What Cyber Criminals Know Most People Don`t?
... Where should you start? These three controls can help you address the top vulnerabilities and begin to reduce risk. ...
... Where should you start? These three controls can help you address the top vulnerabilities and begin to reduce risk. ...
Chapter 1
... are now commercially available. They also have may open source free tools. This proliferation of powerful tools has increased the threat of attack due to the fact that even technical novices can now launch sophisticated attacks. ...
... are now commercially available. They also have may open source free tools. This proliferation of powerful tools has increased the threat of attack due to the fact that even technical novices can now launch sophisticated attacks. ...
Copyright Infringement Policies and Sanctions
... regulations, with applicable city, state, and federal laws and regulations, and with applicable policies of the affiliated networks and systems. Each person requesting service from a PQC Telecommunications and Networking technician for equipment owned by a person or entity other than PQC must acknow ...
... regulations, with applicable city, state, and federal laws and regulations, and with applicable policies of the affiliated networks and systems. Each person requesting service from a PQC Telecommunications and Networking technician for equipment owned by a person or entity other than PQC must acknow ...
HUNTING-AS-A-SERVICE By Accenture, Powered by Endgame
... ever-increasing variety and velocity of data emanating from existing security systems makes it easier for adversaries to hide in the noise, and harder for defenders to root them out. The result is that defenders, or incident responders, at best identify the artifacts of an attack at the latest stage ...
... ever-increasing variety and velocity of data emanating from existing security systems makes it easier for adversaries to hide in the noise, and harder for defenders to root them out. The result is that defenders, or incident responders, at best identify the artifacts of an attack at the latest stage ...
Document
... In-band attack via permitted communication paths enforced by Security enforcing mechanisms Standard Operating Procedures are not followed – patches not applied ...
... In-band attack via permitted communication paths enforced by Security enforcing mechanisms Standard Operating Procedures are not followed – patches not applied ...
Chapter 1
... are dangerous because they are unexpected and can occur with very little warning Can disrupt not only the lives of individuals, but also the storage, transmission, and use of information Include fire, flood, earthquake, and lightning as well as electrostatic discharge Since it is not possible ...
... are dangerous because they are unexpected and can occur with very little warning Can disrupt not only the lives of individuals, but also the storage, transmission, and use of information Include fire, flood, earthquake, and lightning as well as electrostatic discharge Since it is not possible ...
Secure External Network Communications
... must be professionally managed. This guarantees auditability and adherence to all corporate and company computer and network security requirements. The security controls must be minimally implemented at the government-defined C2 level. This can be achieved with an access control software product, th ...
... must be professionally managed. This guarantees auditability and adherence to all corporate and company computer and network security requirements. The security controls must be minimally implemented at the government-defined C2 level. This can be achieved with an access control software product, th ...
Syllabus - Skills Commons
... Department of Labor. The Department of Labor makes no guarantees, warranties or assurances of any kind, express or implied, with respect to such information, including any information on linked sites, and including, but not limited to accuracy of the information or its completeness, timeliness, usef ...
... Department of Labor. The Department of Labor makes no guarantees, warranties or assurances of any kind, express or implied, with respect to such information, including any information on linked sites, and including, but not limited to accuracy of the information or its completeness, timeliness, usef ...
Computer Security And The Law: What You Can Do To Protect
... An inventory of all hardware and software will not only document an organization’s assets, but also serve to document all systems and software that must be protected and maintained. This inventory will aid when performing upgrades, patches, and maintenance. An inventory will help ensure that all res ...
... An inventory of all hardware and software will not only document an organization’s assets, but also serve to document all systems and software that must be protected and maintained. This inventory will aid when performing upgrades, patches, and maintenance. An inventory will help ensure that all res ...
Document
... So… Has it been working? Misuse of network access by employees was about as frequent as virus attacks, occurring in more than 75% of organizations. Theft of proprietary information occurred in over 20% of organizations, resulting in financial losses of more than $ 2.7 million on average. Deni ...
... So… Has it been working? Misuse of network access by employees was about as frequent as virus attacks, occurring in more than 75% of organizations. Theft of proprietary information occurred in over 20% of organizations, resulting in financial losses of more than $ 2.7 million on average. Deni ...
Cutting Edge VoIP Security Issues Color
... Average losses due to security breaches are up, but down significantly from 2001 and 2002 (*) The number of incidents is down (*) Incidents are being reported at a greater rate (*) ...
... Average losses due to security breaches are up, but down significantly from 2001 and 2002 (*) The number of incidents is down (*) Incidents are being reported at a greater rate (*) ...
Controlled Dissemination of Electronic Medical Records Guido van ’t Noordende Abstract
... uses references to disparate patient records. In contrast, in the U.K. NPfIT system, records are uploaded to several central databases, from which many people can access these records [2]. In Germany, information is encrypted before information is uploaded to a central infrastructure. This is much m ...
... uses references to disparate patient records. In contrast, in the U.K. NPfIT system, records are uploaded to several central databases, from which many people can access these records [2]. In Germany, information is encrypted before information is uploaded to a central infrastructure. This is much m ...
- Learn Group
... suffering damage or unintended or unauthorized modification or disclosure. When an organization’s information is stolen, it has suffered a loss. Protection profile or security posture: The entire set of controls and safeguards, including policy, education, training and awareness, and technology, tha ...
