v1 do share an overlapped attacker with v5 . Therefore, s7 which attacked v5 would be given a non-zero score. Effectively, this favoring scheme forms a transitive closure of overl ...
... slightly favored. Finally, while v1 shares no overlap attacker with any other victim, v2 and v3 who are correlated with v1 do share an overlapped attacker with v5 . Therefore, s7 which attacked v5 would be given a non-zero score. Effectively, this favoring scheme forms a transitive closure of overl ...
Defending Network-Based Services Against Denial of Service Attacks
... Over the last decade, several value-added services have been proposed for deployment in the Internet. These include multicast communication [1], quality-of-service support [2], content distribution networks [3], and denial-of-service (DoS) defense mechanisms [4]. These services provide users with an ...
... Over the last decade, several value-added services have been proposed for deployment in the Internet. These include multicast communication [1], quality-of-service support [2], content distribution networks [3], and denial-of-service (DoS) defense mechanisms [4]. These services provide users with an ...
Berkeley NOW - Computer Science Division
... • Naturally adapts to available connectivity • Minimal state and protocol overhead => surprising complexity in this simple mechanism ...
... • Naturally adapts to available connectivity • Minimal state and protocol overhead => surprising complexity in this simple mechanism ...
Linksys NR041 Manual
... A dynamic IP address is automatically assigned to a device on the network, such as PCs and print servers. These IP addresses are called “dynamic” because they are only temporarily assigned to the PC or device. After a certain time period, they expire and may change. If a PC logs onto the network (or ...
... A dynamic IP address is automatically assigned to a device on the network, such as PCs and print servers. These IP addresses are called “dynamic” because they are only temporarily assigned to the PC or device. After a certain time period, they expire and may change. If a PC logs onto the network (or ...
router isis as42
... Router dead interval – how long to wait before deciding router has disappeared The values of “hello interval” and “router dead interval” must match on both neighbours ...
... Router dead interval – how long to wait before deciding router has disappeared The values of “hello interval” and “router dead interval” must match on both neighbours ...