OPERATING SYSTEM CONCEPTS Avi Silberschatz Department of
... Time-Sharing Systems− Interactive Computing ...
... Time-Sharing Systems− Interactive Computing ...
Module 6: CPU Scheduling
... jumping to the proper location in the user program to restart that program ...
... jumping to the proper location in the user program to restart that program ...
Wikibook
... trademark of The Open Group which licenses it for use with any operating system that has been shown to conform to their definitions. "UNIX-like" is commonly used to refer to the large set of operating systems which resemble the original UNIX. Unix-like systems run on a wide variety of computer archi ...
... trademark of The Open Group which licenses it for use with any operating system that has been shown to conform to their definitions. "UNIX-like" is commonly used to refer to the large set of operating systems which resemble the original UNIX. Unix-like systems run on a wide variety of computer archi ...
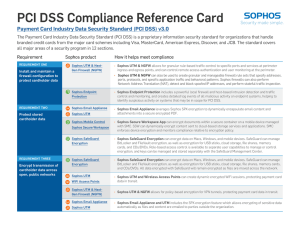
PCI DSS Compliance Reference Card
... ÌÌ Sophos UTM & NGFW can also be used to create granular and manageable firewall rule sets that specify addresses, ports, protocols, and specific application traffic and behavioral patterns. Sophos firewalls can also perform Network Address Translation (NAT), detect and block spoofed IP addresses, a ...
... ÌÌ Sophos UTM & NGFW can also be used to create granular and manageable firewall rule sets that specify addresses, ports, protocols, and specific application traffic and behavioral patterns. Sophos firewalls can also perform Network Address Translation (NAT), detect and block spoofed IP addresses, a ...
I/O Speculation for the Microsecond Era
... it attempts to use data that the OS has not read yet. In addition, the operating system may have a mechanism to rollback if the I/O operation does not complete successfully. By speculating, an application can continue to do useful work even if the I/O has not completed. In the context of microsecond ...
... it attempts to use data that the OS has not read yet. In addition, the operating system may have a mechanism to rollback if the I/O operation does not complete successfully. By speculating, an application can continue to do useful work even if the I/O has not completed. In the context of microsecond ...
ppt
... and storage over typically TCP or UDP on IP network iSCSI protocol uses IP network to carry the SCSI protocol ...
... and storage over typically TCP or UDP on IP network iSCSI protocol uses IP network to carry the SCSI protocol ...
Chapter 10: Mass-Storage Systems
... and storage over typically TCP or UDP on IP network iSCSI protocol uses IP network to carry the SCSI protocol ...
... and storage over typically TCP or UDP on IP network iSCSI protocol uses IP network to carry the SCSI protocol ...
Chapter 10: Mass-Storage Structure
... and storage over typically TCP or UDP on IP network iSCSI protocol uses IP network to carry the SCSI protocol ...
... and storage over typically TCP or UDP on IP network iSCSI protocol uses IP network to carry the SCSI protocol ...
Mass Storage - UCSB Computer Science
... SSTF (Shortest Seek Time First) Selects the request with the minimum seek time from ...
... SSTF (Shortest Seek Time First) Selects the request with the minimum seek time from ...
The Impact of Architectural Trends on Operating System Performance
... Computer systems are rapidly changing. Over the next few years, we will see wide-scale deployment of dynamically-scheduled processors that can issue multiple instructions every clock cycle, execute instructions out of order, and overlap computation and cache misses. We also expect clock-rates to inc ...
... Computer systems are rapidly changing. Over the next few years, we will see wide-scale deployment of dynamically-scheduled processors that can issue multiple instructions every clock cycle, execute instructions out of order, and overlap computation and cache misses. We also expect clock-rates to inc ...
Benchmarking Real-time Operating Systems for use in Radio Base
... GCC GNU Compiler Collection, compiler system by the GNU Project that support various programming languages. ...
... GCC GNU Compiler Collection, compiler system by the GNU Project that support various programming languages. ...
Isolating Faulty Device Drivers
... safe reuse of legacy extensions for security-sensitive applications. In recent years, user-mode drivers were also used in commodity systems such as Linux [20] and Windows [25], but we are not aware of efforts to isolate drivers based on least authority and believe that these systems could benefit fr ...
... safe reuse of legacy extensions for security-sensitive applications. In recent years, user-mode drivers were also used in commodity systems such as Linux [20] and Windows [25], but we are not aware of efforts to isolate drivers based on least authority and believe that these systems could benefit fr ...
Cooperating Processes
... • Blocking send: The sender is blocked until the requested message is delivered. • Nonblocking send: The sending process sends the message and resumes operation. • Blocking receive: The receiver blocks until the requested message is delivered/arrived. • Nonblocking receive: The receiver retrieves ei ...
... • Blocking send: The sender is blocked until the requested message is delivered. • Nonblocking send: The sending process sends the message and resumes operation. • Blocking receive: The receiver blocks until the requested message is delivered/arrived. • Nonblocking receive: The receiver retrieves ei ...
Module 6: CPU Scheduling
... (or most of) its logical address space and system resources with other process(es); in contrast to a thread, a lightweight process has its own private process identifier and parenthood relationships with other processes) ...
... (or most of) its logical address space and system resources with other process(es); in contrast to a thread, a lightweight process has its own private process identifier and parenthood relationships with other processes) ...
NAVAL POSTGRADUATE SCHOOL
... images of itself allows efficient testing of differing design decisions of system programs. In order to create multiple running simulated copies on a single host machine, IBM developed a construct it called the Control Program or CP for short. IBM also developed a simple single user operating system ...
... images of itself allows efficient testing of differing design decisions of system programs. In order to create multiple running simulated copies on a single host machine, IBM developed a construct it called the Control Program or CP for short. IBM also developed a simple single user operating system ...
Chapter 4: Threads
... Ways to render a function thread safe Serialize the function Lock the code to keep other threads out Only one thread can be in the sensitive code at a time Lock only the critical sections of code Only let one thread update the variable at a time. Use only thread safe system functions Make function r ...
... Ways to render a function thread safe Serialize the function Lock the code to keep other threads out Only one thread can be in the sensitive code at a time Lock only the critical sections of code Only let one thread update the variable at a time. Use only thread safe system functions Make function r ...