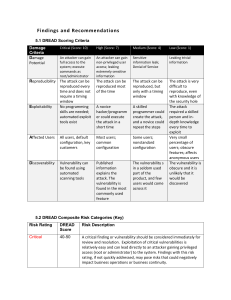
Findings and Recommendations
... high critical and severe risks have been addressed. These vulnerabilities may leak sensitive data that an attacker can use to assist in the exploitation of other vulnerabilities. Moderate findings do not pose a substantial threat to business operations. Low risk findings are informational and do not ...
... high critical and severe risks have been addressed. These vulnerabilities may leak sensitive data that an attacker can use to assist in the exploitation of other vulnerabilities. Moderate findings do not pose a substantial threat to business operations. Low risk findings are informational and do not ...
DATASHEET Malwarebytes Endpoint Security
... against exploits. Signature-less behavioral monitoring technology automatically detects and blocks unknown (zero-hour) ransomware. ...
... against exploits. Signature-less behavioral monitoring technology automatically detects and blocks unknown (zero-hour) ransomware. ...
Whitepaper: Network Penetration Testing
... Happiest Minds is focused on helping customers build Smart Secure and Connected experience by leveraging disruptive technologies like mobility, analytics, security, cloud computing, social computing and unified communications. Enterprises are embracing these technologies to implement Omni-channel st ...
... Happiest Minds is focused on helping customers build Smart Secure and Connected experience by leveraging disruptive technologies like mobility, analytics, security, cloud computing, social computing and unified communications. Enterprises are embracing these technologies to implement Omni-channel st ...
Event Title - Microsoft Center
... for IBM DB2 was run with vendor name: ‘IBM’ , and product name: ‘db2.’ Query for MySQL was run with vendor name: ‘MySQL’, and product name: ‘Any.’ Query for Microsoft was run with vendor name: ‘Microsoft ‘ ; product name: ‘Microsoft SQL Server’; version name: ’Any’ This chart counts NIST CVE – Softw ...
... for IBM DB2 was run with vendor name: ‘IBM’ , and product name: ‘db2.’ Query for MySQL was run with vendor name: ‘MySQL’, and product name: ‘Any.’ Query for Microsoft was run with vendor name: ‘Microsoft ‘ ; product name: ‘Microsoft SQL Server’; version name: ’Any’ This chart counts NIST CVE – Softw ...
F our T op
... that maximized mutual information. For example, for the average spike count constrained to lie between 1 and 10, the maximal mutual information occurred when fR ; Pr(S )g were (1; 0:42), (4:4; 0:18) and (10; 0:40). What his paper does not say is that when more than three stimuli are used to produce ...
... that maximized mutual information. For example, for the average spike count constrained to lie between 1 and 10, the maximal mutual information occurred when fR ; Pr(S )g were (1; 0:42), (4:4; 0:18) and (10; 0:40). What his paper does not say is that when more than three stimuli are used to produce ...
Data mining tools - Cal State LA
... Chief information officer (CIO) - responsible for overseeing an organization’s information resource. ...
... Chief information officer (CIO) - responsible for overseeing an organization’s information resource. ...
Information and Communication
... • One and the same message can be and usually is interpreted rather differently by separate human beings • Nevertheless, it has an invariant base shared by all or many enough: This is the information of the message • It is not formal and yet less mathematical • Information is not identical to commun ...
... • One and the same message can be and usually is interpreted rather differently by separate human beings • Nevertheless, it has an invariant base shared by all or many enough: This is the information of the message • It is not formal and yet less mathematical • Information is not identical to commun ...
Chapter 1. Introduction to Data Communications
... • Special attention must be paid to preventing viruses that attach themselves to other programs and spread when the programs are executed. • Macroviruses attach themselves to documents and become active when the files are opened are also common. Anti-virus software packages are available to check di ...
... • Special attention must be paid to preventing viruses that attach themselves to other programs and spread when the programs are executed. • Macroviruses attach themselves to documents and become active when the files are opened are also common. Anti-virus software packages are available to check di ...
spear-phishing attacks
... FireEye protects the most valuable assets in the world from those who have them in their sights. Our combination of technology, intelligence, and expertise—reinforced with the most aggressive incident response team—helps eliminate the impact of security breaches. With FireEye, you’ll detect attacks ...
... FireEye protects the most valuable assets in the world from those who have them in their sights. Our combination of technology, intelligence, and expertise—reinforced with the most aggressive incident response team—helps eliminate the impact of security breaches. With FireEye, you’ll detect attacks ...
Chapter 3 Internet and Web Security
... Availability – Assurance in the timely and reliable access to data services for authorized users (Available when required). Denial of service controls (DoS) Intrusion detection systems. ...
... Availability – Assurance in the timely and reliable access to data services for authorized users (Available when required). Denial of service controls (DoS) Intrusion detection systems. ...
Indianapolis: ITT - BS Information Systems Security (2016
... **All ITT learner transfer credit evaluations subject to individual transcript review for official transfer credit acceptance. Credit total may be fewer or more than outlined. Capella University Transfer policy can be found http://www.capella.edu/content/dam/capella/PDF/Transfer_Credit_Assessment.pd ...
