The Internet Protocol - Faculty Personal Homepage
... Data Communications and Computer Networks Chapter 11 ...
... Data Communications and Computer Networks Chapter 11 ...
Flow_files/Flow Analysis and Network Hunting_7-8
... mac.addr is an optional field, specified using the -m flag. mac.addr represents the first source and destination MAC addresses seen for a particular transaction. These addresses are paired with the host.port fields, so the direction indicator is needed to distinguish between the source and destinati ...
... mac.addr is an optional field, specified using the -m flag. mac.addr represents the first source and destination MAC addresses seen for a particular transaction. These addresses are paired with the host.port fields, so the direction indicator is needed to distinguish between the source and destinati ...
Framework
... Can change default configuration with access control lists (ACLs) for ingress and egress filtering ACLs are sets of IF-THEN rules applied in sequential ...
... Can change default configuration with access control lists (ACLs) for ingress and egress filtering ACLs are sets of IF-THEN rules applied in sequential ...
Chapter 5 - Department of Computer Engineering
... A creates datagram with source A, destination B A uses ARP to get R’s MAC address for 111.111.111.110 A creates link-layer frame with R's MAC address as dest, frame contains A-to-B IP datagram A’s adapter sends frame R’s adapter receives frame R removes IP datagram from Ethernet frame, sees its dest ...
... A creates datagram with source A, destination B A uses ARP to get R’s MAC address for 111.111.111.110 A creates link-layer frame with R's MAC address as dest, frame contains A-to-B IP datagram A’s adapter sends frame R’s adapter receives frame R removes IP datagram from Ethernet frame, sees its dest ...
Interior Routing Protocols Note: exterior
... an old one fails, the routing topology may not stabilize to match the changed network topology because information propagates slowly from one router to another and while it is propagating, some routers will have incorrect routing information. Another disadvantage is that each router has to send a co ...
... an old one fails, the routing topology may not stabilize to match the changed network topology because information propagates slowly from one router to another and while it is propagating, some routers will have incorrect routing information. Another disadvantage is that each router has to send a co ...
A340105
... packet drops, even at mobility 0 makes the delay high already from the start. DSR has a much lower delay compared to AODV. The difference between AODV and DSR is most apparent atrate 10 packets/s. DSDV has the lowest delay of them all. This is however an effect from the large fraction of packet drop ...
... packet drops, even at mobility 0 makes the delay high already from the start. DSR has a much lower delay compared to AODV. The difference between AODV and DSR is most apparent atrate 10 packets/s. DSDV has the lowest delay of them all. This is however an effect from the large fraction of packet drop ...
Chapter 5 - Department of Computer Science and Engineering, CUHK
... A’s data link layer sends frame R’s data link layer receives frame R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get B’s physical layer address R creates frame containing A-to-B IP datagram sends to B ...
... A’s data link layer sends frame R’s data link layer receives frame R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get B’s physical layer address R creates frame containing A-to-B IP datagram sends to B ...
Client/Server Architecture
... Deals with and implements different data sources of Information Systems Also referred to as the data layer, which indicates that it is implemented using a Database Management System From the banking example: ...
... Deals with and implements different data sources of Information Systems Also referred to as the data layer, which indicates that it is implemented using a Database Management System From the banking example: ...
Network Performance Definitions & Analysis
... the receiver cannot process packets at the same rate that packets are arriving. ...
... the receiver cannot process packets at the same rate that packets are arriving. ...
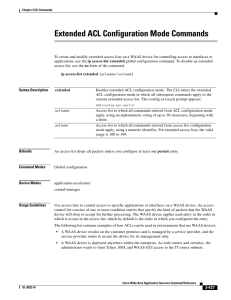
Extended ACL Configuration Mode Commands
... You must use a standard access list for providing access to the SNMP server or to the TFTP gateway/server. However, you can use either a standard access list or an extended access list for providing access to the WCCP application. To allow connections from a specific host, use the permit host source ...
... You must use a standard access list for providing access to the SNMP server or to the TFTP gateway/server. However, you can use either a standard access list or an extended access list for providing access to the WCCP application. To allow connections from a specific host, use the permit host source ...
Clean Slate Design for the Internet
... A clean separation between the substrate and an open programming environment A simple hardware substrate that generalizes, subsumes and simplifies the current substrate ...
