Exam Questions - Advanced Technology Support, Inc.
... . Describe how Linux is hacked and how it is used as a hacking tool ...
... . Describe how Linux is hacked and how it is used as a hacking tool ...
PPT
... ~2,500 Faculty & Staff 12 buildings on a 13 acre campus Stand-alone institution (not part of a university or hospital) • Research only – no clinical care ...
... ~2,500 Faculty & Staff 12 buildings on a 13 acre campus Stand-alone institution (not part of a university or hospital) • Research only – no clinical care ...
IEEE Communications Society
... The current Internet, which was designed over 40 years ago, is facing unprecedented challenges in many aspects, especially in the commercial context. JIANLI PAN, SUBHARTHI PAUL, AND RAJ JAIN Designing for competition is an important consideration for the design of future Internet architectures. Netw ...
... The current Internet, which was designed over 40 years ago, is facing unprecedented challenges in many aspects, especially in the commercial context. JIANLI PAN, SUBHARTHI PAUL, AND RAJ JAIN Designing for competition is an important consideration for the design of future Internet architectures. Netw ...
EC Council CHFI Certification: Course CF220
... Introduction to Snort Analysis • Snort – Widely used, open-source, network-based intrusion detection system capable of performing real-time traffic analysis and packet logging on IP networks – Performs protocol analysis and content matching to detect a variety of attacks and probes such as: buffer ...
... Introduction to Snort Analysis • Snort – Widely used, open-source, network-based intrusion detection system capable of performing real-time traffic analysis and packet logging on IP networks – Performs protocol analysis and content matching to detect a variety of attacks and probes such as: buffer ...
Dr.Halil ADAHAN NEAR EAST UNIVERSITY Faculty of
... available to network users, and managing changes in those resources. The Windows Server amily provides many tools you can use to manage files and folders. These tools include Shared ...
... available to network users, and managing changes in those resources. The Windows Server amily provides many tools you can use to manage files and folders. These tools include Shared ...
Firewalls And Networks How To Hack Into
... to which network protocols, which hosts are the source of most of the traffic, and which hosts are the destination of most of the traffic. You can also examine data traveling between a particular pair of hosts and categorize it by protocol and store it for later analysis offline. With a sufficiently ...
... to which network protocols, which hosts are the source of most of the traffic, and which hosts are the destination of most of the traffic. You can also examine data traveling between a particular pair of hosts and categorize it by protocol and store it for later analysis offline. With a sufficiently ...
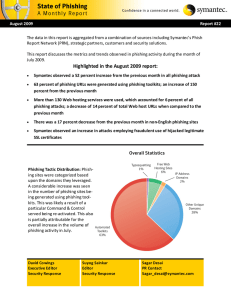
Highlighted in the August 2009 report
... certificates. Fraudsters have targeted the users of major brands by compromising Web servers with SSL certificates so that the fraudulent Web pages can display the familiar padlock icon, while offering a false sense of security to the victims. In this particular attack, the certificates were legitim ...
... certificates. Fraudsters have targeted the users of major brands by compromising Web servers with SSL certificates so that the fraudulent Web pages can display the familiar padlock icon, while offering a false sense of security to the victims. In this particular attack, the certificates were legitim ...
Junos Pulse Access Control Service
... credentials, and assesses the device’s security state. Junos Pulse leverages and integrates with the native 802.1X supplicant available within Microsoft Windows to deliver comprehensive L2 access control. Junos Pulse Access Control Service can also support native 802.1X supplicants on Apple Mac OS X ...
... credentials, and assesses the device’s security state. Junos Pulse leverages and integrates with the native 802.1X supplicant available within Microsoft Windows to deliver comprehensive L2 access control. Junos Pulse Access Control Service can also support native 802.1X supplicants on Apple Mac OS X ...
N10-003 Network+
... A: In the star topology, each node is connected to a central hub or switch. This requires less cabling than in the mesh topology, in which each node is connected to at least three other nodes. B: In the ring topology consists of a closed loop in which each node is connected to the node ahead of it a ...
