SQL Server Developer
... ❏ Created Triggers that produces primary key (unique) automatically when a new record is inserted into the database. The intention is to maintain unique records to eliminate duplicate records. ❏ Generated multiple Enterprise reports using SSRS from SQL Server Database (OLTP) and included various re ...
... ❏ Created Triggers that produces primary key (unique) automatically when a new record is inserted into the database. The intention is to maintain unique records to eliminate duplicate records. ❏ Generated multiple Enterprise reports using SSRS from SQL Server Database (OLTP) and included various re ...
Transaction
... as a transaction, but after executing these statements, thinks better of it and issues a ROLLBACK statement If Peter executes his statements after (ins) but before the rollback, he’d see a value (35) that never existed in the database ...
... as a transaction, but after executing these statements, thinks better of it and issues a ROLLBACK statement If Peter executes his statements after (ins) but before the rollback, he’d see a value (35) that never existed in the database ...
Storage and File Structure
... non-volatile, used primarily for backup (to recover from disk failure), and for archival data sequential-access – much slower than disk very high capacity (40 to 300 GB tapes available) Tape jukeboxes available for storing massive amounts of data ...
... non-volatile, used primarily for backup (to recover from disk failure), and for archival data sequential-access – much slower than disk very high capacity (40 to 300 GB tapes available) Tape jukeboxes available for storing massive amounts of data ...
WebSphere Commerce Top DB2 Performance Problems
... • Inadequate bufferpool size • On a database server which is running only DB2 with a single Websphere Commerce database on a single instance, 75% of the physical memory on the machine can be allocated for bufferpool • Use only one large bufferpool • If using one bufferpool, size it to the minimum of ...
... • Inadequate bufferpool size • On a database server which is running only DB2 with a single Websphere Commerce database on a single instance, 75% of the physical memory on the machine can be allocated for bufferpool • Use only one large bufferpool • If using one bufferpool, size it to the minimum of ...
SQL Injection
... • The best security measure is one that catches problems before they are revealed. • As part of QAT or UAT testing, applications must be automatically scanned for vulnerabilities. • Reveals vulnerabilities above and beyond simple ...
... • The best security measure is one that catches problems before they are revealed. • As part of QAT or UAT testing, applications must be automatically scanned for vulnerabilities. • Reveals vulnerabilities above and beyond simple ...
Databases and MySQL in 21 minutes
... Multiple tables and joins • if desired info comes from multiple tables, this implies a "join" operator to relate data in different tables – in effect join makes a big table for later selection select title, count from books, stock where books.isbn = stock.isbn; select * from books, sales where book ...
... Multiple tables and joins • if desired info comes from multiple tables, this implies a "join" operator to relate data in different tables – in effect join makes a big table for later selection select title, count from books, stock where books.isbn = stock.isbn; select * from books, sales where book ...
Best Practices: Physical Database Design for OLTP
... v Disjoint sets of data and the seldom reuse of data leads to a large working set size that results in a low buffer pool hit ratio and frequent page cleaning. v Relatively simple queries that do not include complex joins or the ORDER BY clause. v Stringent uptime requirements. For example, database ...
... v Disjoint sets of data and the seldom reuse of data leads to a large working set size that results in a low buffer pool hit ratio and frequent page cleaning. v Relatively simple queries that do not include complex joins or the ORDER BY clause. v Stringent uptime requirements. For example, database ...
Lecture5
... • Example : The following SQL creates a DEFAULT constraint on the "City" column when the "Persons" table is created: ...
... • Example : The following SQL creates a DEFAULT constraint on the "City" column when the "Persons" table is created: ...
Molecular biological databases: evolutionary history, data modeling
... Relations differ from ordinary tables and flat files as they are not sensitive to the ordering of tuples and ordering of attributes and values within a tuple. In relational databases various restrictions can be applied to the data. They are called „constraints‟ and classified into inherent model-bas ...
... Relations differ from ordinary tables and flat files as they are not sensitive to the ordering of tuples and ordering of attributes and values within a tuple. In relational databases various restrictions can be applied to the data. They are called „constraints‟ and classified into inherent model-bas ...
Dynamic Database Browsing
... Step 1: Obtain a sample DDB-compatible .KML from the PerCon website at http://www.perconcorp.com/ddb_demo.kml . Step 2: Clicking the above link or copying/pasting the above URL into a web browser should automatically load the .KML file in Google Earth. If Google Earth loads automatically, skip to St ...
... Step 1: Obtain a sample DDB-compatible .KML from the PerCon website at http://www.perconcorp.com/ddb_demo.kml . Step 2: Clicking the above link or copying/pasting the above URL into a web browser should automatically load the .KML file in Google Earth. If Google Earth loads automatically, skip to St ...
Application Development in Web Mapping 2. Spatial Data Storage
... To store spatial data in files sometimes is a good solution. However using a database to store geometry has some advantages: • Attributes and geometry of features are stored together. • Spatial indexing makes drawing faster at larger scales. • Spatial databases allow you to perform spatial queries a ...
... To store spatial data in files sometimes is a good solution. However using a database to store geometry has some advantages: • Attributes and geometry of features are stored together. • Spatial indexing makes drawing faster at larger scales. • Spatial databases allow you to perform spatial queries a ...
Storing Unstructured Data in SQL Server 2008
... audio formats have further extended the range of unstructured data formats that are used for business data. Additionally, dramatic reductions in the cost of storage hardware and memory have significantly affected the amount and type of data that is stored in computer systems, and led to the emergenc ...
... audio formats have further extended the range of unstructured data formats that are used for business data. Additionally, dramatic reductions in the cost of storage hardware and memory have significantly affected the amount and type of data that is stored in computer systems, and led to the emergenc ...
SQL Stored Procedures
... INSERT trigger - The trigger is fired when the attempt is made to insert a row in the trigger table. After the INSERT statement is executed the new row is added to the Inserted table. DELETE trigger - It is fired when the attempt is made to delete the row from the trigger table. The deleted rows ...
... INSERT trigger - The trigger is fired when the attempt is made to insert a row in the trigger table. After the INSERT statement is executed the new row is added to the Inserted table. DELETE trigger - It is fired when the attempt is made to delete the row from the trigger table. The deleted rows ...
Stasis: Flexible Transactional Storage Russell Sears and Eric Brewer
... Updates from aborted transactions should not be applied, so we also need to log commit records; a transaction commits when its commit record correctly reaches the disk. Recovery starts with an analysis phase that determines all of the outstanding transactions and their fate. The redo phase then appl ...
... Updates from aborted transactions should not be applied, so we also need to log commit records; a transaction commits when its commit record correctly reaches the disk. Recovery starts with an analysis phase that determines all of the outstanding transactions and their fate. The redo phase then appl ...
Document
... key value Ki, or to a bucket of pointers to file records, each record having search-key value Ki. Only need bucket structure if search-key does not form a primary key. If Li, Lj are leaf nodes and i < j, Li’s search-key values are less than Lj’s ...
... key value Ki, or to a bucket of pointers to file records, each record having search-key value Ki. Only need bucket structure if search-key does not form a primary key. If Li, Lj are leaf nodes and i < j, Li’s search-key values are less than Lj’s ...
12Access.12 - unix.eng.ua.edu
... • If you want to print a graphical view of the relationships in your database, you can have Access print the relationships window. • This will print exactly what you see when you open this window. • If you need to have more detailed information about the objects in the database, you can run the Docu ...
... • If you want to print a graphical view of the relationships in your database, you can have Access print the relationships window. • This will print exactly what you see when you open this window. • If you need to have more detailed information about the objects in the database, you can run the Docu ...
Database - La Salle University
... units of information that will be contained in a single file. These are known as the entities. An entity is somewhat similar to an object in programming, it collects data that belongs together in some immediate way. Entities also separate the data into distinct units. Database entities often reflect ...
... units of information that will be contained in a single file. These are known as the entities. An entity is somewhat similar to an object in programming, it collects data that belongs together in some immediate way. Entities also separate the data into distinct units. Database entities often reflect ...
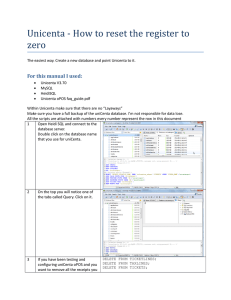
Unicenta - How to reset the register to zero
... Unicenta - How to reset the register to zero - sql03.txt Unicenta - How to reset the register to zero - sql07.txt Unicenta - How to reset the register to zero - sql09.txt Unicenta - How to reset the register to zero - sql10.txt Unicenta - How to reset the register to zero - sql11.txt ...
... Unicenta - How to reset the register to zero - sql03.txt Unicenta - How to reset the register to zero - sql07.txt Unicenta - How to reset the register to zero - sql09.txt Unicenta - How to reset the register to zero - sql10.txt Unicenta - How to reset the register to zero - sql11.txt ...
Database Management System - The Institute of Finance
... that we have defined name as being functionally dependent on SSN. The idea of a functional dependency is to define one field as an anchor (link) from which one can always find a single value for another field. ...
... that we have defined name as being functionally dependent on SSN. The idea of a functional dependency is to define one field as an anchor (link) from which one can always find a single value for another field. ...