Implementation of a PCI based gigabit Ethernet device driver
... and higher speeds. In order to meet these increasing demands, more efficient ways to handle traffic are needed. The limiting factor today is not link speed but rather processing speed of the routers and end stations in the network. Here at ISY research is performed on network processors. In order to ...
... and higher speeds. In order to meet these increasing demands, more efficient ways to handle traffic are needed. The limiting factor today is not link speed but rather processing speed of the routers and end stations in the network. Here at ISY research is performed on network processors. In order to ...
Basics of Networking
... The concept of how a modern day network operates can be understood by dissecting it into seven layers. This seven layer model is known as the OSI Reference Model and defines how the vast majority of the digital networks on earth function. OSI is the acronym for Open Systems Interconnection, which wa ...
... The concept of how a modern day network operates can be understood by dissecting it into seven layers. This seven layer model is known as the OSI Reference Model and defines how the vast majority of the digital networks on earth function. OSI is the acronym for Open Systems Interconnection, which wa ...
SNMP
... • SNMP is the prevailing standard for management of TCP/IP networks. SNMP is layered on top of UDP, the User Datagram Protocol. • An SNMP management station monitors and controls a managed node by issuing requests directed to the agent residing in the managed node. The agent interprets the request a ...
... • SNMP is the prevailing standard for management of TCP/IP networks. SNMP is layered on top of UDP, the User Datagram Protocol. • An SNMP management station monitors and controls a managed node by issuing requests directed to the agent residing in the managed node. The agent interprets the request a ...
Abstract - Chennaisunday.com
... (IDAGs) and developed a methodology for resilient multipath routing using two IDAGs. We developed polynomial-time algorithms to construct nodeindependent and link-independent DAGs using all possible edges in the network. The IDAGs approach was evaluated on four real-life network topologies and compa ...
... (IDAGs) and developed a methodology for resilient multipath routing using two IDAGs. We developed polynomial-time algorithms to construct nodeindependent and link-independent DAGs using all possible edges in the network. The IDAGs approach was evaluated on four real-life network topologies and compa ...
Course Syllabus for Advanced PC Configuration
... Experimentation It has been said that experimentation is the basis for all good research. This instance is no different. In order to find the maximum level of performance for your BIOS and chipset, you will have to tweak the settings, reboot the computer, and see what happens. If it works, then brav ...
... Experimentation It has been said that experimentation is the basis for all good research. This instance is no different. In order to find the maximum level of performance for your BIOS and chipset, you will have to tweak the settings, reboot the computer, and see what happens. If it works, then brav ...
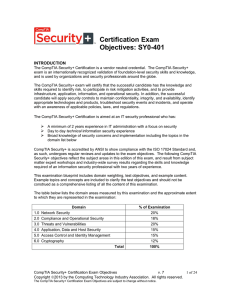
CompTIA Security (SY0-401)
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
The Real Cost of Free Programs such as Instant
... Instant Messenger (AIM). Incidentally, these two products are also the most widely used Instant Messaging products, along with Yahoo Instant Messenger and ICQ. ...
... Instant Messenger (AIM). Incidentally, these two products are also the most widely used Instant Messaging products, along with Yahoo Instant Messenger and ICQ. ...
Risk Analysis - University at Albany
... • Different stakeholders have various perception of risk • Several sources of threats exist simultaneously Sanjay Goel, School of Business/Center for Information Forensics and Assurance University at Albany Proprietary Information ...
... • Different stakeholders have various perception of risk • Several sources of threats exist simultaneously Sanjay Goel, School of Business/Center for Information Forensics and Assurance University at Albany Proprietary Information ...
6. Basic concept of the Cybersecurity Information Exchange
... the actual sources of attacks, i.e. bot-herders and the like, viewing only one type of information, no matter what the one type is, has proven ineffective in countering the threat. Information that is available is often of such disparate nature that trying to coordinate and correlate available infor ...
... the actual sources of attacks, i.e. bot-herders and the like, viewing only one type of information, no matter what the one type is, has proven ineffective in countering the threat. Information that is available is often of such disparate nature that trying to coordinate and correlate available infor ...
Certification Exam Objectives: SY0-401
... • Risks associated with Cloud Computing and Virtualization • Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
... • Risks associated with Cloud Computing and Virtualization • Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
McAfee Database Security Solution Brief
... McAfee Database Activity Monitoring Protect business-critical databases in real time across all threat vectors—without downtime. McAfee Database Activity Monitoring provides real-time visibility into all database activity, including local privileged user access and sophisticated attacks from within ...
... McAfee Database Activity Monitoring Protect business-critical databases in real time across all threat vectors—without downtime. McAfee Database Activity Monitoring provides real-time visibility into all database activity, including local privileged user access and sophisticated attacks from within ...
CISSP 第四版最新上课培训笔记(详细版)
... Single State Machine – All users have full access. (System High mode of Operation) ...
... Single State Machine – All users have full access. (System High mode of Operation) ...
A: - Tripod
... access server: Communications processor that connects asynchronous devices to a LAN or WAN through network and terminal emulation software. Performs both synchronous and asynchronous routing of supported protocols. Sometimes called a network access server. Compare with communication server. ACCESS T ...
