CS244a: An Introduction to Computer Networks
... The link layer delivers data between two machines that are directly connected using a link ...
... The link layer delivers data between two machines that are directly connected using a link ...
Chapter 2 Protocols and TCP/IP
... Need For Protocol Architecture • E.g. File transfer —Source must activate comms. Path or inform network of destination —Source must check destination is prepared to receive —File transfer application on source must check destination file management system will accept and store file for his user —Ma ...
... Need For Protocol Architecture • E.g. File transfer —Source must activate comms. Path or inform network of destination —Source must check destination is prepared to receive —File transfer application on source must check destination file management system will accept and store file for his user —Ma ...
Computer Networks
... • Communication takes place between peer layers – Virtual comms: eg bt layer 3 and layer 3 – Actual comms: down/up the stack ...
... • Communication takes place between peer layers – Virtual comms: eg bt layer 3 and layer 3 – Actual comms: down/up the stack ...
internet overview lecture slides
... request goes to a root nameserver to find out where the appropriate top level domain server (.edu) is, then that server is queried as to where the host (buffalo) is, then the host is queried for the address of the actual computer in question (mediastudy) ...
... request goes to a root nameserver to find out where the appropriate top level domain server (.edu) is, then that server is queried as to where the host (buffalo) is, then the host is queried for the address of the actual computer in question (mediastudy) ...
Basic Networking Terminology
... frequency bands 14. a physical location that offers Internet access over a wireless local area network 16. a computer network that interconnects computers within a limited area such as a home, school, or office. 17. allows computers to automatically request and be assigned IP addresses and other net ...
... frequency bands 14. a physical location that offers Internet access over a wireless local area network 16. a computer network that interconnects computers within a limited area such as a home, school, or office. 17. allows computers to automatically request and be assigned IP addresses and other net ...
Chapter 4 : TCP/IP and OSI
... information are called protocols • Defines a set of rules that govern the exchange of data • Includes syntax, semantics, and timing ...
... information are called protocols • Defines a set of rules that govern the exchange of data • Includes syntax, semantics, and timing ...
Week 1 - DePaul University
... Semantics Control information for coordination Error handling Timing Speed matching (between sender and receiver) Sequencing (the right commands in the right order – closely related to semantics) ...
... Semantics Control information for coordination Error handling Timing Speed matching (between sender and receiver) Sequencing (the right commands in the right order – closely related to semantics) ...
CPSC 155a Lecture 3
... Transport: provides process-to-process semantics such as in-order-delivery and reliability, at the unit of messages • Top three layers are not well-defined, all have to do with application level abstractions such as transformation of different data formats ...
... Transport: provides process-to-process semantics such as in-order-delivery and reliability, at the unit of messages • Top three layers are not well-defined, all have to do with application level abstractions such as transformation of different data formats ...
Chapter 4
... supported by The International Development Plan (IDP), to communicate with the University of Melbourne by e-mail. ...
... supported by The International Development Plan (IDP), to communicate with the University of Melbourne by e-mail. ...
Tcp/ip
... passes down through the layers of the protocol and then back up through the layers on the server side, as shown on the previous slide • This means that the last action that takes place in the Link layer on the client computer becomes the first action in the Link layer in the server – this is an exam ...
... passes down through the layers of the protocol and then back up through the layers on the server side, as shown on the previous slide • This means that the last action that takes place in the Link layer on the client computer becomes the first action in the Link layer in the server – this is an exam ...
Class Power Points for Chapter #2
... An IP address is a numeric identifier assigned to each machine on an IP network. It designates the specific location of a device on the network. IP addressing was designed to allow hosts on one network to communicate with a host on a different network regardless of the type of LANs the hosts are par ...
... An IP address is a numeric identifier assigned to each machine on an IP network. It designates the specific location of a device on the network. IP addressing was designed to allow hosts on one network to communicate with a host on a different network regardless of the type of LANs the hosts are par ...
No Slide Title
... that connects to the network segment that it needs. • The default gateway’s IP address must be in the same network segment as the host is on. ...
... that connects to the network segment that it needs. • The default gateway’s IP address must be in the same network segment as the host is on. ...
Ethernet, IP and TCP
... protocol provides for transmitting blocks of data called datagrams from sources to destinations. The Internet protocol also provides for fragmentation and reassembly of long datagram, if necessary, for transmission through 'small packet' networks.” • “There are no mechanisms to augment end-toend dat ...
