No Slide Title - Virginia Tech
... – traditional telephone and voice-mail – cable television (mostly residence halls) – IP/IPX/AppleTalk network layer and below • Exception: DNS and DHCP ...
... – traditional telephone and voice-mail – cable television (mostly residence halls) – IP/IPX/AppleTalk network layer and below • Exception: DNS and DHCP ...
HG556a INSTALLATION GUIDE AND USER MANUAL
... Procedure for enabling the Wi-Fi connection The initial configuration for the Wi-Fi radio interface of the HG556a is Disabled. To enable the Wi-Fi connection, do as follows: 1. Press the Wi-Fi button on the side panel of HG556a. 2. Once the button is pressed and held, the Wi-Fi indicator turns red i ...
... Procedure for enabling the Wi-Fi connection The initial configuration for the Wi-Fi radio interface of the HG556a is Disabled. To enable the Wi-Fi connection, do as follows: 1. Press the Wi-Fi button on the side panel of HG556a. 2. Once the button is pressed and held, the Wi-Fi indicator turns red i ...
IPSO-6LoWPAN - University of California, Berkeley
... • Originating node and Final node specified by either short (16 bit) or EUID (64 bit) 802.15.4 address – In addition to IP source and destination ...
... • Originating node and Final node specified by either short (16 bit) or EUID (64 bit) 802.15.4 address – In addition to IP source and destination ...
Computer Networks Addressing
... Best effort service Network does his best effort to forward packets ...
... Best effort service Network does his best effort to forward packets ...
Point-to-Point Protocol (PPP)
... Multilink is especially useful with ISDN BRI configurations, in which both B channels can be used to achieve 128kbps throughput. MLP also works with modems to provide additional bandwidth. This protocol was first supported in Cisco IOS Release ...
... Multilink is especially useful with ISDN BRI configurations, in which both B channels can be used to achieve 128kbps throughput. MLP also works with modems to provide additional bandwidth. This protocol was first supported in Cisco IOS Release ...
VENDOR PROFILE Tata Communications Ethernet Portfolio and
... IDC believes that the market for global Ethernet services is evolving into a second phase of offerings now that major Ethernet service providers have had several years of experience, Ethernet technology has matured, and many service providers' Ethernet services have achieved MEF certification. Wirel ...
... IDC believes that the market for global Ethernet services is evolving into a second phase of offerings now that major Ethernet service providers have had several years of experience, Ethernet technology has matured, and many service providers' Ethernet services have achieved MEF certification. Wirel ...
Chapter 5 - Department of Computer Engineering
... point-to-point link between Ethernet switch and host ...
... point-to-point link between Ethernet switch and host ...
PowerPoint
... Each layer depends on the ones below it, but can often detect and/or recover from errors in those lower layers Real networks do not always obey this strict layered model – Multiprotocol Label Switching (MPLS) is “layer 2.5” – Routers may perform processing based on layer-4 header content (firewa ...
... Each layer depends on the ones below it, but can often detect and/or recover from errors in those lower layers Real networks do not always obey this strict layered model – Multiprotocol Label Switching (MPLS) is “layer 2.5” – Routers may perform processing based on layer-4 header content (firewa ...
Deep Packet Inspection - Computer Science and Engineering
... Algorithm comparison Implementation details – Regular expression – DFA & NFA – Detection engine ...
... Algorithm comparison Implementation details – Regular expression – DFA & NFA – Detection engine ...
Internetworking, higher layer protocols TCP/IP and ATM Eytan Modiano Massachusetts Institute of Technology
... All packets associated with a session follow the same path Route is chosen at start of session Packets are labeled with a VC# designating the route The VC number must be unique on a given link but can change from link to link Imagine having to set up connections between 1000 nodes in a mesh Unique V ...
... All packets associated with a session follow the same path Route is chosen at start of session Packets are labeled with a VC# designating the route The VC number must be unique on a given link but can change from link to link Imagine having to set up connections between 1000 nodes in a mesh Unique V ...
Network Routing - Yale University
... can change ISP without changing addresses of devices in local network can change addresses of devices in local network without notifying outside world ...
... can change ISP without changing addresses of devices in local network can change addresses of devices in local network without notifying outside world ...
TCP/IP Protocol Suite (Internet Model)
... Q2-1. What is the first principle we discussed in this chapter for protocol layering that needs to be followed to make the communication bidirectional? We need to make each layer so that it is able to perform two opposite tasks, one in each direction. Q2-2. Which layers of the TCP/IP protocol suite ...
... Q2-1. What is the first principle we discussed in this chapter for protocol layering that needs to be followed to make the communication bidirectional? We need to make each layer so that it is able to perform two opposite tasks, one in each direction. Q2-2. Which layers of the TCP/IP protocol suite ...
VPNs
... ISPs had 100’s of routers, each of which logically had a link to all others Was difficult to manage and run routing over all of these logical links ...
... ISPs had 100’s of routers, each of which logically had a link to all others Was difficult to manage and run routing over all of these logical links ...
