Network Vulnerability Scanning - Texas Tech University Departments
... Summer Cyber-Security Workshop, Lubbock, July 2014 ...
... Summer Cyber-Security Workshop, Lubbock, July 2014 ...
Processes
... Stubs – client-side proxy for the actual procedure on the server The client-side stub locates the server and marshalls the parameters The server-side stub receives this message, unpacks the marshalled ...
... Stubs – client-side proxy for the actual procedure on the server The client-side stub locates the server and marshalls the parameters The server-side stub receives this message, unpacks the marshalled ...
Slide 1
... Due to the inherent uncertainty associated with gaining cyber SA, operating point estimation won’t be 100% accurate. Although the estimation problem for individual exploits has been studied in the literature, the estimation problem for multi-step attacks (a chain of exploits) under model parameter u ...
... Due to the inherent uncertainty associated with gaining cyber SA, operating point estimation won’t be 100% accurate. Although the estimation problem for individual exploits has been studied in the literature, the estimation problem for multi-step attacks (a chain of exploits) under model parameter u ...
Solution to Critical
... To introduce the critical-section problem, whose solutions can be used to ...
... To introduce the critical-section problem, whose solutions can be used to ...
Dancing with Giants: Wimpy Kernels for On-demand Isolated I/O
... sensitive applications (i.e., wimps) to dynamically connect to diverse peripheral devices of unmodified commodity OSes. Central to on-demand isolation of I/O channels is the notion of the wimpy kernel, which constructs these channels without affecting the underlying TCB; i.e., without modifying its ...
... sensitive applications (i.e., wimps) to dynamically connect to diverse peripheral devices of unmodified commodity OSes. Central to on-demand isolation of I/O channels is the notion of the wimpy kernel, which constructs these channels without affecting the underlying TCB; i.e., without modifying its ...
Principles of Operating Systems
... 9 it takes less time to switch between two threads within the same process than between two processes 9 threads within the same process share memory and files, therefore they can communicate with each other without having to invoke the kernel 9 for these reasons, threads are sometimes called “lightw ...
... 9 it takes less time to switch between two threads within the same process than between two processes 9 threads within the same process share memory and files, therefore they can communicate with each other without having to invoke the kernel 9 for these reasons, threads are sometimes called “lightw ...
Dept. of Computer Science Engineering, School of Engineering
... 6. Describe scheduling policies appropriate for both uniprocessor and multiprocessor systems. 7. Describe or apply the various disk scheduling techniques 8. Describe or apply basic algorithms associated with distributed process management 9. Design and implement a concurrent programming application ...
... 6. Describe scheduling policies appropriate for both uniprocessor and multiprocessor systems. 7. Describe or apply the various disk scheduling techniques 8. Describe or apply basic algorithms associated with distributed process management 9. Design and implement a concurrent programming application ...
A Case for High Performance Computing with Virtual
... Virtual machine (VM) technologies are experiencing a resurgence in both industry and research communities. VMs offer many desirable features such as security, ease of management, OS customization, performance isolation, checkpointing, and migration, which can be very beneficial to the performance an ...
... Virtual machine (VM) technologies are experiencing a resurgence in both industry and research communities. VMs offer many desirable features such as security, ease of management, OS customization, performance isolation, checkpointing, and migration, which can be very beneficial to the performance an ...
2. Operating Systems
... logical conclusion. It treats hardware and the operating system kernel as though they were all hardware. A virtual machine provides an interface identical to the underlying bare hardware. The operating system creates the illusion of multiple processes, each executing on its own processor with its ow ...
... logical conclusion. It treats hardware and the operating system kernel as though they were all hardware. A virtual machine provides an interface identical to the underlying bare hardware. The operating system creates the illusion of multiple processes, each executing on its own processor with its ow ...
Providing Dynamic Update in an Operating System
... In addition to the above mentioned impact on availability, dynamically updatable systems have other benefits. Such systems provide a good prototyping environment. They allow, for example, a new page replacement, file system, or network policy to be tested without rebooting. Further, in more mature s ...
... In addition to the above mentioned impact on availability, dynamically updatable systems have other benefits. Such systems provide a good prototyping environment. They allow, for example, a new page replacement, file system, or network policy to be tested without rebooting. Further, in more mature s ...
Synchronization - Operating System
... Example -1Suppose that we wanted to provide a solution to the consumerproducer problem that fills all the buffers. We can do so by having an integer count that keeps track of the number of full buffers. Initially, count is set to 0. It is incremented by the producer after it produces a new buffer a ...
... Example -1Suppose that we wanted to provide a solution to the consumerproducer problem that fills all the buffers. We can do so by having an integer count that keeps track of the number of full buffers. Initially, count is set to 0. It is incremented by the producer after it produces a new buffer a ...
comparison between smartphone operating systems
... connectivity or software installation possibilities. One example of this category is the Nokia 1100. The problem with this type of very low-end mobile phones is that it is not possible for everyone to develop applications or web content for it. However, the situation is changing as even cheaper mobi ...
... connectivity or software installation possibilities. One example of this category is the Nokia 1100. The problem with this type of very low-end mobile phones is that it is not possible for everyone to develop applications or web content for it. However, the situation is changing as even cheaper mobi ...
Secure Computer Organization and System Design (lecture 3)
... according to VMM policy. A VMM has only one allocator module, however, it accounts for most of the complexity of the VMM. It decides which system resources to provide to each VM, ensuring that two different VM’s do not get the same resource. 3. The final module type is the interpreter. For each priv ...
... according to VMM policy. A VMM has only one allocator module, however, it accounts for most of the complexity of the VMM. It decides which system resources to provide to each VM, ensuring that two different VM’s do not get the same resource. 3. The final module type is the interpreter. For each priv ...
