Constructing Large Proposition Databases
... provider reads articles from a Wikipedia database and then uses a language specific filter to remove markups and other items that would otherwise impede the process of parsing. Wikipedia is available in the form of XML dump files1 provided by the Wikimedia Foundation. Although XML is a suitable form ...
... provider reads articles from a Wikipedia database and then uses a language specific filter to remove markups and other items that would otherwise impede the process of parsing. Wikipedia is available in the form of XML dump files1 provided by the Wikimedia Foundation. Although XML is a suitable form ...
How to Write a DML Trigger
... INSTEAD OF – When an INSERT, UPDATE or DELETE occurs, instead of the typical code executed, the trigger executes instead. You have to code the effective INSERT, UPDATE or DELETE . AFTER – When an INSERT, UPDATE or DELETE occurs, the typical operation occurs, and then the coded object executes. The u ...
... INSTEAD OF – When an INSERT, UPDATE or DELETE occurs, instead of the typical code executed, the trigger executes instead. You have to code the effective INSERT, UPDATE or DELETE . AFTER – When an INSERT, UPDATE or DELETE occurs, the typical operation occurs, and then the coded object executes. The u ...
PHP MySQL Introduction
... There is one other thing you should be aware of in this database. The id field will also be set as PRIMARY, INDEX, UNIQUE and will be set to auto_increment (found under Extra in PH PMyAdmin). The reason for this is that this will be the field identifier (primary and index) and so must be unique. The ...
... There is one other thing you should be aware of in this database. The id field will also be set as PRIMARY, INDEX, UNIQUE and will be set to auto_increment (found under Extra in PH PMyAdmin). The reason for this is that this will be the field identifier (primary and index) and so must be unique. The ...
Introduction to DB2
... Only one root page is available per Index.It should exist at the highest level of the hierarchy.It can be structured as Leaf pages or Non leaf pages. ...
... Only one root page is available per Index.It should exist at the highest level of the hierarchy.It can be structured as Leaf pages or Non leaf pages. ...
Paper
... cryptographic approach that achieves a fine-grained data access control. It provides a way of defining access policies based on different attributes of the requester, environment, or the data object. Especially, cipher text-policy attribute-based encryption (CPABE) enables an encryptor to define the ...
... cryptographic approach that achieves a fine-grained data access control. It provides a way of defining access policies based on different attributes of the requester, environment, or the data object. Especially, cipher text-policy attribute-based encryption (CPABE) enables an encryptor to define the ...
Automated Ranking of Database Query Results
... inappropriate bucket boundaries may separate two values that are actually close to each other, (b) determining the correct number of buckets is not easy, and (c) values in different buckets are treated as completely dissimilar, regardless of the actual distance separating the buckets. Instead, we pr ...
... inappropriate bucket boundaries may separate two values that are actually close to each other, (b) determining the correct number of buckets is not easy, and (c) values in different buckets are treated as completely dissimilar, regardless of the actual distance separating the buckets. Instead, we pr ...
LABELVIEW 2015 Tutorial
... The Add New Object window allows you to add multiple objects at once. The objects are grouped according to their type in four tabs: Tables, Views, Procedures ( or Functions) and Synonyms. You may select one or several objects by holding the CTRL key and then press the Add Object button to add these ...
... The Add New Object window allows you to add multiple objects at once. The objects are grouped according to their type in four tabs: Tables, Views, Procedures ( or Functions) and Synonyms. You may select one or several objects by holding the CTRL key and then press the Add Object button to add these ...
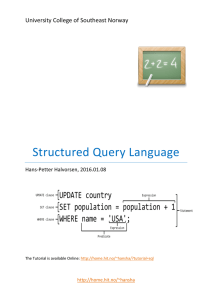
Structured Query Language
... SQL Server uses T-SQL (Transact-SQL). T-SQL is Microsoft's proprietary extension to SQL. TSQL is very similar to standard SQL, but in addition it supports some extra functionality, builtin functions, etc. T-SQL expands on the SQL standard to include procedural programming, local variables, various ...
... SQL Server uses T-SQL (Transact-SQL). T-SQL is Microsoft's proprietary extension to SQL. TSQL is very similar to standard SQL, but in addition it supports some extra functionality, builtin functions, etc. T-SQL expands on the SQL standard to include procedural programming, local variables, various ...
Chapter Notes
... Application architecture evolved with the rise of dot-com and web-based companies. This new client/server architecture is based on the web and is therefore referred to as a web application. A web application uses the web to connect and communicate to the server. A web application uses HTML page crea ...
... Application architecture evolved with the rise of dot-com and web-based companies. This new client/server architecture is based on the web and is therefore referred to as a web application. A web application uses the web to connect and communicate to the server. A web application uses HTML page crea ...
A Relational Data Warehouse for Multidimensional - CEUR
... Process mining can be categorized in three different kinds: (1) Process discovery extracts a process model from the event log reflecting its behavior, (2) conformance checking compares an event log to a manually created or previously discovered process model to measure the quality of the process mo ...
