G:\Aethra (Aztech)\Starbridge E
... After every change save the configuration and restart the Modem/Router. During the process of restart, the DSL indicator will go off, followed by the ETH/ACT indicator. Once you see the ETH/ACT indicator lights up and DSL indicator flickers, it meas that the restart process is completed. Please ref ...
... After every change save the configuration and restart the Modem/Router. During the process of restart, the DSL indicator will go off, followed by the ETH/ACT indicator. Once you see the ETH/ACT indicator lights up and DSL indicator flickers, it meas that the restart process is completed. Please ref ...
of the packet
... – it requires no initial exchange of control information to establish an end-to-end connection before packets are forwarded – nor does it require additional fields in the PDU header to maintain this connection. ...
... – it requires no initial exchange of control information to establish an end-to-end connection before packets are forwarded – nor does it require additional fields in the PDU header to maintain this connection. ...
Telecommunications Concepts - Vrije Universiteit Brussel
... • Data Link : similar to HDLC or 802.2, but with bytes – Payload encapsulated in P frames – Frame delimited by 802.2 flag (01111110) – Character stuffing within the frame – Optional error correction with sliding window • Network Layer : support for different protocols – Connection management, with a ...
... • Data Link : similar to HDLC or 802.2, but with bytes – Payload encapsulated in P frames – Frame delimited by 802.2 flag (01111110) – Character stuffing within the frame – Optional error correction with sliding window • Network Layer : support for different protocols – Connection management, with a ...
COMS 4995-1 Networking Laboratory
... To determine the size of the fragments we recall that, since there are only 13 bits available for the fragment offset, the offset is given as a multiple of eight bytes. As a result, the first and second fragment have a size of 996 bytes (and not 1000 bytes). This number is chosen since 976 is the la ...
... To determine the size of the fragments we recall that, since there are only 13 bits available for the fragment offset, the offset is given as a multiple of eight bytes. As a result, the first and second fragment have a size of 996 bytes (and not 1000 bytes). This number is chosen since 976 is the la ...
Chapter 5 part 2 - Distributed Computing Group
... – receiving adapter doesn’t send ACKs or NAKs to sending adapter – stream of datagrams passed to network layer can have gaps, which will be filled if app is using TCP or seen by application ...
... – receiving adapter doesn’t send ACKs or NAKs to sending adapter – stream of datagrams passed to network layer can have gaps, which will be filled if app is using TCP or seen by application ...
Evolution of Data Networks
... Workstation-Based • Aggregate bandwidth – 1/2 of the I/O bus bandwidth – capacity shared among all hosts connected to switch – example: 800Mbps bus can support 8 T3 ports • Packets-per-second – must be able to switch small packets – 100,000 packets-persecond is achievable – e.g., 64-byte packets im ...
... Workstation-Based • Aggregate bandwidth – 1/2 of the I/O bus bandwidth – capacity shared among all hosts connected to switch – example: 800Mbps bus can support 8 T3 ports • Packets-per-second – must be able to switch small packets – 100,000 packets-persecond is achievable – e.g., 64-byte packets im ...
Chapter 36
... Networking technologies, such as Ethernet, Token Ring and FDDI provide a data link layer function, that is, they allow a reliable connection between one node and another on the same network. They do not provide for inter-networking where data can be transferred from one network to another or one net ...
... Networking technologies, such as Ethernet, Token Ring and FDDI provide a data link layer function, that is, they allow a reliable connection between one node and another on the same network. They do not provide for inter-networking where data can be transferred from one network to another or one net ...
TRILL Link
... Introduce a new Hierarchical L2VPN architecture with RBridge and IP/MPLS It is an informational draft because it requires no changes to the TRILL or MPLS standards ...
... Introduce a new Hierarchical L2VPN architecture with RBridge and IP/MPLS It is an informational draft because it requires no changes to the TRILL or MPLS standards ...
Congestion Control Outline: Queuing Discipline
... • While connection-oriented networks have setup protocols, best-effort connectionless networks don’t – they need some sort of reservation protocl in order to offer QoS. – Internet resource reservation corresponds to signaling in ATM – Proposed Internet standard is called RSVP ...
... • While connection-oriented networks have setup protocols, best-effort connectionless networks don’t – they need some sort of reservation protocl in order to offer QoS. – Internet resource reservation corresponds to signaling in ATM – Proposed Internet standard is called RSVP ...
COMET—COMBO Ethernet Tester
... In current days, networks are still getting faster. e spread of mobile technologies and voice/video services (e.g. Video-on-demand) causes that users rely on high speed of their connection. erefore, Internet Service Providers (ISP) and network operators need to test and diagnose their high-speed net ...
... In current days, networks are still getting faster. e spread of mobile technologies and voice/video services (e.g. Video-on-demand) causes that users rely on high speed of their connection. erefore, Internet Service Providers (ISP) and network operators need to test and diagnose their high-speed net ...
Cisco S2 C4 - YSU Computer Science & Information Systems
... • display the CDP updates on the local router – device identifiers -- e.g. the router's configured host name and domain – name (if any) – address list -- at least one address for SNMP, up to one address for each supported protocol – port identifier -- e.g. Ethernet 0, Ethernet 1, and Serial0 – capab ...
... • display the CDP updates on the local router – device identifiers -- e.g. the router's configured host name and domain – name (if any) – address list -- at least one address for SNMP, up to one address for each supported protocol – port identifier -- e.g. Ethernet 0, Ethernet 1, and Serial0 – capab ...
ATM Networks
... meeting timing/QoS requirements of voice, video (versus Internet best-effort model) “next generation” telephony: technical roots in telephone world packet-switching (fixed length packets, called “cells”) using virtual circuits ...
... meeting timing/QoS requirements of voice, video (versus Internet best-effort model) “next generation” telephony: technical roots in telephone world packet-switching (fixed length packets, called “cells”) using virtual circuits ...
3rd Edition, Chapter 5
... meeting timing/QoS requirements of voice, video (versus Internet best-effort model) “next generation” telephony: technical roots in telephone world packet-switching (fixed length packets, called “cells”) using virtual circuits ...
... meeting timing/QoS requirements of voice, video (versus Internet best-effort model) “next generation” telephony: technical roots in telephone world packet-switching (fixed length packets, called “cells”) using virtual circuits ...
Final Presentation - High Speed Digital Systems Laboratory
... networking packets of type UDP, TCP, IP, Ethernet Full control over UDP and TCP ports should be provided to user of Packet Generator Full control over IP addresses should be provided to user of Packet Generator UDP and TCP and IP checksums must be calculated and set in packets headers A user ...
... networking packets of type UDP, TCP, IP, Ethernet Full control over UDP and TCP ports should be provided to user of Packet Generator Full control over IP addresses should be provided to user of Packet Generator UDP and TCP and IP checksums must be calculated and set in packets headers A user ...
Cisco RV110W Wireless
... The Cisco RV110W Wireless-N VPN Firewall provides simple, affordable, highly secure, business-class connectivity to the Internet for small offices/home offices and remote workers. The Cisco RV110W combines wired and wireless connectivity for small offices and remote workers with a highspeed, 802.11n ...
... The Cisco RV110W Wireless-N VPN Firewall provides simple, affordable, highly secure, business-class connectivity to the Internet for small offices/home offices and remote workers. The Cisco RV110W combines wired and wireless connectivity for small offices and remote workers with a highspeed, 802.11n ...
Draft CCNA 3
... Module 11: TCP/IP Transport and Application Layers 11.1 TCP/IP Transport Layer 11.2 TCP/IP Application Layer Case Study: Structured Cabling What has changed from CCNA versions 2.x? More information on optical and wireless More cable testing terminology and concepts More details on the operation of ...
... Module 11: TCP/IP Transport and Application Layers 11.1 TCP/IP Transport Layer 11.2 TCP/IP Application Layer Case Study: Structured Cabling What has changed from CCNA versions 2.x? More information on optical and wireless More cable testing terminology and concepts More details on the operation of ...
downloading
... tcpdump used to view network traffic on the wire basic usage: # tcpdump [-e] [-n] -i if0 [expr.] ... where if0 is your interface (e.g.: em0) ...
... tcpdump used to view network traffic on the wire basic usage: # tcpdump [-e] [-n] -i if0 [expr.] ... where if0 is your interface (e.g.: em0) ...
networks
... warning state sent back to the source via choke packet. Source reduces traffic to that destination by a fixed % (e.g., ATM) ...
... warning state sent back to the source via choke packet. Source reduces traffic to that destination by a fixed % (e.g., ATM) ...
IP Address - Zoo - Yale University
... can change ISP without changing addresses of devices in local network can change addresses of devices in local network without notifying outside world ...
... can change ISP without changing addresses of devices in local network can change addresses of devices in local network without notifying outside world ...
the sending adapter inserts the destination adapter`s MAC address
... This protocol is CSMA with collision detection capabilities. How an adapter works with CSMA/CD? The adapter works as follows: 1. The adapter obtains a datagram from the network layer, prepares a link-layer frame, and puts the frame in the adapter buffer. 2. If the adapter senses that the channel is ...
... This protocol is CSMA with collision detection capabilities. How an adapter works with CSMA/CD? The adapter works as follows: 1. The adapter obtains a datagram from the network layer, prepares a link-layer frame, and puts the frame in the adapter buffer. 2. If the adapter senses that the channel is ...
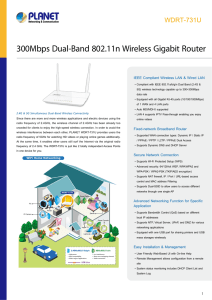
300Mbps Dual-Band 802.11n Wireless Gigabit Router
... crowded for clients to enjoy the high-speed wireless connection. In order to avoid the wireless interference between each other, PLANET WDRT-731U provides users the radio frequency of 5GHz for watching HD videos or playing online games additionally. At the same time, it enables other users still sur ...
... crowded for clients to enjoy the high-speed wireless connection. In order to avoid the wireless interference between each other, PLANET WDRT-731U provides users the radio frequency of 5GHz for watching HD videos or playing online games additionally. At the same time, it enables other users still sur ...
OSI
... > Data terminal equipment (DTEs), which include terminals, personal computers, routers and bridges. > Data circuit-terminating equipment (DCEs), which transmit the data through the network and are often carrier-owned devices. Frame Relay virtual circuit fall into 2 categories: > switched virtual c ...
... > Data terminal equipment (DTEs), which include terminals, personal computers, routers and bridges. > Data circuit-terminating equipment (DCEs), which transmit the data through the network and are often carrier-owned devices. Frame Relay virtual circuit fall into 2 categories: > switched virtual c ...
Networks and TCP/IP Part 2
... TCP – Transmission Control Protocol One protocol on how data may be transmitted between addresses TCP: ...
... TCP – Transmission Control Protocol One protocol on how data may be transmitted between addresses TCP: ...
AREN - ASC
... Commands you must know and love: ping (the daddy of them all) traceroute (tracert in Microsoft land) ipconfig (ipconfig /all for details) ...
... Commands you must know and love: ping (the daddy of them all) traceroute (tracert in Microsoft land) ipconfig (ipconfig /all for details) ...