... A: In the star topology, each node is connected to a central hub or switch. This requires less cabling than in the mesh topology, in which each node is connected to at least three other nodes. B: In the ring topology consists of a closed loop in which each node is connected to the node ahead of it a ...
AdderView CATxIP 5000
... Enterprise installations are effectively limitless, you can keep adding AdderView CATxIP 5000 units and new hosts whenever and wherever required. For all but the most basic enterprise configurations, the supplied ADDER.NET utility becomes vitally important: For users, it provides a virtualised and s ...
... Enterprise installations are effectively limitless, you can keep adding AdderView CATxIP 5000 units and new hosts whenever and wherever required. For all but the most basic enterprise configurations, the supplied ADDER.NET utility becomes vitally important: For users, it provides a virtualised and s ...
Administrator`s Guide
... (called briefly WinRoute in further text). After this setup the firewall should be immediately available and able to share your Internet connection and protect your local network. For a detailed guide refer to the separate WinRoute — Step-by-Step Configuration guide. If you are not sure how to set a ...
... (called briefly WinRoute in further text). After this setup the firewall should be immediately available and able to share your Internet connection and protect your local network. For a detailed guide refer to the separate WinRoute — Step-by-Step Configuration guide. If you are not sure how to set a ...
Exadata Health and Resource Usage Monitoring
... The Exachk and Enterprise Manager HealthCheck Plug-in output assists customers to more easily review and cross reference current collected data against supported version levels as well as recommended Oracle Exadata best practices. The Oracle Exadata Database Machine Exachk and HealthCheck tools are ...
... The Exachk and Enterprise Manager HealthCheck Plug-in output assists customers to more easily review and cross reference current collected data against supported version levels as well as recommended Oracle Exadata best practices. The Oracle Exadata Database Machine Exachk and HealthCheck tools are ...
VPN: Virtual Private Network
... • Lack of standards • Understanding of security issues • Unpredictable Internet traffic • Difficult to accommodate products from different vendors ...
... • Lack of standards • Understanding of security issues • Unpredictable Internet traffic • Difficult to accommodate products from different vendors ...
Wireless Sensor Networks: Technology Roadmap
... Oceanographic and Atmospheric Administration (NOAA) for monitoring events in the ocean, e.g., seismic and animal activity. During the same time, United States developed the network of air defense radars to defend its territory, which now is also used for drug interdiction. Research on sensor network ...
... Oceanographic and Atmospheric Administration (NOAA) for monitoring events in the ocean, e.g., seismic and animal activity. During the same time, United States developed the network of air defense radars to defend its territory, which now is also used for drug interdiction. Research on sensor network ...
Centralized Management and Processing Policy for Log Files
... The log management console uses two network cards to physically insulate the bottom network equipment layer from the top log server layer. One network card communicates with the bottom target equipment. The other communicates with the top log server, and performs the functions below. (1) Controlling ...
... The log management console uses two network cards to physically insulate the bottom network equipment layer from the top log server layer. One network card communicates with the bottom target equipment. The other communicates with the top log server, and performs the functions below. (1) Controlling ...
Kerio WinRoute Firewall 6
... to as “WinRoute” within this document). After this setup the firewall should be immediately available and able to share your Internet connection and protect your local network. For a detailed guide refer to the separate WinRoute — Step-by-Step Configuration guide. If you are not sure how to set any ...
... to as “WinRoute” within this document). After this setup the firewall should be immediately available and able to share your Internet connection and protect your local network. For a detailed guide refer to the separate WinRoute — Step-by-Step Configuration guide. If you are not sure how to set any ...
Windows Peer-to-Peer Network Configuration Guide
... client and a server. However, with a client/server based application such as Pathways, it is necessary that only one workstation act as the server, with the other workstations, or clients, accessing Pathways from that single “server”. The installation of Pathways can either be performed from one of ...
... client and a server. However, with a client/server based application such as Pathways, it is necessary that only one workstation act as the server, with the other workstations, or clients, accessing Pathways from that single “server”. The installation of Pathways can either be performed from one of ...