... access server: Communications processor that connects asynchronous devices to a LAN or WAN through network and terminal emulation software. Performs both synchronous and asynchronous routing of supported protocols. Sometimes called a network access server. Compare with communication server. ACCESS T ...
Viruses - Binus Repository
... • viral attacks exploit lack of integrity control on systems • to defend need to add such controls • typically by one or more of: – prevention - block virus infection mechanism – detection - of viruses in infected system – reaction - restoring system to clean state ...
... • viral attacks exploit lack of integrity control on systems • to defend need to add such controls • typically by one or more of: – prevention - block virus infection mechanism – detection - of viruses in infected system – reaction - restoring system to clean state ...
the catalogue here
... Providing the optimal solution, with constant innovation. As the leader in content security, Trend Micro provides solutions enabling a safe information society. This is Trend Micro’s mission. In addition to the changing trends in threats, the emergence of cloud computing, and the penetration of mobi ...
... Providing the optimal solution, with constant innovation. As the leader in content security, Trend Micro provides solutions enabling a safe information society. This is Trend Micro’s mission. In addition to the changing trends in threats, the emergence of cloud computing, and the penetration of mobi ...
Slides - TERENA Networking Conference 2008
... • Secure and reliable access to any service from any device across any network (in accordance with policy) ...
... • Secure and reliable access to any service from any device across any network (in accordance with policy) ...
VPN
... remote-access VPN. AAA server - For each VPN connection, the AAA server confirms who you are, identifies what you're allowed to access over the connection and tracks what you do while you're logged in. Firewall - maintaining that the information on the private network is secure ...
... remote-access VPN. AAA server - For each VPN connection, the AAA server confirms who you are, identifies what you're allowed to access over the connection and tracks what you do while you're logged in. Firewall - maintaining that the information on the private network is secure ...
Reading for This Class - Computer Secrity Classes
... finding flaws – Called a “test”, when used by defenders – Called an “attack” when used by attackers ...
... finding flaws – Called a “test”, when used by defenders – Called an “attack” when used by attackers ...
Advanced Operating Systems, CSci555
... • Security is host to host, or host to network, or network to network as with VPN’s – Actually, VPN’s are rarely used host to host, but if the network had a single host, then it is equivalent. Copyright © 1995-2007 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE ...
... • Security is host to host, or host to network, or network to network as with VPN’s – Actually, VPN’s are rarely used host to host, but if the network had a single host, then it is equivalent. Copyright © 1995-2007 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE ...
8. Enabling cybersecurity information exchange
... The editors initially designated for the progress of the Recommendation were (in alphabetical order): Stephen Adegbite (Adobe, FIRST), Inette Furey (DHS), Youki Kadobayashi (NICT), Robert A. Martin (MITRE), Angela McKay (Microsoft), Damir Rajnovic (FIRST), Gavin Reid (Cisco), Tony Rutkowski (Yaana), ...
... The editors initially designated for the progress of the Recommendation were (in alphabetical order): Stephen Adegbite (Adobe, FIRST), Inette Furey (DHS), Youki Kadobayashi (NICT), Robert A. Martin (MITRE), Angela McKay (Microsoft), Damir Rajnovic (FIRST), Gavin Reid (Cisco), Tony Rutkowski (Yaana), ...
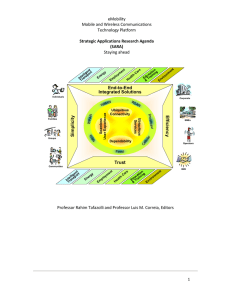
List if Contents
... Full project title: eMobility Coordination Action Short Project Title: eMobility CA Number and title of work‐packages: WP1,2,3 Strategic Applications and Research Agenda Document Title: SARA Editor: Prof. Rahim Tafazolli, Prof. Luis M Correia and various Work‐packages leaders: UniS, IST Lisbon ...
... Full project title: eMobility Coordination Action Short Project Title: eMobility CA Number and title of work‐packages: WP1,2,3 Strategic Applications and Research Agenda Document Title: SARA Editor: Prof. Rahim Tafazolli, Prof. Luis M Correia and various Work‐packages leaders: UniS, IST Lisbon ...
Security+Certification
... automated information system or a network. This type of hacker (also known as a cracker) is typically doing something mischievous or malicious, and although they might be trying to break into a system for what they consider a good and higher cause, they are still breaking into a system. Novice. A no ...
... automated information system or a network. This type of hacker (also known as a cracker) is typically doing something mischievous or malicious, and although they might be trying to break into a system for what they consider a good and higher cause, they are still breaking into a system. Novice. A no ...
Hands-On Ethical Hacking and Network Security
... Defines the WirelessMAN Air Interface Range of up to 30 miles Throughput of up to 120 Mbps ...
... Defines the WirelessMAN Air Interface Range of up to 30 miles Throughput of up to 120 Mbps ...
PDF - IBM Redbooks
... storage, and many others are all readily available. The ease and speed at which these new applications can be installed or simply accessed reduces the effectiveness of a perimeter-based security architecture and provides many new types of risks. These applications can be used by an attacker to obtai ...
... storage, and many others are all readily available. The ease and speed at which these new applications can be installed or simply accessed reduces the effectiveness of a perimeter-based security architecture and provides many new types of risks. These applications can be used by an attacker to obtai ...