Voice Over IP and Security
... Security Issues (cont) IPsec AH is incompatible with NAT : address behind NAT are masked -> Encapsulating IPsec packet in a new UDP packet. Use SRTP: offers encryption, authentication and periodic refreshment of session keys. Implement strict ACL at gateways. Implement NAT behind firewalls: issues ...
... Security Issues (cont) IPsec AH is incompatible with NAT : address behind NAT are masked -> Encapsulating IPsec packet in a new UDP packet. Use SRTP: offers encryption, authentication and periodic refreshment of session keys. Implement strict ACL at gateways. Implement NAT behind firewalls: issues ...
Protecting against spear-phishing
... Facing an increasing number of threats and stricter business regulations, organisations are continually challenged with ensuring that security and compliance across the IT infrastructure is sufficient. While scams and tricks are hardly new, the speed and reach of them has been magnified enormously w ...
... Facing an increasing number of threats and stricter business regulations, organisations are continually challenged with ensuring that security and compliance across the IT infrastructure is sufficient. While scams and tricks are hardly new, the speed and reach of them has been magnified enormously w ...
MIS409_DB_Security_Auth_Encrypt
... The XACML policy language is as expressive as a natural language. For example, consider the following sentence: "A user wants to do something with an information asset in a given context". A sentence like this includes four grammatical building blocks: a subject an action a resource the environment ...
... The XACML policy language is as expressive as a natural language. For example, consider the following sentence: "A user wants to do something with an information asset in a given context". A sentence like this includes four grammatical building blocks: a subject an action a resource the environment ...
IPSEC Presentation
... • A collection of protocols for securing Internet Protocol (IP) communications by encrypting and authenticating all IP packets1 • Progressive standard • Defined in RFC 2401 thru 2409 • Purpose: – To protect IP packets – To provide defense against network attacks 1: From wikipedia.org ...
... • A collection of protocols for securing Internet Protocol (IP) communications by encrypting and authenticating all IP packets1 • Progressive standard • Defined in RFC 2401 thru 2409 • Purpose: – To protect IP packets – To provide defense against network attacks 1: From wikipedia.org ...
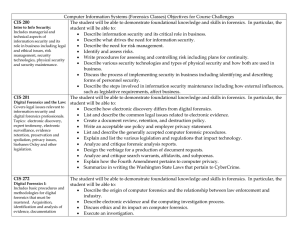
Computer Information Systems (Forensics Classes) Objectives for
... The student will be able to demonstrate foundational knowledge and skills in forensics. In particular, the student will be able to: • Compare and contrast the three basic cryptographic functions. • Describe how cryptographic functions can be used to enable security services. • Describe authenticatio ...
... The student will be able to demonstrate foundational knowledge and skills in forensics. In particular, the student will be able to: • Compare and contrast the three basic cryptographic functions. • Describe how cryptographic functions can be used to enable security services. • Describe authenticatio ...
Monitoring and Discovery - Pegasus Workflow Management System
... This should not adversely affect other users Some state (such as the user’s subscriptions) may need to be cleaned up. Some systems use soft-state to deal with this issue: ...
... This should not adversely affect other users Some state (such as the user’s subscriptions) may need to be cleaned up. Some systems use soft-state to deal with this issue: ...
Chapter 13
... Zombie—machine on which the DDoS software is loaded, unknown to the owner Home computers with cable modems or DSL service that are left on all the time Business Web servers located outside the ...
... Zombie—machine on which the DDoS software is loaded, unknown to the owner Home computers with cable modems or DSL service that are left on all the time Business Web servers located outside the ...
chapter13
... Zombie—machine on which the DDoS software is loaded, unknown to the owner Home computers with cable modems or DSL service that are left on all the time Business Web servers located outside the ...
... Zombie—machine on which the DDoS software is loaded, unknown to the owner Home computers with cable modems or DSL service that are left on all the time Business Web servers located outside the ...
SWIFT Customer Security Program
... between itself and its customers, including on suspected fraudulent activity, effective preventive and detective measures, and leading practices and innovations on cyber defenses. It will maintain an up-to-date malware inventory and curate an information sharing community. Enhance SWIFT-related tool ...
... between itself and its customers, including on suspected fraudulent activity, effective preventive and detective measures, and leading practices and innovations on cyber defenses. It will maintain an up-to-date malware inventory and curate an information sharing community. Enhance SWIFT-related tool ...
Information Theory Makes Logistic Regression Special
... is special, and unlike other regression models mentioned above. A similar approach will be used to interpret Bayes’ formula in terms of nformation. Our second goal is to propose a test of significance that in case of small samples is superior to the conventional ChiSquare test. This is important bec ...
... is special, and unlike other regression models mentioned above. A similar approach will be used to interpret Bayes’ formula in terms of nformation. Our second goal is to propose a test of significance that in case of small samples is superior to the conventional ChiSquare test. This is important bec ...
What is Penetration Testing?
... a malicious source. • The process involves an active analysis of the system for any potential vulnerabilities that may result from poor or improper system configuration, known and/or unknown hardware or software flaws, or operational weaknesses in process or technical countermeasures. • The intent o ...
... a malicious source. • The process involves an active analysis of the system for any potential vulnerabilities that may result from poor or improper system configuration, known and/or unknown hardware or software flaws, or operational weaknesses in process or technical countermeasures. • The intent o ...