Web Teaching 2nd edition @ www.mkclibrary.yolasite.com
... includes potentially useful research on teaching and learning. It may surprise many readers to learn that support for multimedia or learning styles is much weaker than many think it is, but that support for cooperative learning seems very strong. Chapter 3, "Multimedia Overview ," begins some nuts a ...
... includes potentially useful research on teaching and learning. It may surprise many readers to learn that support for multimedia or learning styles is much weaker than many think it is, but that support for cooperative learning seems very strong. Chapter 3, "Multimedia Overview ," begins some nuts a ...
Web Teaching 2nd edition @ www.mkclibrary.yolasite
... Active learning approaches have larger positive effects on learning outcomes. 5. Many teachers have developed Web supplements for their courses. There is very strong evidence that the students who use these resources learn better than those who do not. 6. Very few teachers have enjoyed time efficien ...
... Active learning approaches have larger positive effects on learning outcomes. 5. Many teachers have developed Web supplements for their courses. There is very strong evidence that the students who use these resources learn better than those who do not. 6. Very few teachers have enjoyed time efficien ...
FE408xxxAx - USR - To Parent Directory
... Gathering Initial Information ......................................................................................................................................... 4 Connecting to Optinet ........................................................................................................... ...
... Gathering Initial Information ......................................................................................................................................... 4 Connecting to Optinet ........................................................................................................... ...
Kerio WinRoute Firewall 6
... to as “WinRoute” within this document). After this setup the firewall should be immediately available and able to share your Internet connection and protect your local network. For a detailed guide refer to the separate WinRoute — Step-by-Step Configuration guide. If you are not sure how to set any ...
... to as “WinRoute” within this document). After this setup the firewall should be immediately available and able to share your Internet connection and protect your local network. For a detailed guide refer to the separate WinRoute — Step-by-Step Configuration guide. If you are not sure how to set any ...
Slide 1
... • 802.11n – Faster and newer antenna technology – Most devices must use multiple antennas – Multiple in/multiple out (MIMO) – Up to 600 Mbps theoretically – Many WAPs use transmit beamforming – Dual-band WAPs run at 5 GHz and 2.4 GHz – Some WAPs support 802.11a devices © 2012 The McGraw-Hill Compani ...
... • 802.11n – Faster and newer antenna technology – Most devices must use multiple antennas – Multiple in/multiple out (MIMO) – Up to 600 Mbps theoretically – Many WAPs use transmit beamforming – Dual-band WAPs run at 5 GHz and 2.4 GHz – Some WAPs support 802.11a devices © 2012 The McGraw-Hill Compani ...
Exam Topics in This Chapter
... OpenDNS, and CloudLock, to expand its security portfolio. The Cisco ASA FirePOWER module provides NGIPS, Application Visibility and Control (AVC), URL filtering, and Advanced Malware Protection (AMP). This module runs as a separate application from the classic Cisco ASA software. The Cisco ASA FireP ...
... OpenDNS, and CloudLock, to expand its security portfolio. The Cisco ASA FirePOWER module provides NGIPS, Application Visibility and Control (AVC), URL filtering, and Advanced Malware Protection (AMP). This module runs as a separate application from the classic Cisco ASA software. The Cisco ASA FireP ...
Internet of Things (IoT) in 5 days
... welcome! Please engage visiting IoT in five days GitHub repository The book has been developed in asciidoc, and it can be compiled from its sources to produce HTML, PDF, eBook and others formats. The following are the authors who contributed to this book: Antonio Liñán defines himself as "an enginee ...
... welcome! Please engage visiting IoT in five days GitHub repository The book has been developed in asciidoc, and it can be compiled from its sources to produce HTML, PDF, eBook and others formats. The following are the authors who contributed to this book: Antonio Liñán defines himself as "an enginee ...
$doc.title
... markets. I propose that mutual augmentation exists between individual, institutional, and aggregate forms of surveillance on social media. These three models are situated within the same informational platform. By ...
... markets. I propose that mutual augmentation exists between individual, institutional, and aggregate forms of surveillance on social media. These three models are situated within the same informational platform. By ...