Interconnection networks 2, clusters
... IP, TCP, and UDP • IP = internet protocol, used at network layer – IP routes datagrams to destination machine, makes best effort to deliver packets but does not guarantee delivery or order of datagrams – For IP, every host and router must have unique IP address • IPv4 uses 32-bit addresses • IPv6 us ...
... IP, TCP, and UDP • IP = internet protocol, used at network layer – IP routes datagrams to destination machine, makes best effort to deliver packets but does not guarantee delivery or order of datagrams – For IP, every host and router must have unique IP address • IPv4 uses 32-bit addresses • IPv6 us ...
ppt
... • Each layer relies on services from layer below and exports services to layer above • Interface defines interaction • Hides implementation - layers can change without disturbing other layers (black box) ...
... • Each layer relies on services from layer below and exports services to layer above • Interface defines interaction • Hides implementation - layers can change without disturbing other layers (black box) ...
Network Layer
... network server when it joins network Can renew its lease on address in use Allows reuse of addresses (only hold address while connected an ...
... network server when it joins network Can renew its lease on address in use Allows reuse of addresses (only hold address while connected an ...
TCP Ports
... of the program, as their book first appeared in 1933, years (decades!) before the operating system and network infrastructure were finalized. The book describes networking in terms even a child could understand, choosing to anthropomorphize the underlying packet structure. The ping packet is describ ...
... of the program, as their book first appeared in 1933, years (decades!) before the operating system and network infrastructure were finalized. The book describes networking in terms even a child could understand, choosing to anthropomorphize the underlying packet structure. The ping packet is describ ...
Chapter 18 - William Stallings, Data and Computer Communications
... depend on underlying transmission system and lower-level entities ...
... depend on underlying transmission system and lower-level entities ...
SCORE: A Scalable Architecture for Implementing Resource
... – Transport layer resistance to DoS attacks ...
... – Transport layer resistance to DoS attacks ...
Searching Extracting and Archiving Data
... To describe different protocols used at the data-link layer. ...
... To describe different protocols used at the data-link layer. ...
Slide 1
... • the transport function can issue a “not ready” indicator to the sender. When the receiver can handle additional data, the receiver sends a “ready” transport indicator. When this indicator is received, the sender can resume the segment transmission ...
... • the transport function can issue a “not ready” indicator to the sender. When the receiver can handle additional data, the receiver sends a “ready” transport indicator. When this indicator is received, the sender can resume the segment transmission ...
ch9
... • SMTP is the protocol used to transfer messages form one host to another. • Users interact with a mail reader, when they compose, file, search and read email. • There is a mail daemon (or process) running on each host, which plays the role of post office. (The mail daemon on most hosts is Unix send ...
... • SMTP is the protocol used to transfer messages form one host to another. • Users interact with a mail reader, when they compose, file, search and read email. • There is a mail daemon (or process) running on each host, which plays the role of post office. (The mail daemon on most hosts is Unix send ...
Transport Issues in Ad Hoc and Sensor Networks
... Makes it possible for the users to send and receive data without concern of network congestion or loss of packets. Ability to dynamically adjust window size to provide better flow control. ...
... Makes it possible for the users to send and receive data without concern of network congestion or loss of packets. Ability to dynamically adjust window size to provide better flow control. ...
OLD_chapter_18
... • position of fragment of user data in original datagram • in multiples of 64 bits (8 octets) ...
... • position of fragment of user data in original datagram • in multiples of 64 bits (8 octets) ...
Chapter 3 E-business infrastructure
... HTTP or Hypertext Transfer Protocol is a standard which defines the way information is transmitted across the Internet between web browsers and web servers. XML or eXtensible Markup Language A standard for transferring structured data, unlike HTML which is purely presentational. File Transfer Protoc ...
... HTTP or Hypertext Transfer Protocol is a standard which defines the way information is transmitted across the Internet between web browsers and web servers. XML or eXtensible Markup Language A standard for transferring structured data, unlike HTML which is purely presentational. File Transfer Protoc ...
Chapter 18 - William Stallings, Data and Computer
... depend on underlying transmission system and lower-level entities ...
... depend on underlying transmission system and lower-level entities ...
Lecture - 13
... i.e., network and transport layers? » Network layer is part of the communication subnet and is run by the carriers » The network layer may offer connectionoriented service which may be unreliable » The users have no control over the subnet, so the only possibility to improve the quality of service i ...
... i.e., network and transport layers? » Network layer is part of the communication subnet and is run by the carriers » The network layer may offer connectionoriented service which may be unreliable » The users have no control over the subnet, so the only possibility to improve the quality of service i ...
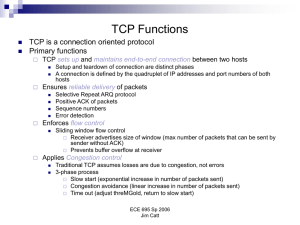
Factors that influence TCP performance
... Transmitter maintains a metric related to number of packets “in flight”. As long as this metric is less than the congestion window size, the (NACK) segments can be re-transmitted Requires both sender and receiver to maintain additional information about packets sent and received. ...
... Transmitter maintains a metric related to number of packets “in flight”. As long as this metric is less than the congestion window size, the (NACK) segments can be re-transmitted Requires both sender and receiver to maintain additional information about packets sent and received. ...
Computer Networks - Texas State Department of Computer Science
... Each computer has its own network address. A LAN is a private network and owned an operated by the company or institution. Ethernet (1970’s- Xerox PARC) operates at 10, 100, or 1000 Mbps (million bits per second, 1Gbps). Shared cable with transceivers and bridges Hubs to which every comput ...
... Each computer has its own network address. A LAN is a private network and owned an operated by the company or institution. Ethernet (1970’s- Xerox PARC) operates at 10, 100, or 1000 Mbps (million bits per second, 1Gbps). Shared cable with transceivers and bridges Hubs to which every comput ...
computer networks - Technicalsymposium
... Network Interface Cards (NIC) are working as repeaters. No starting or ending point. Each node will repeat any signal that is on the network regardless its destination. The destination station recognizes its address and copies the frame into a local buffer. The frame continues to circulate until it ...
... Network Interface Cards (NIC) are working as repeaters. No starting or ending point. Each node will repeat any signal that is on the network regardless its destination. The destination station recognizes its address and copies the frame into a local buffer. The frame continues to circulate until it ...
Internet protocol suite

The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP, because among many protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) is the accepted and most widely used protocol in Internet. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. This functionality is organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link); the internet layer, connecting hosts across independent networks, thus establishing internetworking; the transport layer handling host-to-host communication; and the application layer, which provides process-to-process application data exchange.The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF).