Appendix G: When is a DBMS Relational?
... that the full power and implications of the relational approach were being distorted, Codd specified 12 rules (13 with Rule 0, the foundational rule) for a relational DBMS (Codd, 1985a,b). These rules form a yardstick against which the “real” relational DBMS products can be identified. Over the year ...
... that the full power and implications of the relational approach were being distorted, Codd specified 12 rules (13 with Rule 0, the foundational rule) for a relational DBMS (Codd, 1985a,b). These rules form a yardstick against which the “real” relational DBMS products can be identified. Over the year ...
Lecture12 - The University of Texas at Dallas
... low-trust, low security scenarios. The levels of identity assurance that may be required for a given scenario are also being standardized through a common and open Identity Assurance Framework. It can involve user-centric use-cases, as well as enterprise- ...
... low-trust, low security scenarios. The levels of identity assurance that may be required for a given scenario are also being standardized through a common and open Identity Assurance Framework. It can involve user-centric use-cases, as well as enterprise- ...
Oracle Active Data Guard Best Practices Standby For More Than
... – No Brainer – Just point it at your Active Data Guard standby! ...
... – No Brainer – Just point it at your Active Data Guard standby! ...
Finding Time: SAS® and Data Warehouse Solutions for Determining Last Day of the Month
... We use production reports to monitor performance of the portfolio or response to a campaign on an ongoing basis. We also run production jobs to create data sets as input files for other systems. These reports or files are produced on a monthly basis where only the most recent month’s data need to be ...
... We use production reports to monitor performance of the portfolio or response to a campaign on an ongoing basis. We also run production jobs to create data sets as input files for other systems. These reports or files are produced on a monthly basis where only the most recent month’s data need to be ...
Module 1 - Faculty Websites
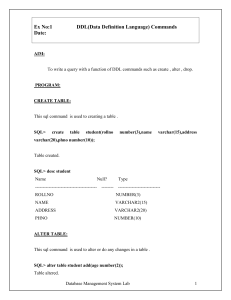
... • Renaming the Default Primary Key Field • To rename the ID field to the VisitID field: • Right-click the ID column heading to open the shortcut menu, and then click Rename Field. The column heading ID is selected, so that whatever text you type next will replace it • Type VisitID and then click the ...
... • Renaming the Default Primary Key Field • To rename the ID field to the VisitID field: • Right-click the ID column heading to open the shortcut menu, and then click Rename Field. The column heading ID is selected, so that whatever text you type next will replace it • Type VisitID and then click the ...
Developer 2000
... There are two main styles for forms. A Tabular layout arranges the field labels across the top of the form with a number of records below as in a spreadsheet. A Form layout places the field labels to the left of the fields. Generally only one record is displayed at a time. 5.select the title and the ...
... There are two main styles for forms. A Tabular layout arranges the field labels across the top of the form with a number of records below as in a spreadsheet. A Form layout places the field labels to the left of the fields. Generally only one record is displayed at a time. 5.select the title and the ...
CUSTOMER_CODE SMUDE DIVISION_CODE SMUDE
... NORMAL: This is default mode for shutting down the database. The oracle server waits for all currently connected users to disconnected users to disconnect their sessions. No new connections are permitted. A checkpoint is performed on the entire database and the files are closed. When a database is s ...
... NORMAL: This is default mode for shutting down the database. The oracle server waits for all currently connected users to disconnected users to disconnect their sessions. No new connections are permitted. A checkpoint is performed on the entire database and the files are closed. When a database is s ...
security of database systems - Computer Science and Engineering
... In SQL this privilege is further divided into UPDATE, DELETE, and INSERT privileges to apply the corresponding SQL command to R. In addition, both the INSERT and UPDATE privileges can specify that only certain attributes of R can be updated by the account. REFERENCES privilege on R: This gives the ...
... In SQL this privilege is further divided into UPDATE, DELETE, and INSERT privileges to apply the corresponding SQL command to R. In addition, both the INSERT and UPDATE privileges can specify that only certain attributes of R can be updated by the account. REFERENCES privilege on R: This gives the ...
Chapter 6
... Multiple tables can be queried by using either subqueries or joins If all of the result data comes from a single table, subqueries can be used If results come from two or more tables, joins must be used Joins cannot substitute for correlated subqueries nor for queries that involve EXISTS and ...