... A clean separation between the substrate and an open programming environment A simple hardware substrate that generalizes, subsumes and simplifies the current substrate ...
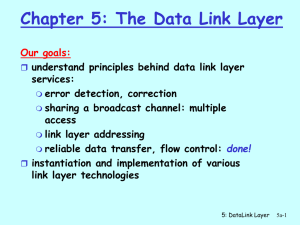
5_Data Link Layer
... Introduces “MAC” addresses used in frame headers to identify hosts (actually NICs) who are part of the network. Different for IP addresses! ...
... Introduces “MAC” addresses used in frame headers to identify hosts (actually NICs) who are part of the network. Different for IP addresses! ...
Chap 4 Router Components
... Send a packet to the destination host and then waits for a reply packet Evaluate the path-to-host reliability, delays over the path, and whether the host can be reached or is functioning ...
... Send a packet to the destination host and then waits for a reply packet Evaluate the path-to-host reliability, delays over the path, and whether the host can be reached or is functioning ...
XCAST6_WhiteBoard
... •Multicast is wasteful for small groups communication because of the routing mechanism. Another protocol that may solve this? XCAST ...
... •Multicast is wasteful for small groups communication because of the routing mechanism. Another protocol that may solve this? XCAST ...
SNMP vs CMIP
... Protocol/Internet Protocol (TCP/IP) network architecture (Burke 2004). The Common Management Information Protocol (CMIP) uses the same Management Information Base (MIB) that SNMP uses. The only difference is that there are more objects and variables to comprehend and to work with. CMIP is more effic ...
... Protocol/Internet Protocol (TCP/IP) network architecture (Burke 2004). The Common Management Information Protocol (CMIP) uses the same Management Information Base (MIB) that SNMP uses. The only difference is that there are more objects and variables to comprehend and to work with. CMIP is more effic ...
Solution
... 1. Error-reporting messages: report problems that a router or a host (destination) may encounter when it processes an IP packet. 2. Query messages: which occur in pairs, help a host or a network manager get specific information from a router or another host. For example, nodes can discover their nei ...
... 1. Error-reporting messages: report problems that a router or a host (destination) may encounter when it processes an IP packet. 2. Query messages: which occur in pairs, help a host or a network manager get specific information from a router or another host. For example, nodes can discover their nei ...
White Paper
... There are two types of periodic status traps: Traps containing dynamic data (data that changes frequently) and traps containing static or semi-static data. The send interval for traps containing dynamic data can be adjusted from the MSM web interface and ranges from once every minute to once every t ...
... There are two types of periodic status traps: Traps containing dynamic data (data that changes frequently) and traps containing static or semi-static data. The send interval for traps containing dynamic data can be adjusted from the MSM web interface and ranges from once every minute to once every t ...
NAT traversal
... Full cone NAT is NAT where all requests from the same internal IP address and port are mapped to the same public IP address and port. Once a mapping is created, all incoming traffic to the public address is routed to the internal host without checking the address of the remote host. A restricted con ...
... Full cone NAT is NAT where all requests from the same internal IP address and port are mapped to the same public IP address and port. Once a mapping is created, all incoming traffic to the public address is routed to the internal host without checking the address of the remote host. A restricted con ...
Routing - King Fahd University of Petroleum and Minerals
... Each router using distance vector routing begins by identifying its own neighbors. In the graphic, the port to each directly connected network is shown as having a distance of 0. As the distance vector network discovery process proceeds, routers discover the best path to destination networks based o ...
... Each router using distance vector routing begins by identifying its own neighbors. In the graphic, the port to each directly connected network is shown as having a distance of 0. As the distance vector network discovery process proceeds, routers discover the best path to destination networks based o ...
lecture16
... • Sending host puts destination internetworking address in the packet. • Destination addresses can be interpreted by any intermediate router/gateway. • Router/gateway examines address and forwards packet on to the destination. ...
... • Sending host puts destination internetworking address in the packet. • Destination addresses can be interpreted by any intermediate router/gateway. • Router/gateway examines address and forwards packet on to the destination. ...
Internet protocol suite

The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP, because among many protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) is the accepted and most widely used protocol in Internet. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. This functionality is organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link); the internet layer, connecting hosts across independent networks, thus establishing internetworking; the transport layer handling host-to-host communication; and the application layer, which provides process-to-process application data exchange.The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF).