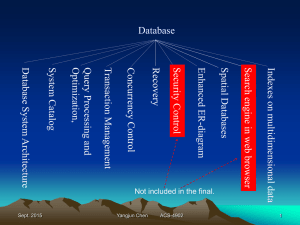
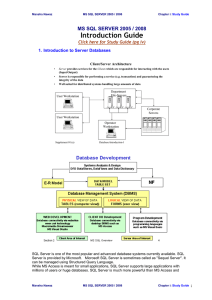
Part of chapter 7 - Software and Mind
... in the subsequent footnotes it is usually abbreviated. For these abbreviations, then, the full reference can be found by searching the previous footnotes no further back than the beginning of the current titled part. The statement “italics added” in a footnote indicates that the emphasis is only in ...
... in the subsequent footnotes it is usually abbreviated. For these abbreviations, then, the full reference can be found by searching the previous footnotes no further back than the beginning of the current titled part. The statement “italics added” in a footnote indicates that the emphasis is only in ...
Document
... • The array representation of a max-heap is not sorted. • Steps in sorting (i) Convert the given array of size n to a max-heap (BuildMaxHeap) (ii) Swap the first and last elements of the array. • Now, the largest element is in the last position – where it belongs. • That leaves n – 1 elements to be ...
... • The array representation of a max-heap is not sorted. • Steps in sorting (i) Convert the given array of size n to a max-heap (BuildMaxHeap) (ii) Swap the first and last elements of the array. • Now, the largest element is in the last position – where it belongs. • That leaves n – 1 elements to be ...
Oracle Database High Availability Overview
... The Programs are not intended for use in any nuclear, aviation, mass transit, medical, or other inherently dangerous applications. It shall be the licensee's responsibility to take all appropriate fail-safe, backup, redundancy and other measures to ensure the safe use of such applications if the Pro ...
... The Programs are not intended for use in any nuclear, aviation, mass transit, medical, or other inherently dangerous applications. It shall be the licensee's responsibility to take all appropriate fail-safe, backup, redundancy and other measures to ensure the safe use of such applications if the Pro ...
Erlang ODBC
... problem. But unfortunately there is no guarantee that all databases actually treats the ANSI data types equivalently. For instance an installation of Oracle Enterprise release 8.0.5.0.0 for unix will accept that you create a table column with the ANSI data type integer, but when retrieving values fr ...
... problem. But unfortunately there is no guarantee that all databases actually treats the ANSI data types equivalently. For instance an installation of Oracle Enterprise release 8.0.5.0.0 for unix will accept that you create a table column with the ANSI data type integer, but when retrieving values fr ...
here. - NYU Computer Science
... • (customer-id, account-number) is the super key of depositor • NOTE: this means a pair of entity sets can have at most one relationship in a particular relationship set. • E.g. if we wish to track all access-dates to each account by each ...
... • (customer-id, account-number) is the super key of depositor • NOTE: this means a pair of entity sets can have at most one relationship in a particular relationship set. • E.g. if we wish to track all access-dates to each account by each ...
Resume
... Created Availability Groups, Listener, Replicas, Endpoints, Backup Preferences, data synchronization, Readable Secondary’s in Always On Availability Groups in On premises and Azure IAAS. Improved the performance of the Queries, databases, SQL Servers, Replication, SSIS Packages, SSRS Reports, Window ...
... Created Availability Groups, Listener, Replicas, Endpoints, Backup Preferences, data synchronization, Readable Secondary’s in Always On Availability Groups in On premises and Azure IAAS. Improved the performance of the Queries, databases, SQL Servers, Replication, SSIS Packages, SSRS Reports, Window ...
Insert, Update and Delete in Access
... application that will start automatically when your computer starts and keep running always). Your program (software) which need to access the database will not access the database file directly. Instead, your program will communicate with the database service application. It is the responsibility o ...
... application that will start automatically when your computer starts and keep running always). Your program (software) which need to access the database will not access the database file directly. Instead, your program will communicate with the database service application. It is the responsibility o ...
GURGLE - GNU Report Generator Language
... predefined macros (one per line), most of which take arguments, and all of which are optional (except database of which there must be at least one, see Section 0.3.4.3 [DATABASE], page 10). These have three general forms. They can define an internal structure or process (such as how to sort or filte ...
... predefined macros (one per line), most of which take arguments, and all of which are optional (except database of which there must be at least one, see Section 0.3.4.3 [DATABASE], page 10). These have three general forms. They can define an internal structure or process (such as how to sort or filte ...
Installation Manual SW 6000 Conference Management
... 7/Vista operating system is only suitable for systems with up to 10 users. With more than 10 users, the CUI must run on a Windows Server. For systems with less than 25 users, the SQL Server Express Edition can be used. For systems with more than 25 users, it is recommended to use an SQL Server versi ...
... 7/Vista operating system is only suitable for systems with up to 10 users. With more than 10 users, the CUI must run on a Windows Server. For systems with less than 25 users, the SQL Server Express Edition can be used. For systems with more than 25 users, it is recommended to use an SQL Server versi ...
n IBM Tivoli Network Manager with DB2 Best Practices v1.1
... services of a central Database Administration, and that can affect performance as the DB administrators attempt to optimize their resources by sharing the DB2 server with other applications. Knowing how Network Manager uses the database can help avoid heavy traffic problems. Using the information in ...
... services of a central Database Administration, and that can affect performance as the DB administrators attempt to optimize their resources by sharing the DB2 server with other applications. Knowing how Network Manager uses the database can help avoid heavy traffic problems. Using the information in ...
