Data Definition: Creating a Relation
... Restricting access to parts pf a table can be effected by using the view and grant commands Privileges can be withdrawn with the revoke command ...
... Restricting access to parts pf a table can be effected by using the view and grant commands Privileges can be withdrawn with the revoke command ...
Languages of DBMS Data Definition, Relational
... insert into weak_students (studno,name,courseno,exammark) where (select s.studno,name,courseno,exammark from enrol, student s where exammark <= 40 and enrol.studno = s.studno ); ...
... insert into weak_students (studno,name,courseno,exammark) where (select s.studno,name,courseno,exammark from enrol, student s where exammark <= 40 and enrol.studno = s.studno ); ...
Data Definition: Creating a Relation
... Restricting access to parts pf a table can be effected by using the view and grant commands Privileges can be withdrawn with the revoke command ...
... Restricting access to parts pf a table can be effected by using the view and grant commands Privileges can be withdrawn with the revoke command ...
Big Data
... (Continued) “Big data is a collection of data sets so large and complex that it becomes awkward to work with using on-hand database management tools. Difficulties include capture, storage, search, sharing, analysis, and visualization.” – Wikipedia ...
... (Continued) “Big data is a collection of data sets so large and complex that it becomes awkward to work with using on-hand database management tools. Difficulties include capture, storage, search, sharing, analysis, and visualization.” – Wikipedia ...
Document
... Establishment of a geologic framework for the USArray mission of EarthScope largely depends on community efforts that facilitate the integration of seismic data with petrologic, gravity, structural, and other geologic data. In an effort to address the needs of the GeoFrame/USArray community, EarthCh ...
... Establishment of a geologic framework for the USArray mission of EarthScope largely depends on community efforts that facilitate the integration of seismic data with petrologic, gravity, structural, and other geologic data. In an effort to address the needs of the GeoFrame/USArray community, EarthCh ...
Database Systems
... – DBMS - may be Access, Oracle, DB2,… – Users may be individuals on workstations (interactive users) or application programs – Both users and applications go through DBMS – Applications produce standard output, such as reports ...
... – DBMS - may be Access, Oracle, DB2,… – Users may be individuals on workstations (interactive users) or application programs – Both users and applications go through DBMS – Applications produce standard output, such as reports ...
Database glossary of terms
... to a key field or group of fields forming a key of another database record in some (usually different) table. Usually a foreign key in one table refers to the primary key (PK) of another table. This way references can be made to link information together and it is an essential part of database norma ...
... to a key field or group of fields forming a key of another database record in some (usually different) table. Usually a foreign key in one table refers to the primary key (PK) of another table. This way references can be made to link information together and it is an essential part of database norma ...
Chapter 13
... user access to data and user actions that can be enacted on data – Who can update? Insert? Read? ...
... user access to data and user actions that can be enacted on data – Who can update? Insert? Read? ...
THE DATABLITZ™ MAIN-MEMORY STORAGE MANAGER
... that logging facilities can be turned off for data that need not be persistent, and locking can be turned off if data is private to a process. The latter principle means that lowlevel index components are exposed to the user so that critical application components can be optimized with special imple ...
... that logging facilities can be turned off for data that need not be persistent, and locking can be turned off if data is private to a process. The latter principle means that lowlevel index components are exposed to the user so that critical application components can be optimized with special imple ...
Working interactively with VFP - dFPUG
... section in left/right part of grid IN MACDESKTOP (for separate window) Additional menu functions that sometimes might be helpfull ...
... section in left/right part of grid IN MACDESKTOP (for separate window) Additional menu functions that sometimes might be helpfull ...
Chapter 4 Exercise
... C) Composite key D) None of the above In this database model, multiple tables can be linked to each other, by using a common field in each table: A) Linking model B) Network model C) Relational model D) Hierarchical model ...
... C) Composite key D) None of the above In this database model, multiple tables can be linked to each other, by using a common field in each table: A) Linking model B) Network model C) Relational model D) Hierarchical model ...
Backup tables
... 9. Run a script to select all data from the backup table to make sure all the data rows and columns have been included in the new table. Verify that no data has been corrupted or changed. ...