... protocol provides for transmitting blocks of data called datagrams from sources to destinations. The Internet protocol also provides for fragmentation and reassembly of long datagram, if necessary, for transmission through 'small packet' networks.” • “There are no mechanisms to augment end-toend dat ...
ppt file
... It assigns private node addresses to IPC processes It internally maps app/service name to node address ...
... It assigns private node addresses to IPC processes It internally maps app/service name to node address ...
William Stallings Data and Computer Communications
... Ñ Dependent on type of network used (LAN, packet switched etc.) ...
... Ñ Dependent on type of network used (LAN, packet switched etc.) ...
(M1) why are protocols important
... include quotes and referencing from other web sites to support your arguments. (Essential at undergraduate level so get used to working this way) ...
... include quotes and referencing from other web sites to support your arguments. (Essential at undergraduate level so get used to working this way) ...
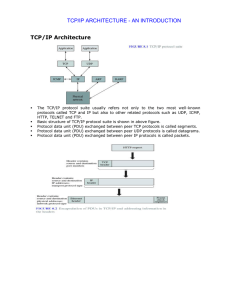
TCP/IP Architecture TCP/IP ARCHITECTURE
... Example: Ethernet uses 48-bit addresses o Each Ethernet network interface card (NIC) has globally unique Medium Access Control (MAC) or physical address o First 24 bits identify NIC manufacturer; second 24 bits are serial number o 00:90:27:96:68:07 12 hex numbers ...
... Example: Ethernet uses 48-bit addresses o Each Ethernet network interface card (NIC) has globally unique Medium Access Control (MAC) or physical address o First 24 bits identify NIC manufacturer; second 24 bits are serial number o 00:90:27:96:68:07 12 hex numbers ...
Chapter03
... Internet Control Message Protocol (ICMP) works at the Network layer and is used by IP for many different services. •ICMP is a management protocol and messaging service provider for IP. •Its messages are carried as IP datagrams. ICMP packets have the following characteristics: • They can provide host ...
... Internet Control Message Protocol (ICMP) works at the Network layer and is used by IP for many different services. •ICMP is a management protocol and messaging service provider for IP. •Its messages are carried as IP datagrams. ICMP packets have the following characteristics: • They can provide host ...
Network Protocols
... devices in an IP network •No two computers on the Internet can have the same IP address ...
... devices in an IP network •No two computers on the Internet can have the same IP address ...
投影片 1
... Error-checking values help the receiver detect when received data doesn’t match what was sent. Flow-control information helps the sender determine when the receiver is ready for more data. And a value that identifies an application-level port, or process, can help in routing received data to the c ...
... Error-checking values help the receiver detect when received data doesn’t match what was sent. Flow-control information helps the sender determine when the receiver is ready for more data. And a value that identifies an application-level port, or process, can help in routing received data to the c ...
Wireless Audio Conferencing System (WACS)
... Why we used RTP? TCP is not an appropriate choice for carrying real-time multimedia contents ...
... Why we used RTP? TCP is not an appropriate choice for carrying real-time multimedia contents ...
MIST Multicast Implementation Study
... applications which use network (e.g.: H1 router: computer (often w/o applications-level programs) routing packets from input line to output line. (e.g., A->C) gateway: router directly connected to 2+ networks (e.g. A) network: set of node (hosts/routers/gateways) within single administrative domain ...
... applications which use network (e.g.: H1 router: computer (often w/o applications-level programs) routing packets from input line to output line. (e.g., A->C) gateway: router directly connected to 2+ networks (e.g. A) network: set of node (hosts/routers/gateways) within single administrative domain ...
Networking and communication
... transport layer The OS adds a TCP header that identify the source and destination ports, forming a TCP segment, and sends that to the network layer In the network layer, an IP header identifying the source and destination systems are added, which gets sent to the link layer The link layer appe ...
... transport layer The OS adds a TCP header that identify the source and destination ports, forming a TCP segment, and sends that to the network layer In the network layer, an IP header identifying the source and destination systems are added, which gets sent to the link layer The link layer appe ...
Week 4: Monetary Transactions in Ecommerce
... sending end and reassembly (reconstructing the original message into a single whole) at the receiving end. • The network layer is responsible for addressing and routing of the message. • The network and transport layers also perform encapsulation of message segments from the application layer, passi ...
... sending end and reassembly (reconstructing the original message into a single whole) at the receiving end. • The network layer is responsible for addressing and routing of the message. • The network and transport layers also perform encapsulation of message segments from the application layer, passi ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.