... **All ITT learner transfer credit evaluations subject to individual transcript review for official transfer credit acceptance. Credit total may be fewer or more than outlined. Capella University Transfer policy can be found http://www.capella.edu/content/dam/capella/PDF/Transfer_Credit_Assessment.pd ...
ip encapsulation security payload protocol
... a monotonically increasing counter value. This help in anti-replay protection. Payload Data is variable length field, which can be used to carry cryptographic synchronization data. Padding is used when the encryption algorithm requires the plain text to be a multiple of some number of bytes. Pad Len ...
... a monotonically increasing counter value. This help in anti-replay protection. Payload Data is variable length field, which can be used to carry cryptographic synchronization data. Padding is used when the encryption algorithm requires the plain text to be a multiple of some number of bytes. Pad Len ...
Ingen bildrubrik
... POC Security System High security system combining PIN-on-Card, information security, physical access, control and alarm – all in one system ...
... POC Security System High security system combining PIN-on-Card, information security, physical access, control and alarm – all in one system ...
Illustrative Examples Threat Mitigation
... technical solutions. While organizations and sectors may develop overall Profiles, these Threat Mitigation Profile examples that illustrate how organizations may apply the Framework to mitigate specific threats. These scenarios include cybersecurity intrusion, malware, and insider threat. ...
... technical solutions. While organizations and sectors may develop overall Profiles, these Threat Mitigation Profile examples that illustrate how organizations may apply the Framework to mitigate specific threats. These scenarios include cybersecurity intrusion, malware, and insider threat. ...
An Introduction to NIST Special Publication 800
... When tackling FISMA compliance (800-53) in 2012, Pitt chose a similar model to Notre Dame in which it created a FISMA-compliant private cloud in the data center. This model allowed Pitt to quickly onboard research contracts that required FISMA Moderate or Low compliance, without impacting the larger ...
... When tackling FISMA compliance (800-53) in 2012, Pitt chose a similar model to Notre Dame in which it created a FISMA-compliant private cloud in the data center. This model allowed Pitt to quickly onboard research contracts that required FISMA Moderate or Low compliance, without impacting the larger ...
Application of CYBEX (Cybersecurity Information Exchange)
... Ian Bryant of the EU NEISAS Project described the challenges in sharing security information for infrastructure protection Takeshi Takahashi of NICT described an ontological approach for cybersecurity information haring, especially for Cloud Computing Thomas Millar of the US-CERT presented an operat ...
... Ian Bryant of the EU NEISAS Project described the challenges in sharing security information for infrastructure protection Takeshi Takahashi of NICT described an ontological approach for cybersecurity information haring, especially for Cloud Computing Thomas Millar of the US-CERT presented an operat ...
TECHNOLOGY-DRIVEN METRICS
... infections/month Rate of finding illegal software, hardware Security awareness training averages ...
... infections/month Rate of finding illegal software, hardware Security awareness training averages ...
Forcepoint™ Stonesoft Next Generation Firewall
... intellectual property, customer information, and other sensitive data, causing irreparable damage to businesses and reputations. Some attackers use advanced evasion techniques (AETs) that are able to bypass most of today’s security devices. AETs deliver malware piece meal across network layers or pr ...
... intellectual property, customer information, and other sensitive data, causing irreparable damage to businesses and reputations. Some attackers use advanced evasion techniques (AETs) that are able to bypass most of today’s security devices. AETs deliver malware piece meal across network layers or pr ...
Systems Analysis
... Importance of Conceptual Modelling Independence from physical implementation ...
... Importance of Conceptual Modelling Independence from physical implementation ...
Document
... infections/month Rate of finding illegal software, hardware Security awareness training averages ...
... infections/month Rate of finding illegal software, hardware Security awareness training averages ...
Security and Availability of Client Data
... that only access to both live data and reporting data is given to the appropriate employees. Access to the Adobe Live Network environment is granted only after sufficient business justification for such access has been provided, successful passing of a background check, and appropriate written appro ...
... that only access to both live data and reporting data is given to the appropriate employees. Access to the Adobe Live Network environment is granted only after sufficient business justification for such access has been provided, successful passing of a background check, and appropriate written appro ...
Detection of the security mechanism` violations and other
... hours). With right mouse button click an administrator can read attacks performed by an intruder, services which have been attacked and time of attacks as well as other related data (such as protection system reaction). In order to further explain events, an administrator can analyze sessions relate ...
... hours). With right mouse button click an administrator can read attacks performed by an intruder, services which have been attacked and time of attacks as well as other related data (such as protection system reaction). In order to further explain events, an administrator can analyze sessions relate ...
Privacy Policy - Dickey`s Barbecue Pit
... To choose not to have your transactional information given to, or used by, our third-party advertising partner in this way, please contact communicationservices@dickeys.com. We may also use or disclose information to resolve dispute or investigate problems. We may disclose or access information whe ...
... To choose not to have your transactional information given to, or used by, our third-party advertising partner in this way, please contact communicationservices@dickeys.com. We may also use or disclose information to resolve dispute or investigate problems. We may disclose or access information whe ...