... Process mining can be categorized in three different kinds: (1) Process discovery extracts a process model from the event log reflecting its behavior, (2) conformance checking compares an event log to a manually created or previously discovered process model to measure the quality of the process mo ...
chapter 1 - Sacramento - California State University
... LAMP (Linux, Apache, MySQL, PHP/ Pearl/ Python). MySQL is flexible since it can work on different platforms like Linux, Windows, Unix, BSD (Mac OS X), Handheld (Windows CE). MySQL gives both open source freedom and 24 X 7 supports The new MySQL Enterprise improved the application performance and eff ...
... LAMP (Linux, Apache, MySQL, PHP/ Pearl/ Python). MySQL is flexible since it can work on different platforms like Linux, Windows, Unix, BSD (Mac OS X), Handheld (Windows CE). MySQL gives both open source freedom and 24 X 7 supports The new MySQL Enterprise improved the application performance and eff ...
paper - VLDB Endowment
... as much as possible up-to-date such that the work of refresh transactions (whenever needed) is reduced and thus the performance of the overall system is increased. We assume that a globally serializable schedule is produced for all update sites by some algorithm that is of no concern for this paper. ...
... as much as possible up-to-date such that the work of refresh transactions (whenever needed) is reduced and thus the performance of the overall system is increased. We assume that a globally serializable schedule is produced for all update sites by some algorithm that is of no concern for this paper. ...
PowerPoint Chapter 11
... on server side oriented to ensure that DBMS is properly configured to respond to clients’ requests in fastest way possible while making optimum use of existing resources • DBMS architecture is represented by many processes and structures (in memory and in permanent storage) used to manage a database ...
... on server side oriented to ensure that DBMS is properly configured to respond to clients’ requests in fastest way possible while making optimum use of existing resources • DBMS architecture is represented by many processes and structures (in memory and in permanent storage) used to manage a database ...
Chapter 11
... on server side oriented to ensure that DBMS is properly configured to respond to clients’ requests in fastest way possible while making optimum use of existing resources • DBMS architecture is represented by many processes and structures (in memory and in permanent storage) used to manage a database ...
... on server side oriented to ensure that DBMS is properly configured to respond to clients’ requests in fastest way possible while making optimum use of existing resources • DBMS architecture is represented by many processes and structures (in memory and in permanent storage) used to manage a database ...
focus on: fdr/upstream`s online database solutions
... FDR/UPSTREAM for Exchange provides powerful online database agents. The UPSTREAM specialized agents overcome the problem that normal file system solutions have with trying to backup the databases, as they are always open and access to them is denied. A result of the agent support is that the protec ...
... FDR/UPSTREAM for Exchange provides powerful online database agents. The UPSTREAM specialized agents overcome the problem that normal file system solutions have with trying to backup the databases, as they are always open and access to them is denied. A result of the agent support is that the protec ...
Chapter 17: Parallel Databases
... Queries/transactions execute in parallel with one another. Increases transaction throughput; used primarily to scale up a ...
... Queries/transactions execute in parallel with one another. Increases transaction throughput; used primarily to scale up a ...
SQL virtual database Release Notes
... The WITH TABLOCK keyword is no longer required when running DBCC CHECKDB against virtual databases, resulting in a more thorough integrity check and improved performance. ...
... The WITH TABLOCK keyword is no longer required when running DBCC CHECKDB against virtual databases, resulting in a more thorough integrity check and improved performance. ...
Security and the Data Warehouse
... required by their job functions. In addition, other features, such as roles and stored procedures, not only allow you to control which privileges a user has, but under what conditions he can use those privileges. While privileges let you restrict the types of operations a user can perform, managing ...
... required by their job functions. In addition, other features, such as roles and stored procedures, not only allow you to control which privileges a user has, but under what conditions he can use those privileges. While privileges let you restrict the types of operations a user can perform, managing ...
Mimer SQL embedded in healthcare industry equipment
... The sdbgen program can be executed without any arguments and will in that case prompt for information needed. Generate the default configuration file (multidefs) for the database server by using the following command: mimcontrol –g ...
... The sdbgen program can be executed without any arguments and will in that case prompt for information needed. Generate the default configuration file (multidefs) for the database server by using the following command: mimcontrol –g ...
StealthAUDIT System Requirements and Installation
... Each DC must connect to a target host in order to obtain data during an audit. Most Windows® administrative data is obtained via RPC; hence, a shared RPC connection is utilized. StealthAUDIT Data Collectors expose Windows®-based administrative data by calling into the Windows API functions in the sa ...
... Each DC must connect to a target host in order to obtain data during an audit. Most Windows® administrative data is obtained via RPC; hence, a shared RPC connection is utilized. StealthAUDIT Data Collectors expose Windows®-based administrative data by calling into the Windows API functions in the sa ...