Referential Integrity in Oracle Rdb
... SQL nomenclature for this feature. Rdb implemented three types of constraints - valid if, verb time and commit time. Traces of this terminology exist still in the Rdb product, even in the SQL syntax. This technical note provides an overview of the referential integrity features available in the Orac ...
... SQL nomenclature for this feature. Rdb implemented three types of constraints - valid if, verb time and commit time. Traces of this terminology exist still in the Rdb product, even in the SQL syntax. This technical note provides an overview of the referential integrity features available in the Orac ...
(A) R
... decomposition of R E.g. Consider R (A, B, C, D), with F = { A B, B C} Decompose R into R1(A,B) and R2(A,C,D) Neither of the dependencies in F contain only attributes from (A,C,D) so we might be mislead into thinking R2 satisfies BCNF. In fact, dependency A C in F+ shows R2 is not in BC ...
... decomposition of R E.g. Consider R (A, B, C, D), with F = { A B, B C} Decompose R into R1(A,B) and R2(A,C,D) Neither of the dependencies in F contain only attributes from (A,C,D) so we might be mislead into thinking R2 satisfies BCNF. In fact, dependency A C in F+ shows R2 is not in BC ...
Porting to DB2 Universal Database Version 8.1 from Sybase
... Database management software is now the core of enterprise computing. Companies need access to a wide range of information such as XML documents, streaming video, and other rich media types. New ways of working bring new requirements, including digital rights management. The e-business evolution mak ...
... Database management software is now the core of enterprise computing. Companies need access to a wide range of information such as XML documents, streaming video, and other rich media types. New ways of working bring new requirements, including digital rights management. The e-business evolution mak ...
Document
... Plan and Create a Database The purpose of the database. Tables to create (address) Fields in each table (Name, phone,…) ...
... Plan and Create a Database The purpose of the database. Tables to create (address) Fields in each table (Name, phone,…) ...
Hibernate_ - JBoss Issue Tracker
... Hibernate distribution (hibernate.org) Database of your choice (hsqldb preferably) SQL tables to hold your persistent objects Java classes to represent that objects in code XML mapping files Configuration file for database connection ...
... Hibernate distribution (hibernate.org) Database of your choice (hsqldb preferably) SQL tables to hold your persistent objects Java classes to represent that objects in code XML mapping files Configuration file for database connection ...
Evaluating and Comparing Oracle Database Appliance X6
... a missing post from DBWR that can cause buffer busy waits. As a workaround the _buffer_busy_wait_timeout parameter should be set to 20ms. ...
... a missing post from DBWR that can cause buffer busy waits. As a workaround the _buffer_busy_wait_timeout parameter should be set to 20ms. ...
ppt - FCN
... We define additional operations that do not add any power to the relational algebra, but that simplify common queries. ...
... We define additional operations that do not add any power to the relational algebra, but that simplify common queries. ...
TerraAmazon Administrator User´s Manual
... model database. It engages land use and land cover classification tools as well as spatial operations between vector data, allowing transitions analysis among other applications. TerraAmazon keeps work time records for project control. It´s functionalities are extensible through plugins, such as the ...
... model database. It engages land use and land cover classification tools as well as spatial operations between vector data, allowing transitions analysis among other applications. TerraAmazon keeps work time records for project control. It´s functionalities are extensible through plugins, such as the ...
Lecture13-Nov16
... database system where COUGAR extends the Cornell PREDATOR objectrelational database system. In COUGAR, each type of sensor is modeled as a new Abstract Data Type (ADT). Signal-processing functions are modeled as ADT functions that return sensor data. Long-running queries are formulated in SQL. To su ...
... database system where COUGAR extends the Cornell PREDATOR objectrelational database system. In COUGAR, each type of sensor is modeled as a new Abstract Data Type (ADT). Signal-processing functions are modeled as ADT functions that return sensor data. Long-running queries are formulated in SQL. To su ...
ERModelling
... one or more cars each. Each car has associated with it zero to any number of recorded accidents. Each insurance policy covers one or more cars, and has one or more premium payments associated with it. Each payment is for a particular period of time, and has an associated due date, and the date when ...
... one or more cars each. Each car has associated with it zero to any number of recorded accidents. Each insurance policy covers one or more cars, and has one or more premium payments associated with it. Each payment is for a particular period of time, and has an associated due date, and the date when ...
Towards Sensor Database Systems
... database system where COUGAR extends the Cornell PREDATOR objectrelational database system. In COUGAR, each type of sensor is modeled as a new Abstract Data Type (ADT). Signal-processing functions are modeled as ADT functions that return sensor data. Long-running queries are formulated in SQL. To su ...
... database system where COUGAR extends the Cornell PREDATOR objectrelational database system. In COUGAR, each type of sensor is modeled as a new Abstract Data Type (ADT). Signal-processing functions are modeled as ADT functions that return sensor data. Long-running queries are formulated in SQL. To su ...
TMF Introduction - Hewlett Packard Enterprise
... Refer to this manual for information about how to use the TMFCOM command interface to the TMF software. This manual includes syntax, cautionary considerations, and command examples for TMFCOM. TMF Application Programmer’s Guide Read this guide for information about how to design requester and server ...
... Refer to this manual for information about how to use the TMFCOM command interface to the TMF software. This manual includes syntax, cautionary considerations, and command examples for TMFCOM. TMF Application Programmer’s Guide Read this guide for information about how to design requester and server ...