* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Chap 12
Security-focused operating system wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wireless security wikipedia , lookup
Unix security wikipedia , lookup
Computer security wikipedia , lookup
Mobile security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Cyberattack wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
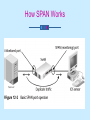
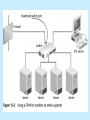
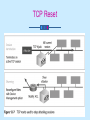
Intrusion Detection Chapter 12 Learning Objectives Explain what intrusion detection systems are and identify some major characteristics of intrusion detection products Detail the differences between host-based and network-based intrusion detection Identify active detection and passive detection features of both host- and network-based IDS products continued… Learning Objectives Explain what honeypots are and how they are employed to increase network security Clarify the role of security incident response teams in the organization Intrusion Detection System (IDS) Detects malicious activity in computer systems Identifies and stops attacks in progress Conducts forensic analysis once attack is over The Value of IDS Monitors network resources to detect intrusions and attacks that were not stopped by preventative techniques (firewalls, packet-filtering routers, proxy servers) Expands available options to manage risk from threats and vulnerabilities Negatives and Positives IDS must correctly identify intrusions and attacks False negatives True positives True negatives IDS missed an attack False positives Benign activity reported as malicious Dealing with False Negatives and False Positives False negatives Obtain more coverage by using a combination of network-based and host-based IDS Deploy NIDS at multiple strategic locations in the network False positives Reduce number using the tuning process Types of IDS Network-based (NIDS) Host-based (HIDS) Network-based IDS Uses a dedicated platform for purpose of monitoring network activity Analyzes all passing traffic Sensors have two network connections One operates in promiscuous mode to sniff passing traffic An administrative NIC sends data such as alerts to a centralized management system Most commonly employed form of IDS NIDS Architecture Place IDS sensors strategically to defend most valuable assets Typical locations of IDS sensors Just inside the firewall On the DMZ On network segments connecting mainframe or midrange hosts Switch Port Analyzer (SPAN) Allows traffic sent or received in one interface to be copied to another monitoring interface Typically used for sniffers or NIDS sensors How SPAN Works Limitations of SPAN Traffic between hosts on the same segment is not monitored; only traffic leaving the segment crosses the monitored link Switch may offer limited number of SPAN ports or none at all Hub Device for creating LANs that forward every packet received to every host on the LAN Allows only a single port to be monitored Using a Hub in a Switched Infrastructure Tap Fault-tolerant hub-like device used inline to provide IDS monitoring in switched network infrastructures NIDS Signature Types Signature-based IDS Port signature Header signatures Network IDS Reactions TCP resets IP session logging Shunning or blocking Host-based IDS Primarily used to protect only critical servers Software agent resides on the protected system Detects intrusions by analyzing logs of operating systems and applications, resource utilization, and other system activity Use of resources can have impact on system performance HIDS Method of Operation Auditing logs (system logs, event logs, security logs, syslog) Monitoring file checksums to identify changes Elementary network-based signature techniques including port activity Intercepting and evaluating requests by applications for system resources before they are processed Monitoring of system processes for suspicious activity HIDS Software Host wrappers Inexpensive and deployable on all machines Do not provide in-depth, active monitoring measures of agent-based HIDS products Agent-based software More suited for single purpose servers HIDS Active Monitoring Capabilities Log the event Alert the administrator Terminate the user login Disable the user account Advantages of Host-based IDS Verifies success or failure of attack by reviewing HIDS log entries Monitors use and system activities; useful in forensic analysis of the attack Protects against attacks that are not network based Reacts very quickly to intrusions continued… Advantages of Host-based IDS Not reliant on particular network infrastructure; not limited by switched infrastructures Installed on protected server itself; requires no additional hardware to deploy and no changes to network infrastructure Passive Detection Systems Can take passive action (logging and alerting) when an attack is identified Cannot take active actions to stop an attack in progress Active Detection Systems Have logging, alerting, and recording features of passive IDS, with additional ability to take action against offending traffic Options IDS shunning or blocking TCP reset Used in networks where IDS administrator has carefully tuned the sensor’s behavior to minimize number of false positive alarms TCP Reset Signature-based and Anomaly-based IDS Signature detections Also know as misuse detection IDS analyzes information it gathers and compares it to a database of known attacks, which are identified by their individual signatures Anomaly detection Baseline is defined to describe normal state of network or host Any activity outside baseline is considered to be an attack Intrusion Detection Products Aladdin Knowledge Systems Entercept Security Technologies Cisco Systems, Inc. Computer Associates International Inc. CyberSafe Corp. Cylant Technology Enterasys Networks Inc. Internet Security Systems Inc. Intrusion.com Inc. family of IDS products Honeypots False systems that lure intruders and gather information on methods and techniques they use to penetrate networks—by purposely becoming victims of their attacks Simulate unsecured network services Make forensic process easy for investigators Commercial Honeypots ManTrap Specter Smoke Detector NetFacade Open Source Honeypots BackOfficer Friendly BigEye Deception Toolkit LaBrea Tarpit Honeyd Honeynets User Mode Linux Honeypot Deployment Goal Gather information on hacker techniques, methodology, and tools Options Conduct research into hacker methods Detect attacker inside organization’s network perimeter Honeypot Design Must attract, and avoid tipping off, the attacker Must not become a staging ground for attacking other hosts inside or outside the firewall Honeypots, Ethics, and the Law Nothing wrong with deceiving an attacker into thinking that he/she is penetrating an actual host Honeypot does not convince one to attack it; it merely appears to be a vulnerable target Doubtful that honeypots could be used as evidence in court Incident Response Every IDS deployment should include two documents to answer “what now” questions IDS monitoring policy and procedure Requires well-documented monitoring procedures that detail actions for specific alerts Incident response plan Responsible for assigning personnel to assemble resources required to handle security incidents Typical SIRT Objectives Determine how incident happened Establish process for avoiding further exploitations of the same vulnerability Avoid escalation and further incidents Assess impact and damage of the incident Recover from the incident continued… Chapter Summary Two major types of intrusion detection Network-based IDS (monitor network traffic) Host-based IDS (monitor activity on individual computers) Honeypots Incident response