Chapter 1
... an overarching multitenant container database. A multitenant container database (CDB) is defined as a database capable of housing one or more pluggable databases. A container is defined as a collection of data files and metadata that exist within a CDB. A pluggable database is a special type of cont ...
... an overarching multitenant container database. A multitenant container database (CDB) is defined as a database capable of housing one or more pluggable databases. A container is defined as a collection of data files and metadata that exist within a CDB. A pluggable database is a special type of cont ...
Multi-Layered DB Application
... The system may be conceived of as layers of transparent glass upon which information is printed. The center layer of glass contains basic information which has the potential to be viewed by all user groups. Subsequent layers of glass are added with each new layer having ever greater specificity to ...
... The system may be conceived of as layers of transparent glass upon which information is printed. The center layer of glass contains basic information which has the potential to be viewed by all user groups. Subsequent layers of glass are added with each new layer having ever greater specificity to ...
powerpoint - Cheshire II Project Home Page
... request is a ranking of the documents in the collections in the order of decreasing probability of usefulness to the user who submitted the request, where the probabilities are estimated as accurately as possible on the basis of whatever data has been made available to the system for this purpose, t ...
... request is a ranking of the documents in the collections in the order of decreasing probability of usefulness to the user who submitted the request, where the probabilities are estimated as accurately as possible on the basis of whatever data has been made available to the system for this purpose, t ...
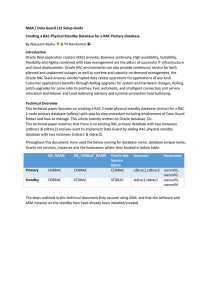
MAA / Data Guard 12c Setup Guide Creating a RAC Physical
... Note: Recommended to use SPFILE, if PFILE is in use the update/append the above parameters as required. 2. Configure the RAC primary database initialization parameters to support standby role. SQL> alter system set FAL_SERVER='stdrac1,stdrac2' scope=both sid='*' DB_FILE_NAME_CONVERT/LOG_FILE_NAME_CO ...
... Note: Recommended to use SPFILE, if PFILE is in use the update/append the above parameters as required. 2. Configure the RAC primary database initialization parameters to support standby role. SQL> alter system set FAL_SERVER='stdrac1,stdrac2' scope=both sid='*' DB_FILE_NAME_CONVERT/LOG_FILE_NAME_CO ...
T - VUB STARLab
... share no physical component Database systems that run on each site are independent of each other Transactions may access data at one or more sites ...
... share no physical component Database systems that run on each site are independent of each other Transactions may access data at one or more sites ...
Data Definition guide
... If this software/documentation is delivered to a U.S. Government Agency not within the Department of Defense, then it is delivered with Restricted Rights, as defined in FAR 552.227-14, Rights in Data-General, including Alternate III (June 1987). Information in this document is subject to change with ...
... If this software/documentation is delivered to a U.S. Government Agency not within the Department of Defense, then it is delivered with Restricted Rights, as defined in FAR 552.227-14, Rights in Data-General, including Alternate III (June 1987). Information in this document is subject to change with ...
QA Wizard Pro External Datasheets How To
... 6. Select First row contains column headers if the text file contains column headings. If this option is selected, QA Wizard Pro uses the values in the first row of the file to identify columns. If it is not selected, column names are created when the datasheet is added. 7. Select the text file form ...
... 6. Select First row contains column headers if the text file contains column headings. If this option is selected, QA Wizard Pro uses the values in the first row of the file to identify columns. If it is not selected, column names are created when the datasheet is added. 7. Select the text file form ...
CS 245: Database System Principles
... • To execute “select A,B from R,S where condition”: (1) Read dictionary to get R,S attributes (2) Read R file, for each line: (a) Read S file, for each line: (i) Create join tuple (ii) Check condition (iii) Display if OK ...
... • To execute “select A,B from R,S where condition”: (1) Read dictionary to get R,S attributes (2) Read R file, for each line: (a) Read S file, for each line: (i) Create join tuple (ii) Check condition (iii) Display if OK ...
The SQL Query Language COS 597A: Principles of Database and Information Systems
... already seen IN, EXISTS and UNIQUE. Can also use NOT IN, NOT EXISTS and NOT UNIQUE. Also available: op ANY, op ALL, op from >, <, =, ≥, ≤, ≠ Find names of branches with assets at least as large as the assets of some NYC branch: ...
... already seen IN, EXISTS and UNIQUE. Can also use NOT IN, NOT EXISTS and NOT UNIQUE. Also available: op ANY, op ALL, op from >, <, =, ≥, ≤, ≠ Find names of branches with assets at least as large as the assets of some NYC branch: ...
select
... where clauses that specify that a value be less than or equal to some value and greater than or equal to some other value. Find the loan number of those loans with loan amounts between ...
... where clauses that specify that a value be less than or equal to some value and greater than or equal to some other value. Find the loan number of those loans with loan amounts between ...
Database Denial of Service
... common DoS approaches we found were based on “flooding the pipes” rather than “exhausting the servers”. Flooding is accomplished by sending so many network packets that they simply overwhelm the network equipment. This type of ‘volumetric’ attack is the classic denial of service, most commonly perfo ...
