Lecture 11
... On some systems, the process is manual. On many systems, e.g. the Apple Macintosh,, this process is completely automatic. In Windows, this capability is known as plug-and-play. Many modern systems even make it possible to add and modify devices on the fly, without shutting down the system. USB and ...
... On some systems, the process is manual. On many systems, e.g. the Apple Macintosh,, this process is completely automatic. In Windows, this capability is known as plug-and-play. Many modern systems even make it possible to add and modify devices on the fly, without shutting down the system. USB and ...
Slide 1
... On some systems, the process is manual. On many systems, e.g. the Apple Macintosh,, this process is completely automatic. In Windows, this capability is known as plug-and-play. Many modern systems even make it possible to add and modify devices on the fly, without shutting down the system. USB and ...
... On some systems, the process is manual. On many systems, e.g. the Apple Macintosh,, this process is completely automatic. In Windows, this capability is known as plug-and-play. Many modern systems even make it possible to add and modify devices on the fly, without shutting down the system. USB and ...
PPT - Course Website Directory
... User app main program; calls kernel for services OS main program; calls user programs as subroutines ...
... User app main program; calls kernel for services OS main program; calls user programs as subroutines ...
The Java Virtual Shell and Kernel
... Nucleus is written in Java, unlike other operating systems like windows or Linux. This makes Nucleus portable, secure, thread-safe, robust and object oriented. In short all the features and advantages present in Java are present in Nucleus. Nucleus has a layered structure, the first and the upper mo ...
... Nucleus is written in Java, unlike other operating systems like windows or Linux. This makes Nucleus portable, secure, thread-safe, robust and object oriented. In short all the features and advantages present in Java are present in Nucleus. Nucleus has a layered structure, the first and the upper mo ...
A+ Guide to Managing and Maintaining your PC, 6e
... • Two main versions: Home Edition and Professional • Noteworthy new features: – Allows two users to logon and open applications – Incorporates Windows Messenger and Media Player ...
... • Two main versions: Home Edition and Professional • Noteworthy new features: – Allows two users to logon and open applications – Incorporates Windows Messenger and Media Player ...
2. Operating System Models
... Todays operating systems provide two fundamental services for users. First, they make the computer hardware easier to use. They create a virtual machine that differs markedly from the real machine. Indeed, the computer revolution of the last two decades is due, in part, to the success that operatin ...
... Todays operating systems provide two fundamental services for users. First, they make the computer hardware easier to use. They create a virtual machine that differs markedly from the real machine. Indeed, the computer revolution of the last two decades is due, in part, to the success that operatin ...
Modern Trends Used In Operating Systems For High Speed
... Process switching will be slow. Stability of the system reduces. Less hard drive space for user. G. Micro kernel [9], [6] Micro kernel is a small privileged source that provides process scheduling memory management and communication services and depends on other processes to perform some of th ...
... Process switching will be slow. Stability of the system reduces. Less hard drive space for user. G. Micro kernel [9], [6] Micro kernel is a small privileged source that provides process scheduling memory management and communication services and depends on other processes to perform some of th ...
Understanding Computers, 10/e, Chapter 6
... Encryption programs are used to secure e-mail messages and files that are sent over the Internet or other networks; can also be used with individual files stored on a hard drive. ...
... Encryption programs are used to secure e-mail messages and files that are sent over the Internet or other networks; can also be used with individual files stored on a hard drive. ...
• Chapter 1: Introduction
... • Distribute the computation among several physical processors. • Loosely coupled system – involves connecting 2 or more independent computer systems via communication link. So, each processor has its own O.S. and local memory; processors communicate with one another through various communications l ...
... • Distribute the computation among several physical processors. • Loosely coupled system – involves connecting 2 or more independent computer systems via communication link. So, each processor has its own O.S. and local memory; processors communicate with one another through various communications l ...
Operating Systems
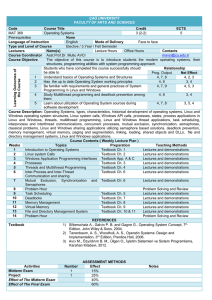
... Course Description: Operating Systems, types, characteristics, historical development of operating systems, Linux and Windows operating system structures, Linux system calls, Windows API calls, processes, states, process applications in Linux and Windows, threads, multithread programming, Linux and ...
... Course Description: Operating Systems, types, characteristics, historical development of operating systems, Linux and Windows operating system structures, Linux system calls, Windows API calls, processes, states, process applications in Linux and Windows, threads, multithread programming, Linux and ...
15.a The Internal Operating System
... programs to be executed Deciding which process shall be executed next by the processor Swapping processes Deciding which process’s pending I/O request shall be handled by an available I/O device ...
... programs to be executed Deciding which process shall be executed next by the processor Swapping processes Deciding which process’s pending I/O request shall be handled by an available I/O device ...
OS2-by-Kevin-Koo-Kyu-Oh-Matt-Liberati-Stephanie-Engel-2002
... OS/2 Warp 4 • Released in August, 1996 • Its new features included a "beautified" GUI; an ex-Apple programmer designed the new graphical icons • A full Java Development Kit, which included a Java Virtual Machine • OS/2 Warp 4 is fully Object Oriented via SOM • Pre-emptively multitasks all sessions ...
