SQL and SAS/ACCESS Differences and Interrelationships
... the SAS/ACCESS Interface to 082 allows the user to view. extract, manipulate and load data to and from a 082 database. Similarly, the SAS/ACCESS Interface to ORACLE provides an interface to an ORACLE database. SAS/ACCESS software will always Include the ACCESS procedure. In addition, many of the SAS ...
... the SAS/ACCESS Interface to 082 allows the user to view. extract, manipulate and load data to and from a 082 database. Similarly, the SAS/ACCESS Interface to ORACLE provides an interface to an ORACLE database. SAS/ACCESS software will always Include the ACCESS procedure. In addition, many of the SAS ...
btgrubu.com
... • Design databases to meet technical and business requirements • Understand the impact of changes to applications • Develop new applications that leverage existing data assets • Locate and explain data that our company uses to make decisions • Reuse designs and design patterns • Train people that ar ...
... • Design databases to meet technical and business requirements • Understand the impact of changes to applications • Develop new applications that leverage existing data assets • Locate and explain data that our company uses to make decisions • Reuse designs and design patterns • Train people that ar ...
Chapter 10
... Spatiotemporal phenomena Dynamic geographic entities are characterized not only by spatial and attribute components, but also by temporal ...
... Spatiotemporal phenomena Dynamic geographic entities are characterized not only by spatial and attribute components, but also by temporal ...
SQL_Saturday_#527_
... Why is this better? Eliminated nested SP calls which resulted in a single record insert/update Loaded all data into temp table in one query Grouped records allow for all hospitals per measure instead of just one at a time Eliminated performance killing cursors A loop was still needed beca ...
... Why is this better? Eliminated nested SP calls which resulted in a single record insert/update Loaded all data into temp table in one query Grouped records allow for all hospitals per measure instead of just one at a time Eliminated performance killing cursors A loop was still needed beca ...
this PDF file - Studia Informatica
... Menu Activity, Table Size provides information about which tables were involved in activity and how many records were added or deleted from each table. 3.9. Client Monitor The Client Monitor is the most important tool used to monitor Navision performance and troubleshoot locking problems. It can als ...
... Menu Activity, Table Size provides information about which tables were involved in activity and how many records were added or deleted from each table. 3.9. Client Monitor The Client Monitor is the most important tool used to monitor Navision performance and troubleshoot locking problems. It can als ...
Chapter 21:Application Development and Administration
... (select customer-name,account-number from depositor, inserted where inserted.account-number = depositor.account-number) insert into loan values (inserted.account-number, inserted.branch-name, – inserted.balance) update account set balance = 0 from account, inserted where account.account-number = ins ...
... (select customer-name,account-number from depositor, inserted where inserted.account-number = depositor.account-number) insert into loan values (inserted.account-number, inserted.branch-name, – inserted.balance) update account set balance = 0 from account, inserted where account.account-number = ins ...
Designing and implementing a web-based data warehouse solution
... For some of the agreements in the system, invoice data is created periodically by a report server. Since only fixed costs are stored in the system, the variable traffic-related costs are retrieved from an external system owned by the telecom operator. These costs are then mapped to the subscriptions ...
... For some of the agreements in the system, invoice data is created periodically by a report server. Since only fixed costs are stored in the system, the variable traffic-related costs are retrieved from an external system owned by the telecom operator. These costs are then mapped to the subscriptions ...
ppt - CSE, IIT Bombay
... (select customer-name,account-number from depositor, inserted where inserted.account-number = depositor.account-number) insert into loan values (inserted.account-number, inserted.branch-name, – inserted.balance) update account set balance = 0 from account, inserted where account.account-number = ins ...
... (select customer-name,account-number from depositor, inserted where inserted.account-number = depositor.account-number) insert into loan values (inserted.account-number, inserted.branch-name, – inserted.balance) update account set balance = 0 from account, inserted where account.account-number = ins ...
Triggers Writeup
... To keep track of modification of data along with the user name, the operation performed and the time when the operation was performed To prevent invalid transaction Enforces complex security authorization Database Triggers Vs Procedures Triggers do not accept parameters whereas procedures ca ...
... To keep track of modification of data along with the user name, the operation performed and the time when the operation was performed To prevent invalid transaction Enforces complex security authorization Database Triggers Vs Procedures Triggers do not accept parameters whereas procedures ca ...
Access Project 1 - Maryville University
... column Press TAB Press TAB again (because Text is the correct data type) Type Client Number (Primary Key) for description Click the Primary Key button on the Table Design toolbar Press F6 key (to move to the bottom Field Properties) Type 4 for size of Client Number field Press F6 key to return to De ...
... column Press TAB Press TAB again (because Text is the correct data type) Type Client Number (Primary Key) for description Click the Primary Key button on the Table Design toolbar Press F6 key (to move to the bottom Field Properties) Type 4 for size of Client Number field Press F6 key to return to De ...
Using BIRT Analytics Loader
... document may be reproduced or transmitted in any form, or by any means, electronic or mechanical, for any purpose, in whole or in part, without the express written permission of Actuate Corporation. © 2003 - 2013 by Actuate Corporation. All rights reserved. Printed in the United States of America. C ...
... document may be reproduced or transmitted in any form, or by any means, electronic or mechanical, for any purpose, in whole or in part, without the express written permission of Actuate Corporation. © 2003 - 2013 by Actuate Corporation. All rights reserved. Printed in the United States of America. C ...
