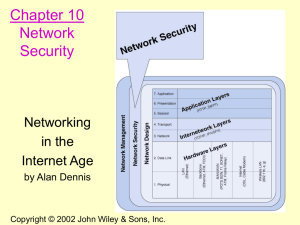
Security Aspects of Internet Related Software Engineering
... • The development process • The organization and the team ...
... • The development process • The organization and the team ...
IP Convergence - Labs
... each class of service usage • You could support both high resilience high quality real time and various profiles of data services, and all points in between within a common switched network platform • You only needed a single protocol, a single carriage architecture and a single OSS to drive the ent ...
... each class of service usage • You could support both high resilience high quality real time and various profiles of data services, and all points in between within a common switched network platform • You only needed a single protocol, a single carriage architecture and a single OSS to drive the ent ...
for ResNet - University of Michigan
... • Efficient use of IP space • Students are not required to know the MAC address of their NIC • Contact/location info is gathered from reliable source rather than having students or consultants enter the data • Requires very little administration time beyond initial configuration of networks ...
... • Efficient use of IP space • Students are not required to know the MAC address of their NIC • Contact/location info is gathered from reliable source rather than having students or consultants enter the data • Requires very little administration time beyond initial configuration of networks ...
Network Registration – Summer 2014 - Orientation
... What is network registration and why is it required? All computing devices connecting to the University of Chicago network within the residence halls must complete the network registration process before getting full internet access. Registration is an important part of network security, and can add ...
... What is network registration and why is it required? All computing devices connecting to the University of Chicago network within the residence halls must complete the network registration process before getting full internet access. Registration is an important part of network security, and can add ...
Brad`s Lecture on networks
... PC • NIC converts between networks, which transmit serial data (1 bit at a time) and PCs, which transmit parallel data (8 bits at a time) ...
... PC • NIC converts between networks, which transmit serial data (1 bit at a time) and PCs, which transmit parallel data (8 bits at a time) ...
Session5-Group4-Networking
... A string of characters used to specify where an identified resource is available and the mechanism for retrieving it. e.g. ...
... A string of characters used to specify where an identified resource is available and the mechanism for retrieving it. e.g. ...
Policy Manual Table of Contents
... Unemployment Insurance Benefits Medical Confidentiality Returning to Work Compassionate Leave Bereavement Court Duties Special Leave Termination of Employment Vacation Entitlement Carry Over Scheduling Cash Payment for Holiday Time Illness during Vacation Office Closure Forced Closure Statutory Holi ...
... Unemployment Insurance Benefits Medical Confidentiality Returning to Work Compassionate Leave Bereavement Court Duties Special Leave Termination of Employment Vacation Entitlement Carry Over Scheduling Cash Payment for Holiday Time Illness during Vacation Office Closure Forced Closure Statutory Holi ...
Introduction - Seattle University
... How to measure scalability of a system? By system size: scale to more users and resources added to the system By geography: geographically scalable in that users and resources are distributed across the Internet By administration: administratively scalable, spanning many independent administ ...
... How to measure scalability of a system? By system size: scale to more users and resources added to the system By geography: geographically scalable in that users and resources are distributed across the Internet By administration: administratively scalable, spanning many independent administ ...
The Application Layers :On Demand Lecture (Part I)
... VPNs require an in-depth understanding of public network security issues and proper deployment of precautions Availability and performance depends on factors largely outside of their control Immature standards ...
... VPNs require an in-depth understanding of public network security issues and proper deployment of precautions Availability and performance depends on factors largely outside of their control Immature standards ...
The Challenge in Developing an SCA Compliant Security
... Eleven legacy waveforms in addition to the WNW ...
... Eleven legacy waveforms in addition to the WNW ...
Chapter 1. Introduction to Data Communications
... pass through it, only allowing packets that have acceptable addresses to pass. • Since each packet is examined separately, the firewall can’t understand what the sender’s goal is. • Packet filters may be vulnerable to IP spoofing, accomplished by changing the source address on incoming packets from ...
... pass through it, only allowing packets that have acceptable addresses to pass. • Since each packet is examined separately, the firewall can’t understand what the sender’s goal is. • Packet filters may be vulnerable to IP spoofing, accomplished by changing the source address on incoming packets from ...
Lesson 1
... cables; device used to carry the signal A receiving device; usually a computer Communications software ...