11 Secure electronic communication
... Up-to-date asset register (see Section 3.1.4) Removal of all equipment and assets is formally recorded (see Section 3.11.1) Return of assets (keys and equipment) on termination of employment (see Section 3.4) Location of equipment to minimise unnecessary access (see Section 3.11.1) Network ...
... Up-to-date asset register (see Section 3.1.4) Removal of all equipment and assets is formally recorded (see Section 3.11.1) Return of assets (keys and equipment) on termination of employment (see Section 3.4) Location of equipment to minimise unnecessary access (see Section 3.11.1) Network ...
Data Encryption Standard - gozips.uakron.edu
... properties, users, and important assets Monitoring applications – utilities and applications used to monitor network traffic and Internet activities, downloads, uploads, and other network activities Auditing procedures and tools – checks and controls to ensure that security measures are working ...
... properties, users, and important assets Monitoring applications – utilities and applications used to monitor network traffic and Internet activities, downloads, uploads, and other network activities Auditing procedures and tools – checks and controls to ensure that security measures are working ...
SECURITY METRICS FOR ENTERPRISE INFORMATION SYSTEMS Interdisciplinarity – New Approaches and Perspectives
... vulnerabilities in a consistent fashion while at the same time allowing for personalization within each user environment. As CVSS matures, these metrics may expand or adjust making it even more accurate, flexible and representative of modern vulnerabilities and their risks. ...
... vulnerabilities in a consistent fashion while at the same time allowing for personalization within each user environment. As CVSS matures, these metrics may expand or adjust making it even more accurate, flexible and representative of modern vulnerabilities and their risks. ...
Internal Networks and Physical Attacks
... A secure operating environment and strict networking and access controls would be appropriate for any server that is exposed to public use and has access to internal databases. ...
... A secure operating environment and strict networking and access controls would be appropriate for any server that is exposed to public use and has access to internal databases. ...
Integrated Risk Managment for Africa (IRMA)
... situations in Africa, including advanced multiple vulnerability assessment to cope with complex emergencies. • An integrated set of tools, compliant with the above mentioned concepts and methodologies and with current and emerging international standards. ...
... situations in Africa, including advanced multiple vulnerability assessment to cope with complex emergencies. • An integrated set of tools, compliant with the above mentioned concepts and methodologies and with current and emerging international standards. ...
TLC_Requirements_TI+AlcatelLucent
... The IRRIIS project will provide a novel technology, named « MIT system » aiming at enhancing the dependability, the survivability and the resilience of LCCIs. MIT system will : ...
... The IRRIIS project will provide a novel technology, named « MIT system » aiming at enhancing the dependability, the survivability and the resilience of LCCIs. MIT system will : ...
TEL2813/IS2820 Security Management
... All Internet Control Message Protocol (ICMP) data should be denied Telnet (terminal emulation) access to all internal servers from the public networks should be blocked When Web services are offered outside the firewall, HTTP traffic should be handled by some form of proxy access or DMZ architecture ...
... All Internet Control Message Protocol (ICMP) data should be denied Telnet (terminal emulation) access to all internal servers from the public networks should be blocked When Web services are offered outside the firewall, HTTP traffic should be handled by some form of proxy access or DMZ architecture ...
Network Management Basics
... • Active attacks: masquerades (i.e., users pretending to be someone else, or • repeating, giving priority to or delaying message; (unauthorized access, viruses, Trojan horses, denial-of-service attacks). • Malfunctioning of resources. • Faulty or inappropriate behavior and incorrect response operati ...
... • Active attacks: masquerades (i.e., users pretending to be someone else, or • repeating, giving priority to or delaying message; (unauthorized access, viruses, Trojan horses, denial-of-service attacks). • Malfunctioning of resources. • Faulty or inappropriate behavior and incorrect response operati ...
Weaponized Malware
... users if their accounts had been affected by what the company believes are “state-sponsored” attacks. Google gauges the likelihood of an attack’s being state-sponsored based on analysis of the oceans of data that flows across its servers. ...
... users if their accounts had been affected by what the company believes are “state-sponsored” attacks. Google gauges the likelihood of an attack’s being state-sponsored based on analysis of the oceans of data that flows across its servers. ...
Huntsman Security updates trail-blazing cyber security analytics and
... and continuing to increase its maturity.” said Piers Wilson, Huntsman’s Head of Product Management. Peter Woollacott, Huntsman® founder and CEO, said: “Building on our proven track record of machine-learning, anomaly detection and security analytics, Huntsman® is the first vendor in the sector to re ...
... and continuing to increase its maturity.” said Piers Wilson, Huntsman’s Head of Product Management. Peter Woollacott, Huntsman® founder and CEO, said: “Building on our proven track record of machine-learning, anomaly detection and security analytics, Huntsman® is the first vendor in the sector to re ...
Information Management and Information Exploitation
... To exploit spatial information effectively, data needs to be disseminated across the breadth and depth of an organisation and with its partners, which is dependent upon the interoperability of its systems and users. We are experts in handling large volumes of data, providing and integrating private ...
... To exploit spatial information effectively, data needs to be disseminated across the breadth and depth of an organisation and with its partners, which is dependent upon the interoperability of its systems and users. We are experts in handling large volumes of data, providing and integrating private ...