Xen Compared to Other Hypervisors
... A critical benefit of the Xen Hypervisor is its neutrality to the various operating systems. Due to its independence, Xen is capable of allowing any operating system (Linux, Solaris, BSD, etc) to be the Domain0 thereby ensuring the widest possible use case for customers. For example, many hardware m ...
... A critical benefit of the Xen Hypervisor is its neutrality to the various operating systems. Due to its independence, Xen is capable of allowing any operating system (Linux, Solaris, BSD, etc) to be the Domain0 thereby ensuring the widest possible use case for customers. For example, many hardware m ...
Module 7: Process Synchronization
... Example -1Suppose that we wanted to provide a solution to the consumerproducer problem that fills all the buffers. We can do so by having an integer count that keeps track of the number of full buffers. Initially, count is set to 0. It is incremented by the producer after it produces a new buffer a ...
... Example -1Suppose that we wanted to provide a solution to the consumerproducer problem that fills all the buffers. We can do so by having an integer count that keeps track of the number of full buffers. Initially, count is set to 0. It is incremented by the producer after it produces a new buffer a ...
DNS Security Considerations and the Alternatives to BIND
... much information available from that site. The Dents has a very slow development history over the years. It is still in beta testing. At the time of this writing, the current release of Dents is version 0.3.1 (on July 11, 1999) [22]. Key fingerprint = AF19 FA27 2F94 998D FDB5 DE3D F8B5 06E4 A169 4E4 ...
... much information available from that site. The Dents has a very slow development history over the years. It is still in beta testing. At the time of this writing, the current release of Dents is version 0.3.1 (on July 11, 1999) [22]. Key fingerprint = AF19 FA27 2F94 998D FDB5 DE3D F8B5 06E4 A169 4E4 ...
EN 1975155
... Preemption is the ability of RTOS, which helps it to decide which task needs to be serviced, depending on resources required by the task. The tasks are done in order of their priorities. A particular task will be pre-empted, only if a task having higher priority is requested. Tasks that have higher ...
... Preemption is the ability of RTOS, which helps it to decide which task needs to be serviced, depending on resources required by the task. The tasks are done in order of their priorities. A particular task will be pre-empted, only if a task having higher priority is requested. Tasks that have higher ...
Chapter 4 - Angelfire
... It’s only when a ULT is in the active state that it is attached to a LWP (so that it will run when the kernel level thread runs) A thread may transfer to the sleeping state by invoking a synchronization primitive (chap 5) and later transfer to the runnable state when the event ...
... It’s only when a ULT is in the active state that it is attached to a LWP (so that it will run when the kernel level thread runs) A thread may transfer to the sleeping state by invoking a synchronization primitive (chap 5) and later transfer to the runnable state when the event ...
OPERATING- SYSTEM CONCEPTS with Java
... frame, it may cause a breakdown of the entire system it is running. Therefore when writing an operating system for a real-time system, the writer must be sure that his scheduling schemes don’t allow response time to exceed the time constraint. 1.11 Distinguish between the client-server and peer-to-p ...
... frame, it may cause a breakdown of the entire system it is running. Therefore when writing an operating system for a real-time system, the writer must be sure that his scheduling schemes don’t allow response time to exceed the time constraint. 1.11 Distinguish between the client-server and peer-to-p ...
Overview of Damn Small Linux
... Fits in small places—Damn Small Linux fits on a bootable business card CD. So carrying around DSL can take up as little space as a credit card in your wallet. DSL’s small size also means that, in places where there is limited storage space (such as an old hard disk or handheld device), you can devot ...
... Fits in small places—Damn Small Linux fits on a bootable business card CD. So carrying around DSL can take up as little space as a credit card in your wallet. DSL’s small size also means that, in places where there is limited storage space (such as an old hard disk or handheld device), you can devot ...
P - Bilkent University Computer Engineering Department
... – Hold and wait: a process holding at least one resource is waiting to acquire additional resources held by other processes – No preemption: a resource can be released only voluntarily by the process holding it, after that process has completed its task – Circular wait: there exists a set {P0, P1, … ...
... – Hold and wait: a process holding at least one resource is waiting to acquire additional resources held by other processes – No preemption: a resource can be released only voluntarily by the process holding it, after that process has completed its task – Circular wait: there exists a set {P0, P1, … ...
UWB CSS 430 Operating Systems: Deadlocks
... • Let n = # of processes, m = # of resources types • Available: Vector of length m. If Available[j] = k, there are k instances of resource type Rj available • Max: n x m matrix. If Max[i,j] = k, then process Pi may request at most k instances of resource type Rj • Allocation: n x m matrix. If Alloca ...
... • Let n = # of processes, m = # of resources types • Available: Vector of length m. If Available[j] = k, there are k instances of resource type Rj available • Max: n x m matrix. If Max[i,j] = k, then process Pi may request at most k instances of resource type Rj • Allocation: n x m matrix. If Alloca ...
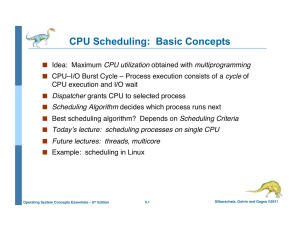
CPU Scheduling - Web Services Overview
... CPU execution and I/O wait" Dispatcher grants CPU to selected process" Scheduling Algorithm decides which process runs next" Best scheduling algorithm? Depends on Scheduling Criteria! Today’s lecture: scheduling processes on single CPU! ...
... CPU execution and I/O wait" Dispatcher grants CPU to selected process" Scheduling Algorithm decides which process runs next" Best scheduling algorithm? Depends on Scheduling Criteria! Today’s lecture: scheduling processes on single CPU! ...