Internet Applications - Guru Ghasidas Vishwavidyalaya
... In response to the threat of nuclear attack, ARPANET was designed to allow continued communication if one or more sites were destroyed. Unlike today, when millions of people have access to the Internet from home, work, or their public library, ARPANET served only computer professionals, engineers, a ...
... In response to the threat of nuclear attack, ARPANET was designed to allow continued communication if one or more sites were destroyed. Unlike today, when millions of people have access to the Internet from home, work, or their public library, ARPANET served only computer professionals, engineers, a ...
Basic Internet Technology in Support of Communication Services
... Subject of this Book Communications is a very broad subject. At one time, a distinction might have been made between computer communications (data networking) and telecommunications (public voice networking). However these two domains are rapidly converging, with the same network technologies being ...
... Subject of this Book Communications is a very broad subject. At one time, a distinction might have been made between computer communications (data networking) and telecommunications (public voice networking). However these two domains are rapidly converging, with the same network technologies being ...
Tracking and Mitigation of Malicious Remote Control
... goal of the attacker is to compromise the victim’s machine and obtain control over it. This machine is then used to carry out denial-of-service attacks, to send out spam mails, or for other nefarious purposes. From an attacker’s point of view, this kind of attack is even more efficient if she manage ...
... goal of the attacker is to compromise the victim’s machine and obtain control over it. This machine is then used to carry out denial-of-service attacks, to send out spam mails, or for other nefarious purposes. From an attacker’s point of view, this kind of attack is even more efficient if she manage ...
PLCsecurity_@_ABT-ABOC_20070122 - Indico
... ► I can stop any PLC at CERN. ► I can modify its contents. ► I just need an Ethernet connection to it. ► I (engineer, operator) might have finger-trouble. ► I (virus) do not care that it’s a PLC. ► I (attacker) might do this on purpose. ...
... ► I can stop any PLC at CERN. ► I can modify its contents. ► I just need an Ethernet connection to it. ► I (engineer, operator) might have finger-trouble. ► I (virus) do not care that it’s a PLC. ► I (attacker) might do this on purpose. ...
Building a Secure Computer System
... Strict procedures for access to the machine room are used by most organizations, and these procedures are often an organization’s only obvious computer security measures. Today, however, with pervasive remote terminal access, communications, and networking, physical measures rarely provide meaningfu ...
... Strict procedures for access to the machine room are used by most organizations, and these procedures are often an organization’s only obvious computer security measures. Today, however, with pervasive remote terminal access, communications, and networking, physical measures rarely provide meaningfu ...
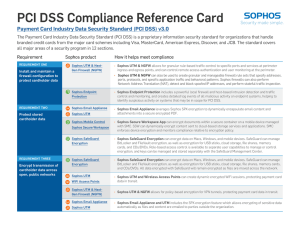
PCI DSS Compliance Reference Card
... ÌÌ Sophos UTM & NGFW can also be used to create granular and manageable firewall rule sets that specify addresses, ports, protocols, and specific application traffic and behavioral patterns. Sophos firewalls can also perform Network Address Translation (NAT), detect and block spoofed IP addresses, a ...
... ÌÌ Sophos UTM & NGFW can also be used to create granular and manageable firewall rule sets that specify addresses, ports, protocols, and specific application traffic and behavioral patterns. Sophos firewalls can also perform Network Address Translation (NAT), detect and block spoofed IP addresses, a ...
destroy faq - Destroy and Destroy Lite
... Additionally to ensure that Destroy operates without interference, unintentional or otherwise, we require Destroy to be run from booted media that ensures no other software is running at the time. It is possible that other systems such as virus scanners or hacking tools could interfere with the inte ...
... Additionally to ensure that Destroy operates without interference, unintentional or otherwise, we require Destroy to be run from booted media that ensures no other software is running at the time. It is possible that other systems such as virus scanners or hacking tools could interfere with the inte ...
bypass Internet censorship
... The kinds of people and institutions who try to restrict the Internet use of specific people are as varied as their goals. They include parents, schools, commercial companies, operators of Internet cafés or Internet Service Providers (ISPs), and governments at different levels. The extreme end of th ...
... The kinds of people and institutions who try to restrict the Internet use of specific people are as varied as their goals. They include parents, schools, commercial companies, operators of Internet cafés or Internet Service Providers (ISPs), and governments at different levels. The extreme end of th ...
HOW TO BECOME THE WORLD`S NO .1 HACKER
... Every day, we hear and see in the news about constant cyber attacks, where hackers have stolen identities, taken millions of dollars, or even shut down websites and companies in their entirety. The reason why hacking will never die is because we hire IT-Managers, who are not hackers, to protect our ...
... Every day, we hear and see in the news about constant cyber attacks, where hackers have stolen identities, taken millions of dollars, or even shut down websites and companies in their entirety. The reason why hacking will never die is because we hire IT-Managers, who are not hackers, to protect our ...
Traveling the Internet
... technology is demonstrated by the ability to share: sharing information, collaborating, the action of connecting people and their ideas.” This vision, which inspired the expression, “The Network Is The Computer,” continues to connect people beyond their desktop, and challenge technologies to provide ...
... technology is demonstrated by the ability to share: sharing information, collaborating, the action of connecting people and their ideas.” This vision, which inspired the expression, “The Network Is The Computer,” continues to connect people beyond their desktop, and challenge technologies to provide ...
