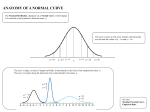
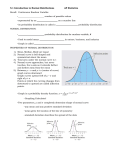
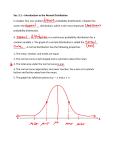
* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Why Cryptography?
Survey
Document related concepts
Transcript
Number Theory and
Advanced Cryptography
4. Elliptic Curves
Part I: Introduction to Number Theory
Part II: Advanced Cryptography
Chih-Hung Wang
Sept. 2012
1
Elliptic Curve Cryptography
Majority of public-key crypto (RSA, D-H) use either
integer or polynomial arithmetic with very large
numbers/polynomials
Imposes a significant load in storing and processing
keys and messages
An alternative is to use elliptic curves
In the mid-1980s, Miller and Koblitz introduced
elliptic curves into cryptography.
Offers same security with smaller bit sizes
4096-bit key size can be replaced by 313-bit elliptic curve
system
2
Real Elliptic Curves
An elliptic curve is defined by an
equation in two variables x & y, with
coefficients
Consider a cubic elliptic curve of form
y2
= x3 + ax + b
where x,y,a,b are all real numbers
also define zero point O
Have addition operation for elliptic curve
geometrically sum of Q+R is reflection of
intersection R
3
Real Elliptic Curve Example 1
4
Real Elliptic Curve Example 2
5
Geometric Description of Addition
6
Algebraic Description of Addition
P+Q = R
=(yQ-yP)/(xQ-xP)
P+P = 2P = R
7
Addition Law
8
Example of Addition (1)
9
Example of Addition (2)
10
Example of Addition (3)
11
Elliptic Curves Mod p
12
Example 1
13
Example 2-1
14
Example 2-2
15
Example 3
16
Example 4
17
Law 1
18
Law 2
19
Number of points Mod p
20
Hasse’s Theorem
Schoof Algorithm:
http://www.math.rochester.edu/people/grads/jdreibel/ref/12-7-05-Schoof.pdf
21
Discrete Logarithms on EC
22
Representing plaintext (1)
23
Representing plaintext (2)
24
Elliptic Curve Cryptography
ECC addition is analog of modulo multiply
ECC repeated addition is analog of modulo
exponentiation
need “hard” problem equiv to discrete log
Q=kP, where Q,P belong to a prime curve
is “easy” to compute Q given k,P
but “hard” to find k given Q,P
known as the elliptic curve logarithm problem
Certicom example: E23(9,17)
25
ECC Diffie-Hellman (1)
can do key exchange analogous to D-H
users select a suitable curve Ep(a,b)
select base point G=(x1,y1) with large order
n s.t. nG=O
A & B select private keys nA<n, nB<n
compute public keys: PA=nA×G, PB=nB×G
compute shared key: K=nA×PB, K=nB×PA
same since K=nA×nB×G
26
ECC Diffie-Hellman (2)
27
ECC Diffie-Hellman (3)
28
ECC Diffie-Hellman (4)
Page 365
29
ECC Encryption/Decryption (1)
several alternatives, will consider simplest
must first encode any message M as a point on
the elliptic curve Pm
select suitable curve & point G as in D-H
each user chooses private key nA<n
and computes public key PA=nA×G
to encrypt Pm : Cm={kG, Pm+k Pb}, k
random
decrypt Cm compute:
Pm+kPb–nB(kG) = Pm+k(nBG)–nB(kG) = Pm
30
ECC Encryption/Decryption (2)
Page 363-364
31
ECC Encryption/Decryption (3)
32
ECC Security (1)
Relies on elliptic curve logarithm problem
Fastest method is “Pollard rho method”
Compared to factoring, can use much
smaller key sizes than with RSA etc
For equivalent key lengths computations
are roughly equivalent
Hence for similar security ECC offers
significant computational advantages
33
ECC Security (2)
34
ECC Digital Signature (page 365366)
Signing
35
ECC Digital Signature (page 365366)II
Verification
36
ECC Digital Signature (1)
37
ECC Digital Signature (2)
38
ECC Digital Signature (3)
39