... Multiple tables can be queried by using either subqueries or joins If all of the result data comes from a single table, subqueries can be used If results come from two or more tables, joins must be used Joins cannot substitute for correlated subqueries nor for queries that involve EXISTS and ...
person-name
... Reduction of an E-R Schema to Tables Primary keys allow entity sets and relationship sets to be ...
... Reduction of an E-R Schema to Tables Primary keys allow entity sets and relationship sets to be ...
Data Mining – Commonly Used SQL Statements
... You can use Structured Query Language (SQL) to query, update, and manage relational databases. You can also use it to retrieve, sort, and filter specific data from any database. A database contains one or more table(s), where each table contains records with relevant information. In GENESIS32 for ex ...
... You can use Structured Query Language (SQL) to query, update, and manage relational databases. You can also use it to retrieve, sort, and filter specific data from any database. A database contains one or more table(s), where each table contains records with relevant information. In GENESIS32 for ex ...
Radius + MySQL Authentification and Accounting
... • Configure usage.cgi and radius.cgi to your own environment (user and password to access database, directories) ...
... • Configure usage.cgi and radius.cgi to your own environment (user and password to access database, directories) ...
Database System Concepts, 6 th Ed
... Younger transactions never wait for older ones; they are rolled back ...
... Younger transactions never wait for older ones; they are rolled back ...
Lecture 6: SQL II - NYU Computer Science
... • In evaluating SQL queries, any row that evaluates to False or Unknown is eliminated. • Two rows are duplicates if the corresponding columns are either equal or both unknown. • Arithmetic operations all return NULL if one of the arguments is NULL • Be very careful with aggregates ...
... • In evaluating SQL queries, any row that evaluates to False or Unknown is eliminated. • Two rows are duplicates if the corresponding columns are either equal or both unknown. • Arithmetic operations all return NULL if one of the arguments is NULL • Be very careful with aggregates ...
Gavin Payne
... • Traditionally a very Unix/Linux focussed product • But today Windows is just as common, if not more ...
... • Traditionally a very Unix/Linux focussed product • But today Windows is just as common, if not more ...
Interfacing Spatial Statistics sofware and GIS: a case study TerraLib
... Oracle, PostGIS, MySQL and SQLServer ...
... Oracle, PostGIS, MySQL and SQLServer ...
Group-based Replication of On-line Transaction Processing Servers*
... locally and replies to the client. Upon the reception of the remote transaction’s commit outcome each replica applies t’s state changes through the execution of a high priority transaction consisting of updates, inserts and deletes according to t’s previously multicast write-values. The high priori ...
... locally and replies to the client. Upon the reception of the remote transaction’s commit outcome each replica applies t’s state changes through the execution of a high priority transaction consisting of updates, inserts and deletes according to t’s previously multicast write-values. The high priori ...
Access Tutorial 14: Data Access Objects
... 14. Data Access Objects x = “one” & “_two” means that the variable x is equal to the string one_two. If you understand these constructs at this point, then understanding the DLookUp() function is just a matter of putting the pieces together one by one. 14.3.5.1 Using DLookUp() in queries The DLookU ...
... 14. Data Access Objects x = “one” & “_two” means that the variable x is equal to the string one_two. If you understand these constructs at this point, then understanding the DLookUp() function is just a matter of putting the pieces together one by one. 14.3.5.1 Using DLookUp() in queries The DLookU ...
department of computer sceinece - Kasturba Gandhi College for
... across time and space enhancing the speed of data communication and information dissemination and also have infinite applications in various fields like Science, technology, commerce, business and entertainment. Study of Computer Science would improve the opportunities of the students in the job mar ...
... across time and space enhancing the speed of data communication and information dissemination and also have infinite applications in various fields like Science, technology, commerce, business and entertainment. Study of Computer Science would improve the opportunities of the students in the job mar ...
Lecture 6: Query optimization, query tuning
... important for the choices made when planning query execution. • Time for operations grow (at least) linearly with size of (largest) argument. (Note that we do not have indexes for intermediate results.) • The total size can even be used as a crude estimate on the running time. ...
... important for the choices made when planning query execution. • Time for operations grow (at least) linearly with size of (largest) argument. (Note that we do not have indexes for intermediate results.) • The total size can even be used as a crude estimate on the running time. ...