... common DoS approaches we found were based on “flooding the pipes” rather than “exhausting the servers”. Flooding is accomplished by sending so many network packets that they simply overwhelm the network equipment. This type of ‘volumetric’ attack is the classic denial of service, most commonly perfo ...
Data Definition Guide - Embarcadero Technologies Product
... About the encryption commands . . . . . . 13-9 Setting a decrypt default value for a column 13-10 ...
... About the encryption commands . . . . . . 13-9 Setting a decrypt default value for a column 13-10 ...
SUGI 26: Database Access Using the SAS(r) System
... the Windows Control Panel and click on “ODBC Data Sources (32 bit)” to set up an ODBC data source name, e.g. “Oracle”. Figure 2 illustrates how this is done in Windows 98; Windows 2000 is virtually identical ...
... the Windows Control Panel and click on “ODBC Data Sources (32 bit)” to set up an ODBC data source name, e.g. “Oracle”. Figure 2 illustrates how this is done in Windows 98; Windows 2000 is virtually identical ...
Partial Database Availability
... that employ multiple filegroups to be online serving queries, while some of the database data may unavailable, in one or more filegroup(s) marked as offline. Online PIECEMEAL RESTORE2 in SQL Server 2005 Enterprise Edition, allows administrators of databases that employ multiple filegroups to restore ...
... that employ multiple filegroups to be online serving queries, while some of the database data may unavailable, in one or more filegroup(s) marked as offline. Online PIECEMEAL RESTORE2 in SQL Server 2005 Enterprise Edition, allows administrators of databases that employ multiple filegroups to restore ...
Document
... Use the flash recovery area for recovery-related files: • Simplifies location of database backups • Automatically manages the disk space allocated for recovery files • Does not require changes to existing scripts • Puts database backups, archive logs, and control file backups in the flash recovery a ...
... Use the flash recovery area for recovery-related files: • Simplifies location of database backups • Automatically manages the disk space allocated for recovery files • Does not require changes to existing scripts • Puts database backups, archive logs, and control file backups in the flash recovery a ...
An Adaptive Replication Environment for a Relational Database
... DBMS scope for the last years. In this context, each database is autonomous, allowing tuning for the best fit configuration to a specific scenario, as well as increasing the performance of each individual DBMS replica according to their needs. Furthermore, the modularity is another important aspect ...
... DBMS scope for the last years. In this context, each database is autonomous, allowing tuning for the best fit configuration to a specific scenario, as well as increasing the performance of each individual DBMS replica according to their needs. Furthermore, the modularity is another important aspect ...
Unit Testing Tips and Tricks: Database Interaction
... structure set up. Refactor mercilessly. • Especially if you need canned data that is ancillary to the test, it is often worth while to factor creation out into a static method in a utility class (object mother) so you can use it as necessary thereafter. ...
... structure set up. Refactor mercilessly. • Especially if you need canned data that is ancillary to the test, it is often worth while to factor creation out into a static method in a utility class (object mother) so you can use it as necessary thereafter. ...
Chapter 4: SQL
... The fetch statement causes the values of one tuple in the query result to be placed on host language variables. EXEC SQL fetch c into :si, :sn END_EXEC Repeated calls to fetch get successive tuples in the query result A variable called SQLSTATE in the SQL communication area (SQLCA) gets set to ‘0200 ...
... The fetch statement causes the values of one tuple in the query result to be placed on host language variables. EXEC SQL fetch c into :si, :sn END_EXEC Repeated calls to fetch get successive tuples in the query result A variable called SQLSTATE in the SQL communication area (SQLCA) gets set to ‘0200 ...
Microsoft Dynamics NAV 5
... Before you can restore a Dynamics NAV backup you must create an empty database into which you can restore the backup. This is because you cannot restore data over existing data. Creating a new database is described in Installation & System Management manual for the server option that you are using. ...
... Before you can restore a Dynamics NAV backup you must create an empty database into which you can restore the backup. This is because you cannot restore data over existing data. Creating a new database is described in Installation & System Management manual for the server option that you are using. ...
Not All Database Security Solutions Are Created Equal
... Your database and the networks that provide access to them must remain available and responsive. In addition, you need a database security solution that can provide real-time, actionable insights, not just after-the-fact forensics. The McAfee Database Security solution provides a clear competitive a ...
... Your database and the networks that provide access to them must remain available and responsive. In addition, you need a database security solution that can provide real-time, actionable insights, not just after-the-fact forensics. The McAfee Database Security solution provides a clear competitive a ...
WCFSQLTablePollingBlogdocx
... It is very common to have a requirement in middleware design where we have to query some SQL tables and retrieve some data when the conditions are met. The WCF-based adapters available with the BizTalk Adapter Pack enable the adapter clients to receive data-change messages from the SQL Server databa ...
... It is very common to have a requirement in middleware design where we have to query some SQL tables and retrieve some data when the conditions are met. The WCF-based adapters available with the BizTalk Adapter Pack enable the adapter clients to receive data-change messages from the SQL Server databa ...