... suffering damage or unintended or unauthorized modification or disclosure. When an organization’s information is stolen, it has suffered a loss. Protection profile or security posture: The entire set of controls and safeguards, including policy, education, training and awareness, and technology, tha ...
Best Practices for Wireless LAN Security & Operational Support
... configurations out of security specs AirDefense alerted security and network ...
... configurations out of security specs AirDefense alerted security and network ...
Part 70 Permit Reissuance Application Forms Master List
... Complete form IA-01-R. This is an update to the list of insignificant activities that appears in your permit. Some permits were issued prior to the time when EPA began requiring that the insignificant activities be listed in the permit. If that is the case, you likely will have to refer to Form IA-0 ...
... Complete form IA-01-R. This is an update to the list of insignificant activities that appears in your permit. Some permits were issued prior to the time when EPA began requiring that the insignificant activities be listed in the permit. If that is the case, you likely will have to refer to Form IA-0 ...
PPT Version
... • Concept of Security Planes could be instrumental for ensuring that essential network activities are protected independently (e.g. compromise of security at the Enduser Security Plane does not affect functions associated with the Management Security Plane). • Concept of Security Planes allows to id ...
... • Concept of Security Planes could be instrumental for ensuring that essential network activities are protected independently (e.g. compromise of security at the Enduser Security Plane does not affect functions associated with the Management Security Plane). • Concept of Security Planes allows to id ...
II.I Selected Database Issues: 1
... • allow controlled access to Web site • ensure data exchanged between browser and server is secure and reliable. SSL creates a secure connection over which any amount of data can be sent securely. S-HTTP transmits individual messages only. Complementary rather than competing technologies. II.I Selec ...
... • allow controlled access to Web site • ensure data exchanged between browser and server is secure and reliable. SSL creates a secure connection over which any amount of data can be sent securely. S-HTTP transmits individual messages only. Complementary rather than competing technologies. II.I Selec ...
Cybersecurity for Critical Control Systems in the Power Industry
... Cybersecurity Framework, which will provide a costeffective approach to security measures for critical infrastructure owners to use in assessing and managing cyber risk. NIST issued a Request for Information (RFI) on February 26, 2013, as a first step in developing the Cybersecurity Framework. Thus, ...
... Cybersecurity Framework, which will provide a costeffective approach to security measures for critical infrastructure owners to use in assessing and managing cyber risk. NIST issued a Request for Information (RFI) on February 26, 2013, as a first step in developing the Cybersecurity Framework. Thus, ...
Unauthorized Access - Threats, Risk, and Control
... Once the intruders gain access to the internal network, they can approach, trespass within, communicate with, store data in or retrieve data from, interfere with, or otherwise intercept and change the system. They can: • Obstruct computer services by placing malicious programs to overload computer r ...
... Once the intruders gain access to the internal network, they can approach, trespass within, communicate with, store data in or retrieve data from, interfere with, or otherwise intercept and change the system. They can: • Obstruct computer services by placing malicious programs to overload computer r ...
Sessuib 12 2012
... Specifies where to report any know violations of the policy, and what consequences could result from such violations. For example, consequences may result in immediate suspension of user privileges, a disciplinary action, or reporting the case to appropriate law enforcement agencies. ...
... Specifies where to report any know violations of the policy, and what consequences could result from such violations. For example, consequences may result in immediate suspension of user privileges, a disciplinary action, or reporting the case to appropriate law enforcement agencies. ...
ppt
... Subject: the entitie that can perform actions in the system Object: the entitie representing resources to which access may need to be controlled Subjects and objects should both be considered as software entities, rather than as human users. Human user can only have an effect on the system via the s ...
... Subject: the entitie that can perform actions in the system Object: the entitie representing resources to which access may need to be controlled Subjects and objects should both be considered as software entities, rather than as human users. Human user can only have an effect on the system via the s ...
Vulnerability Management: Tools, Challenges and Best Practices
... engineering groups supposed to sift through security alerts and know which ones apply to them and which can be discarded?” (Gregory, par. 3). Furthermore, businesses should identify a single entity to hold responsible for inventory management to ensure consistency. Companies who are unwilling or una ...
... engineering groups supposed to sift through security alerts and know which ones apply to them and which can be discarded?” (Gregory, par. 3). Furthermore, businesses should identify a single entity to hold responsible for inventory management to ensure consistency. Companies who are unwilling or una ...
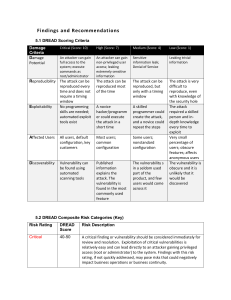
Findings and Recommendations
... high critical and severe risks have been addressed. These vulnerabilities may leak sensitive data that an attacker can use to assist in the exploitation of other vulnerabilities. Moderate findings do not pose a substantial threat to business operations. Low risk findings are informational and do not ...
... high critical and severe risks have been addressed. These vulnerabilities may leak sensitive data that an attacker can use to assist in the exploitation of other vulnerabilities. Moderate findings do not pose a substantial threat to business operations. Low risk findings are informational and do not ...