... 9. Run a script to select all data from the backup table to make sure all the data rows and columns have been included in the new table. Verify that no data has been corrupted or changed. ...
Database technology
... … includes information on which devices that are created … also includes information on the total system … is the most important database on the server. If this database disappears you will have to reinstall! ...
... … includes information on which devices that are created … also includes information on the total system … is the most important database on the server. If this database disappears you will have to reinstall! ...
Chapter One (Introduction) Objectives
... No two tuples are the same No two attributes are the same The order of tuples are immaterial The order of attributes are immaterial There is an attribute or a collection of attributes which identifies tuples uniquely called Primary Key Value of attribute must be atomic ...
... No two tuples are the same No two attributes are the same The order of tuples are immaterial The order of attributes are immaterial There is an attribute or a collection of attributes which identifies tuples uniquely called Primary Key Value of attribute must be atomic ...
JSP-database
... Load a driver which is compatible with the database that is to be processed. Define and establish a connection to the database. Associate an SQL statement with this connection. Execute the SQL statement. The SQL statement which has been executed will produce a table which is stored in a ResultSet ob ...
... Load a driver which is compatible with the database that is to be processed. Define and establish a connection to the database. Associate an SQL statement with this connection. Execute the SQL statement. The SQL statement which has been executed will produce a table which is stored in a ResultSet ob ...
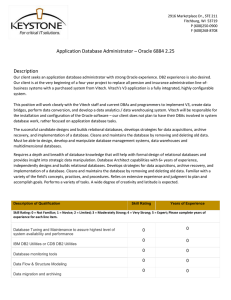
2916 Marketplace Dr., STE 211 Fitchburg, WI 53719 P (608)250
... Our client seeks an application database administrator with strong Oracle experience. DB2 experience is also desired. Our client is at the very beginning of a four year project to replace all pension and insurance administration line-ofbusiness systems with a purchased system from Vitech. Vitech's V ...
... Our client seeks an application database administrator with strong Oracle experience. DB2 experience is also desired. Our client is at the very beginning of a four year project to replace all pension and insurance administration line-ofbusiness systems with a purchased system from Vitech. Vitech's V ...
6. Database Management Systems
... • 2nd , 3rd , BCNF and 4th normal form • Decomposition, desirable properties of decomposition • Overall database design process File Structure, Indexing and Hashing: • File Organization , Organization of records in files , Data dictionary storage • Basic Indexing Concepts, rdered Indices, B+ Trees a ...
... • 2nd , 3rd , BCNF and 4th normal form • Decomposition, desirable properties of decomposition • Overall database design process File Structure, Indexing and Hashing: • File Organization , Organization of records in files , Data dictionary storage • Basic Indexing Concepts, rdered Indices, B+ Trees a ...
IP(Theory) - Kendriya Vidyalaya No. 2, Belagavi Cantt.
... (Monthly Test 4) Distribution of Project to groups Displaying Data From Multiple Tables: Cartesian product, Union, Intersection concept of Foreign Key, Equi-Join � Creating a Table with PRIMARY KEY and NOT NULL constraints, Viewing Constraints, Viewing the Columns Associated with Constraints using D ...
... (Monthly Test 4) Distribution of Project to groups Displaying Data From Multiple Tables: Cartesian product, Union, Intersection concept of Foreign Key, Equi-Join � Creating a Table with PRIMARY KEY and NOT NULL constraints, Viewing Constraints, Viewing the Columns Associated with Constraints using D ...
dbms
... T1 cancels 5 seats updating the seats reserved on Flight 890 to 75 T2 reserves 4 additional seats on the flight and updates the seats reserved on Flight 890 to 84. If T1 updates the database before T2. T2 will override T1’s change and make reservations to 84 rather than getting the correct value of ...
... T1 cancels 5 seats updating the seats reserved on Flight 890 to 75 T2 reserves 4 additional seats on the flight and updates the seats reserved on Flight 890 to 84. If T1 updates the database before T2. T2 will override T1’s change and make reservations to 84 rather than getting the correct value of ...