* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download ppt in chapter 12
Survey
Document related concepts
Transcript
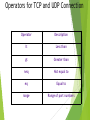
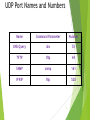
Chapter 12 Using Access List powered by DJ 1 Chapter Objectives At the end of this Chapter you will be able to: Introduce ACL concepts Explain the types of ACL Configure ACL Introduce wildcard masks Verify ACL powered by DJ 2 Access Control List - I Access Control List (ACL) is a set of commands, which are grouped together to filter the traffic that enters or leaves an interface The functions of ACLs include the following: Reduce the network traffic and increase the network performance Control the flow of traffic in the network Provide security for network access Make decision about the type of network to be forwarded or restricted on an interface powered by DJ 3 Access Control List - II You must also specify one of the following directions in which the traffic should be filtered: Inbound Outbound The Access lists are available in the following two types: Numbered ACL Named ACL Each of the below ACLs supports two types: Standard ACL Extended ACL powered by DJ 4 ACL Processing ACL are statements, which are grouped together by using a name or number When ACL process a packet on the router from the group of statements, the router performs a number of steps to find a match for the ACL statements The router processes each ACL in the top-down approach If the router is not able to find a match of packet to the first ACL statement then the router continues with the next statement, following the same process powered by DJ 5 Configuring ACL You must know the guidelines to configure the ACL You can use the access-list command to create an ACL The syntax to create an ACL is: access-list ACL_# permit|deny conditions To activate ACL on the interface, enter the following at the command prompt: interface type slot_#|port_# ip access-group ACL_# in|out powered by DJ 6 ACL Numbers and Protocol Types - I Type Numbers IP Standard 1-99, 1300-1999 Standard Vines 1-99 IP Extended 100-199, 2000-2699 Extended Vines 100-199 Bridging type code (layer-2) 200-299 DECnet 300-399 Standard XNS 400-499 Extended XNS 500-599 Apple Talk 600-699 7 ACL Numbers and Protocol Types - II Bridging MAC address and vendor code 700-799 IPX Standard 800-899 IPX Extended 900-999 IPX SAP filters 1000-1099 Extended transparent bridging 1100-1199 IPX NLSP 1200-1299 8 Wildcard Masking Wildcard masks can be used for matching a range of IP addresses in ACL, instead of manually entering it A wildcard mask of 0 or 1 in the bit position implies the following: 0 - Specifies that the bit position of the ACL statement address must match the bit position in the IP address of the packet that is to be examined 1 - Specifies that the bit position of the ACL statement address does not have to match the bit position in the IP address of the packet that is to be examined powered by DJ 9 Subnet Masks and Wildcard Masks Values Bit Value Subnet Mask Wildcard Mask 0 Host component Must match 1 Network component Ignore 10 Standard Numbered ACL • Standard IP access lists filter network traffic by examining the source IP address in a packet. • It always applies near to Destination. • Range of standard IP access list is 1–99. • After choose the access-list number, you need to decide whether you’re creating a Permit or deny statement. You can use any parameter to permit or deny any host or network you can use an IP address to specify either a single host or a range of them, or you can use the host command to specify a specific host only. 11 Standard Numbered ACL You can create an entry in a standard numbered IP ACL using the access-list command.The syntax of this command is: access-list 1-99|1300-1999 permit|deny source_address [wildcard_mask] [log] After creating the standard ACL, you must activate it on the router's interface The ip access-group command below enables you to activate the ACL on the interface: ip access-group ACL_number in|out powered by DJ 12 Extended Numbered ACLs •Extended access lists allow you to specify source and destination address as well as the protocol and port number. •It always applies near to Source. •Range of Extended IP access list is 100–199. •After choose the access-list number, you need to decide whether you’re creating a Permit or deny statement. •You can effectively allow users access to a physical LAN and stop them from accessing specific hosts—or even specific services on those hosts. powered by DJ 13 Extended Numbered ACLs The extended numbered ACLs are more flexible as compared to the standard ACLs The syntax of the command to configure an extended numbered ACL is: access-list 100-199|2000-2699 permit|deny IP_protocol source_address source_wildcard mask [protocol_information] destination_address destination_wildcard_mask [protocol_information] [log] powered by DJ 14 TCP and UDP The extended ACL can filter the traffic on IP protocols such as TCP and UDP The syntax of the command that allows you to configure an extended ACL for TCP or UDP is: access-list 100-199|2000-2699 permit|deny tcp|udp source_address source_wildcard_mask [operator source_port_#] destination address destination_wildcard_mask [operator destination_port_#][established][log] powered by DJ 15 Operators for TCP and UDP Connection Operator Description lt Less than gt Greater than neq Not equal to eq Equal to range Range of port numbers 16 TCP Port Names and Numbers Name Command Parameter Number FTP Data ftp-data 20 FTP Control ftp 21 Telnet telnet 23 SMTP smtp 25 WWW www 80 17 UDP Port Names and Numbers Name Command Parameter Number DNS Query dns 53 TFTP tftp 69 SNMP snmp 161 IP RIP Rip 520 18 Controlling Telnet Access to a Router The standard IP ACLs controls the telnet access to the router. The access-class command enables you to accomplish this. The syntax of this command is: access-class standard_ACL_# in|out Cisco routers enable you to restrict telnet access for the normal users You can configure your router to allow telnet access only for the networks administrators powered by DJ 19 Named ACL’s Named ACLs support both IP and IPX protocols The ip access-list allows you to create a named ACL The syntax for this command is: ip access-list standard/extended ACL_name After creating a named ACL, you have to activate it on the router interface The ip access-group command given below enables you to activate the named ACL: ip access-group ACL_name in|out powered by DJ 20 Verifying and Monitoring Access Control List To view the ACLs that are activated on the router’s interfaces, use the following command: show ip interfaces Cisco allows you to monitor each statement in the ACL. To view the statements in the ACL, use the following commands: show access-lists [ACL_#_or_name] show ip access-list [ACL_#_or_name] powered by DJ 21 Editing Entries You may need to add, delete or modify an entry in the ACL In a numbered ACL, you cannot delete a specific entry The no access-list command allows you to delete an ACL, The syntax of the command is: no access-list number The no access-list ACL_# command deletes the entire list powered by DJ 22 Summary - I The access control list is a set of commands, which are grouped together, to filter the traffic that enters or leaves an interface ACL are the statements, which are grouped together by using a name or number. When ACL process a packet on the router from the group of statements, the router performs a number of steps to find a match for the ACL statements After building IP ACL, you have to apply it to a process in the IOS The extended numbered ACL’s are more flexible as compared to the standard ACLs powered by DJ 23 Summary - II If the router locates a match between the packet and statement then the router executes one of the two actions that are included with the statement. The actions are: Permit Deny A need may arise to add, delete or modify an entry in the ACL. You cannot delete a specific entry in an ACL To handle the IP addresses in ACL statements, wildcard masks can be used for matching a range of address instead of manually entering it powered by DJ 24 Summary - III A wildcard is similar to an inverted subnet mask. If you want to match on any address in a subnet or network then you have to take the subnet mask and invert the bit values You must consider the following while placing the ACLs: Standard ACL - Needs to be placed close to the destination device that you want to prevent the source from reaching. Extended ACL - Needs to be placed close to the source device. The extended ACL can filter on both the source as well as destination address powered by DJ 25 THANK YOU powered by DJ 26