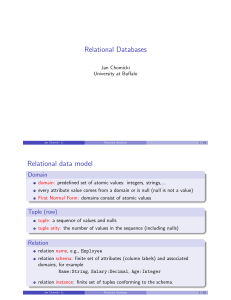
Relational Databases - CSE Buffalo
... each operator takes one or two relations as arguments and returns a relation as the result operators can be nested to form expressions procedural query language: expressions describe how the query can be ...
... each operator takes one or two relations as arguments and returns a relation as the result operators can be nested to form expressions procedural query language: expressions describe how the query can be ...
PrefIndex: An Efficient Supergraph Containment Search Technique
... contained by q. As fa is a subgraph of ga and gb , it will be searched for two more times in q for the verifications of ga and gb . Generally speaking, if a feature f is contained by n candidates, the subgraph isomorphism test on f against q will be repeated (n + 1) times (including one test in the fi ...
... contained by q. As fa is a subgraph of ga and gb , it will be searched for two more times in q for the verifications of ga and gb . Generally speaking, if a feature f is contained by n candidates, the subgraph isomorphism test on f against q will be repeated (n + 1) times (including one test in the fi ...
TMs and ORBs - Microsoft Research
... me the next 10 records.” The requirement for such service requests arises with SQL cursors. First, there is the OPEN CURSOR call, which causes the SELECT statement to be executed and all the context information in the database system to be built up. As was shown, this results in an rmCall to the sql ...
... me the next 10 records.” The requirement for such service requests arises with SQL cursors. First, there is the OPEN CURSOR call, which causes the SELECT statement to be executed and all the context information in the database system to be built up. As was shown, this results in an rmCall to the sql ...
Introduction to Oracle
... VARCHAR2(length) – sequence of characters (up to 4000) NVARCHAR2(length) – sequence of Unicode characters DATE – date and time, e.g. "18-June-2015 20:30:07" ...
... VARCHAR2(length) – sequence of characters (up to 4000) NVARCHAR2(length) – sequence of Unicode characters DATE – date and time, e.g. "18-June-2015 20:30:07" ...
ppt - Avi Silberschatz
... (select customer-name,account-number from depositor, inserted where inserted.account-number = depositor.account-number) insert into loan values (inserted.account-number, inserted.branch-name, – inserted.balance) update account set balance = 0 from account, inserted where account.account-number = ins ...
... (select customer-name,account-number from depositor, inserted where inserted.account-number = depositor.account-number) insert into loan values (inserted.account-number, inserted.branch-name, – inserted.balance) update account set balance = 0 from account, inserted where account.account-number = ins ...
Android.content.SharedPreferences … A developer can
... Server implementation (SQL-CS) that uses client-side hashing to determine the home node/shard for each record by modifying the client-side application that runs the YCSB benchmark. We implemented this client-side sharding so that we could compare MongoDB(-AS) with SQL Server in a cluster environment ...
... Server implementation (SQL-CS) that uses client-side hashing to determine the home node/shard for each record by modifying the client-side application that runs the YCSB benchmark. We implemented this client-side sharding so that we could compare MongoDB(-AS) with SQL Server in a cluster environment ...
Environment Optimization Guide
... If the Relativity roles are not virtualized, there will likely be a mirrored array housing the OS and required Relativity components (unless you’re also booting from the storage device). If these disks are heavily fragmented, roles including the web servers (IIS) may experience poor performance that ...
... If the Relativity roles are not virtualized, there will likely be a mirrored array housing the OS and required Relativity components (unless you’re also booting from the storage device). If these disks are heavily fragmented, roles including the web servers (IIS) may experience poor performance that ...
the data warehouse backroom
... and sequences. The objects can also be grouped into containers where iterative processing, such as looping through data sets, can be applied. Variables: There are two kinds of variables in SSIS: User-defined and system variables, the variables can be accessed both by SSIS objects like containers, ...
... and sequences. The objects can also be grouped into containers where iterative processing, such as looping through data sets, can be applied. Variables: There are two kinds of variables in SSIS: User-defined and system variables, the variables can be accessed both by SSIS objects like containers, ...
OS3e_13
... – Problem of allocating and freeing space on secondary storage is somewhat like that experienced in primary storage allocation under variable-partition multiprogramming – Contiguous allocation systems have generally been replaced by more dynamic noncontiguous allocation systems • Files tend to grow ...
... – Problem of allocating and freeing space on secondary storage is somewhat like that experienced in primary storage allocation under variable-partition multiprogramming – Contiguous allocation systems have generally been replaced by more dynamic noncontiguous allocation systems • Files tend to grow ...
Chapter 13: File and Database Systems
... – Problem of allocating and freeing space on secondary storage is somewhat like that experienced in primary storage allocation under variable-partition multiprogramming – Contiguous allocation systems have generally been replaced by more dynamic noncontiguous allocation systems • Files tend to grow ...
... – Problem of allocating and freeing space on secondary storage is somewhat like that experienced in primary storage allocation under variable-partition multiprogramming – Contiguous allocation systems have generally been replaced by more dynamic noncontiguous allocation systems • Files tend to grow ...
CGI Programming: Part 1 Robert M. Dondero, Ph.D. Princeton University 1
... Python interpreter used by CS Apache Web server is old, and is missing MySQLdb module Hard-code Python interpreter location when using CS Apache Web server ...
... Python interpreter used by CS Apache Web server is old, and is missing MySQLdb module Hard-code Python interpreter location when using CS Apache Web server ...
CHAPTER 3
... different applications and by different human data administrators and end users. We need to deal with multiple (possibly changing) interpretations of data by different user in different context, data inconsistencies, and incomplete information.” ...
... different applications and by different human data administrators and end users. We need to deal with multiple (possibly changing) interpretations of data by different user in different context, data inconsistencies, and incomplete information.” ...