... cables; device used to carry the signal A receiving device; usually a computer Communications software ...
Valiant Load-Balancing in Backbone Networks
... Each packet needs look up only once in the backbone Each flow is evenly split over N paths Routing decisions are local ...
... Each packet needs look up only once in the backbone Each flow is evenly split over N paths Routing decisions are local ...
Kraig Welsh Resume
... Part Time Computer Support/Customer Service Specialist • Provided diagnostics and repair of computers and electronics • Checked out customers via cash register after repairs were completed • Shipped equipment under warranty to main offices for repair AFNI, Tucson, AZ, 2005-2006 Customer Service Repr ...
... Part Time Computer Support/Customer Service Specialist • Provided diagnostics and repair of computers and electronics • Checked out customers via cash register after repairs were completed • Shipped equipment under warranty to main offices for repair AFNI, Tucson, AZ, 2005-2006 Customer Service Repr ...
Telecommunications and Networking - University of Baltimore Home
... – "a group of interconnected computers, workstations, or computer devices (such as printers and data storage systems).” ...
... – "a group of interconnected computers, workstations, or computer devices (such as printers and data storage systems).” ...
Document
... DCs can be physically replicated Test - 8,000 IP addresses for 34 hours – 47 million packets, 21,000 DNS requests, 150,000 TCP connections – Peak: only 200 requests/sec on DC • Test DC can handle 40x this traffic ...
... DCs can be physically replicated Test - 8,000 IP addresses for 34 hours – 47 million packets, 21,000 DNS requests, 150,000 TCP connections – Peak: only 200 requests/sec on DC • Test DC can handle 40x this traffic ...
FMAudit Technical White Paper Product Line Overview
... the Simple Network Management Protocol (SNMP). SNMP is a network protocol that facilitates the exchange of information between network devices; extracting data from the Management Information Base (MIB) and other locations within the print device. The MIB is basically an internal database that all n ...
... the Simple Network Management Protocol (SNMP). SNMP is a network protocol that facilitates the exchange of information between network devices; extracting data from the Management Information Base (MIB) and other locations within the print device. The MIB is basically an internal database that all n ...
Part 2. Logical Network Design
... The purpose of a DMZ is to add an additional layer of security to an organization's local area network (LAN); an external attacker only has access to equipment in the DMZ, rather than any other part of the network. In a computer network, the hosts most vulnerable to attack are those that provide ser ...
... The purpose of a DMZ is to add an additional layer of security to an organization's local area network (LAN); an external attacker only has access to equipment in the DMZ, rather than any other part of the network. In a computer network, the hosts most vulnerable to attack are those that provide ser ...
Chapter 4 - HFT 3444
... It allows the storing of information in a centralized database that may be shared by a few users in a small computer network or by thousands of users in a large computer network. It facilitates centralized management and decentralized operations (e.g., restaurant chain). ...
... It allows the storing of information in a centralized database that may be shared by a few users in a small computer network or by thousands of users in a large computer network. It facilitates centralized management and decentralized operations (e.g., restaurant chain). ...
Datanet Studiu de caz
... Administrative and operational tasks to permit user and device to access the network are slow and heavy due to: q q q ...
... Administrative and operational tasks to permit user and device to access the network are slow and heavy due to: q q q ...
Course name Code/No Units Credit Units Prerequisite Lecture Lab
... List some different protocol attacks to which TCP/IP is susceptible. Describe how the different protocol attacks (e.g. TCP/IP) works against an organization’s network. Give examples of shared concerns across a specified set of security domains. Give examples of concerns that are specific to specifie ...
... List some different protocol attacks to which TCP/IP is susceptible. Describe how the different protocol attacks (e.g. TCP/IP) works against an organization’s network. Give examples of shared concerns across a specified set of security domains. Give examples of concerns that are specific to specifie ...
Understanding Network Technology
... You may take the final course test up to 3 times. Format and Schedule: The course is delivered online via the SCTE virtual classroom over 16 weeks or 4 months, during which participants view web based course materials and complete assessments (quizzes) at a time that is convenient for them. Particip ...
... You may take the final course test up to 3 times. Format and Schedule: The course is delivered online via the SCTE virtual classroom over 16 weeks or 4 months, during which participants view web based course materials and complete assessments (quizzes) at a time that is convenient for them. Particip ...