HPE Cloud-First reference architecture guide
... Today’s enterprise data center network architects and managers are expected to build networks that can concurrently consolidate and geographically distribute resources, which can include virtual and physical application servers, data storage, management platforms and network devices. These expectati ...
... Today’s enterprise data center network architects and managers are expected to build networks that can concurrently consolidate and geographically distribute resources, which can include virtual and physical application servers, data storage, management platforms and network devices. These expectati ...
Ingate Firewall & SIParator Training
... What Other IP-PBXs Vendors Do Most all IP-PBX vendors recommend the use of some sort of “SIP-Aware Firewall” for deployment ...
... What Other IP-PBXs Vendors Do Most all IP-PBX vendors recommend the use of some sort of “SIP-Aware Firewall” for deployment ...
CCNP 2 Version 5 Module 5 - Cisco Device Hardening Module 5
... The open nature of the Internet makes it increasingly important for growing businesses to pay attention to the security of their networks. As companies move more of their business functions to the public network, they need to take precautions to ensure that attackers do not compromise their data or ...
... The open nature of the Internet makes it increasingly important for growing businesses to pay attention to the security of their networks. As companies move more of their business functions to the public network, they need to take precautions to ensure that attackers do not compromise their data or ...
Chapter16-PresentationDistilled
... routinely adopted by governments and corporations the world over. These standards are very comprehensive, outlining the need for risk assessment and management, security policy, and business continuity to address the triad. This chapter touches on some of those key ideas that are most applicable to ...
... routinely adopted by governments and corporations the world over. These standards are very comprehensive, outlining the need for risk assessment and management, security policy, and business continuity to address the triad. This chapter touches on some of those key ideas that are most applicable to ...
Binding Authentication to Provisioning
... applications that require authentication before a user can use them. Currently, a common situation is that users who want to access a network, like the internet, need to give their username and password in order to use the network2. This is called Authenticated Access Control: there is control over ...
... applications that require authentication before a user can use them. Currently, a common situation is that users who want to access a network, like the internet, need to give their username and password in order to use the network2. This is called Authenticated Access Control: there is control over ...
Era of Spybots - A Secure Design Solution Using
... All workstation traffic is unrestricted between their ...
... All workstation traffic is unrestricted between their ...
CSCE 790 – Secure Database Systems
... against a Member of the United Nations, until the Security Council has taken measures necessary to maintain international peace and security. Measures taken by Members in the exercise of this right of self-defense shall be immediately reported to the Security Council and shall not in any way affect ...
... against a Member of the United Nations, until the Security Council has taken measures necessary to maintain international peace and security. Measures taken by Members in the exercise of this right of self-defense shall be immediately reported to the Security Council and shall not in any way affect ...
Slide 1
... Lack authenticity and integrity checking of the data held within the DNS make it not secure. ...
... Lack authenticity and integrity checking of the data held within the DNS make it not secure. ...
Desktop microcomputers first became popular and widespread in
... information. In a multitasked environment, applications share the use of the processor by a method known as "time slicing". The application programs are written to give up the processor after a set amount of time so that other programs that are running simultaneously can use it. If the program is po ...
... information. In a multitasked environment, applications share the use of the processor by a method known as "time slicing". The application programs are written to give up the processor after a set amount of time so that other programs that are running simultaneously can use it. If the program is po ...
Network Security (Firewall)
... A stateful inspection firewall combines aspects of a packet-filtering firewall, a circuit-level gateway, and an application-level gateway. Like a packet-filtering firewall, a stateful inspection firewall operates at the network layer of the OSI model, filtering all incoming and outgoing packets base ...
... A stateful inspection firewall combines aspects of a packet-filtering firewall, a circuit-level gateway, and an application-level gateway. Like a packet-filtering firewall, a stateful inspection firewall operates at the network layer of the OSI model, filtering all incoming and outgoing packets base ...
The Internet and Its Uses
... Most organization LANs are Ethernet networks On Ethernet-based networks, any machine on the network can see the traffic for every machine on that network Sniffer programs exploit this characteristic, monitoring all traffic and capturing the first 128 bytes or so of every unencrypted FTP or Tel ...
... Most organization LANs are Ethernet networks On Ethernet-based networks, any machine on the network can see the traffic for every machine on that network Sniffer programs exploit this characteristic, monitoring all traffic and capturing the first 128 bytes or so of every unencrypted FTP or Tel ...
NPort 5400 Series User`s Manual
... Moxa provides this document “as is,” without warranty of any kind, either expressed or implied, including, but not limited to, its particular purpose. Moxa reserves the right to make improvements and/or changes to this manual, or to the products and/or the programs described in this manual, at any t ...
... Moxa provides this document “as is,” without warranty of any kind, either expressed or implied, including, but not limited to, its particular purpose. Moxa reserves the right to make improvements and/or changes to this manual, or to the products and/or the programs described in this manual, at any t ...
Windows 7 Advanced Training Manual
... Lesson 1.1: Meet the Control Panel Welcome to CSULB’s Windows 7 Advanced Courseware! In this manual we will expand on the functionality of your computer, its networking and communication abilities, and cover more advanced topics relating to your computer and the workings of an operating system. To b ...
... Lesson 1.1: Meet the Control Panel Welcome to CSULB’s Windows 7 Advanced Courseware! In this manual we will expand on the functionality of your computer, its networking and communication abilities, and cover more advanced topics relating to your computer and the workings of an operating system. To b ...