IP: Addresses and Forwarding - RPI ECSE
... Forwarding: Simple “next-hop” forwarding. Last hop forwards directly to destination Best-effort delivery : No error reporting. Delay, out-of-order, corruption, and loss possible => problem of higher layers! Forwarding vs routing: Routing tables setup by separate algorithm (s) ...
... Forwarding: Simple “next-hop” forwarding. Last hop forwards directly to destination Best-effort delivery : No error reporting. Delay, out-of-order, corruption, and loss possible => problem of higher layers! Forwarding vs routing: Routing tables setup by separate algorithm (s) ...
chapter5
... A time stamp is initialized by the sender to the expected transfer time of the packet. Any packet is destroyed, if its delay is greater than its time stamp. Each router remembers (using a per source sequence number) which packets have been received before, and destroys duplicates ...
... A time stamp is initialized by the sender to the expected transfer time of the packet. Any packet is destroyed, if its delay is greater than its time stamp. Each router remembers (using a per source sequence number) which packets have been received before, and destroys duplicates ...
collision
... B receives ARP packet, replies to A with its (B's) physical layer address A caches (saves) IP-to-physical address pairs ...
... B receives ARP packet, replies to A with its (B's) physical layer address A caches (saves) IP-to-physical address pairs ...
TCP/IP Basics
... A more efficient way to assign IP addresses than using IP address “classes” The network and host addresses boundary is not always made on octet boundaries, but may be made any specific number of bits from the beginning of the address Steal bits from the network address for use in the host address an ...
... A more efficient way to assign IP addresses than using IP address “classes” The network and host addresses boundary is not always made on octet boundaries, but may be made any specific number of bits from the beginning of the address Steal bits from the network address for use in the host address an ...
chap05
... reliable delivery between adjacent nodes we learned how to do this already (chapter 3)! seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? ...
... reliable delivery between adjacent nodes we learned how to do this already (chapter 3)! seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? ...
QualNet tutorial 1
... cse2017-pc01 ~ cse2017-pc12: E8400 3G 6M cache cse2027-pc01 ~ cse2027-pc08: E8400 cse2023-pc01 ~ cse2023-pc08: E8400 jun01 ~ jun24: E6750 2.66G 4M cache navy Don’t run QualNet on Indigo/Red Only one process in one computer. Our QualNet license only supports 30 processes simultaneously. ...
... cse2017-pc01 ~ cse2017-pc12: E8400 3G 6M cache cse2027-pc01 ~ cse2027-pc08: E8400 cse2023-pc01 ~ cse2023-pc08: E8400 jun01 ~ jun24: E6750 2.66G 4M cache navy Don’t run QualNet on Indigo/Red Only one process in one computer. Our QualNet license only supports 30 processes simultaneously. ...
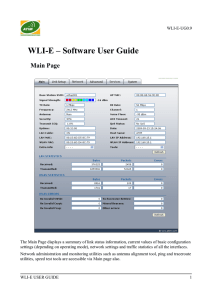
WLI-E – Software User Guide
... Port Forwarding creates a transparent tunnel through a firewall/NAT, granting an access from the WAN side to the particular network service running on the LAN side. ...
... Port Forwarding creates a transparent tunnel through a firewall/NAT, granting an access from the WAN side to the particular network service running on the LAN side. ...
lectures1-2-3
... datagram A’s NIC sends frame and R’s NIC receives it R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get B’s MAC address (R has B’s IP address, included in the just received frame) R creates frame containing A-to-B IP datagram and sends it to B ...
... datagram A’s NIC sends frame and R’s NIC receives it R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get B’s MAC address (R has B’s IP address, included in the just received frame) R creates frame containing A-to-B IP datagram and sends it to B ...
Token Ring Cards - Personal.psu.edu
... Switches and bridges generally learn about the segments they are connected to As packets arrive, they build up a table which lists the network address used on the various network segments Sometimes, a loop would be created which caused the wrong packets to be sent on incorrect segments. These packet ...
... Switches and bridges generally learn about the segments they are connected to As packets arrive, they build up a table which lists the network address used on the various network segments Sometimes, a loop would be created which caused the wrong packets to be sent on incorrect segments. These packet ...
Our network - TalkTalk Business
... from customer premises to the network. Ethernet fibre costs are a function of distance from customer premises to the network. The success of TalkTalk means that we have: A deeply built access network - 1,695 exchanges High capacity core and transit network to the edge ...
... from customer premises to the network. Ethernet fibre costs are a function of distance from customer premises to the network. The success of TalkTalk means that we have: A deeply built access network - 1,695 exchanges High capacity core and transit network to the edge ...
3rd Edition, Chapter 5
... call setup, teardown for each call before data can flow each packet carries VC identifier (not destination ID) every switch on source-dest path maintain “state” for each ...
... call setup, teardown for each call before data can flow each packet carries VC identifier (not destination ID) every switch on source-dest path maintain “state” for each ...