... OS/2 Warp 4 • Released in August, 1996 • Its new features included a "beautified" GUI; an ex-Apple programmer designed the new graphical icons • A full Java Development Kit, which included a Java Virtual Machine • OS/2 Warp 4 is fully Object Oriented via SOM • Pre-emptively multitasks all sessions ...
Chapter 5
... More on Operating Systems • OS often called software environment or platform • Operating systems commonly used by individuals ...
... More on Operating Systems • OS often called software environment or platform • Operating systems commonly used by individuals ...
operating system (2a) - BackBenchersCafe.com
... 4. What do understand by free space management? Explain the different methods to implement it. 5. Explain the different features of Linux Operating System. 6. What do you mean by computer security and how could it be maintained? 7. Differentiate be between any two of the following : (a) Buffering an ...
... 4. What do understand by free space management? Explain the different methods to implement it. 5. Explain the different features of Linux Operating System. 6. What do you mean by computer security and how could it be maintained? 7. Differentiate be between any two of the following : (a) Buffering an ...
Core System Services
... • So instead of constantly maintaining potentially dozens of services loaded in memory waiting to be used, they are all listed in inetd’s configuration file, /etc/inetd.conf. On their behalf, inetd listens for incoming connections. Thus, only a single process needs to be in memory. ...
... • So instead of constantly maintaining potentially dozens of services loaded in memory waiting to be used, they are all listed in inetd’s configuration file, /etc/inetd.conf. On their behalf, inetd listens for incoming connections. Thus, only a single process needs to be in memory. ...
Using the SEL System Control Library for Computer
... disruptive and dangerous for computers running autonomously that must detect and recover from these problems independently. Software failures are the reason SEL designed a hardware watchdog into each of its computers. The watchdog provides a mechanism, independent of software, to restore normal oper ...
... disruptive and dangerous for computers running autonomously that must detect and recover from these problems independently. Software failures are the reason SEL designed a hardware watchdog into each of its computers. The watchdog provides a mechanism, independent of software, to restore normal oper ...
Lecture #3: Operating
... Booting – starting a computer by loading the kernel Bootstrap program – code stored in ROM that is able to locate the kernel, ...
... Booting – starting a computer by loading the kernel Bootstrap program – code stored in ROM that is able to locate the kernel, ...
Installing guest operating systems on VMWare and Linux Kernel
... Installing guest operating systems on Linux Kernel-based Virtual Machine (KVM) virtual servers To install a quest operating system on a KVM virtual server, follow the steps in the Installing guest operating systems on Linux Kernel-based Virtual Machine (KVM) virtual servers quick start guide, which ...
... Installing guest operating systems on Linux Kernel-based Virtual Machine (KVM) virtual servers To install a quest operating system on a KVM virtual server, follow the steps in the Installing guest operating systems on Linux Kernel-based Virtual Machine (KVM) virtual servers quick start guide, which ...
Nechiele Whittington - Optimal Resume at KAPLAN UNIVERSITY
... OS EVOLUTION - 3 got the idea to take the users out of the equation and let the computer set up their workloads on their own. IBM introduced a more streamlined system under the IBM 704 system. This system used operators that processed punch card information into satellite computer feeds that were t ...
... OS EVOLUTION - 3 got the idea to take the users out of the equation and let the computer set up their workloads on their own. IBM introduced a more streamlined system under the IBM 704 system. This system used operators that processed punch card information into satellite computer feeds that were t ...
Abstract View of System Components
... (ex: CPU time, memory space, I/O devices…) Control program – controls the execution of user programs and operations of I/O devices . Kernel – the one program running at all times (all else being application programs). Since hardware alone is not particularly easy to use, application programs a ...
... (ex: CPU time, memory space, I/O devices…) Control program – controls the execution of user programs and operations of I/O devices . Kernel – the one program running at all times (all else being application programs). Since hardware alone is not particularly easy to use, application programs a ...
choices
... – PURE is for deeply embedded systems – PURE extension has an OSEK API – PURE uses the concept of components at the design level, and avoids artificical boundaries in implementation concerning run time and code size – PURE is fine-grained ...
... – PURE is for deeply embedded systems – PURE extension has an OSEK API – PURE uses the concept of components at the design level, and avoids artificical boundaries in implementation concerning run time and code size – PURE is fine-grained ...
slides - Embedded System and Wireless Networking Lab National
... the number of general-purpose processors used. Single-processor systems: There is one main CPU capable of executing a ...
... the number of general-purpose processors used. Single-processor systems: There is one main CPU capable of executing a ...
Operating System organization
... • Created at system start-up, assigned fixed sockets • Effectively a critical section – one request or activity is handled at a time • Maintains internal data structures for queuing up requests that cannot be replied to immediately • No sharing of data with requesting processes • Status information ...
... • Created at system start-up, assigned fixed sockets • Effectively a critical section – one request or activity is handled at a time • Maintains internal data structures for queuing up requests that cannot be replied to immediately • No sharing of data with requesting processes • Status information ...