Reorder Notifying TCP (RN-TCP) with Explicit Packet Drop Notification (EPDN)
... Section 1.1 presents the previous work related to our study. Section 2 presents the details of our proposed solution. In Sections 6,7, 8 , 9, 10 and 11 , we describe and discuss our simulations. We conclude this paper with a summary of our work and a short discussion of the further research in Secti ...
... Section 1.1 presents the previous work related to our study. Section 2 presents the details of our proposed solution. In Sections 6,7, 8 , 9, 10 and 11 , we describe and discuss our simulations. We conclude this paper with a summary of our work and a short discussion of the further research in Secti ...
Cisco Catalyst 2950 Series Intelligent Ethernet
... Intelligence at the Metro Access Edge: Enabling Profitable Ethernet Services Service providers that address the residential and SOHO market face the continual challenge of offering compelling value-added services. Although alternative broadband technologies such as DSL can offer bandwidth at speeds ...
... Intelligence at the Metro Access Edge: Enabling Profitable Ethernet Services Service providers that address the residential and SOHO market face the continual challenge of offering compelling value-added services. Although alternative broadband technologies such as DSL can offer bandwidth at speeds ...
The Network Layer
... A “flow” is a number in the IPv6 header that can be used by routers to see which packets belong to the ...
... A “flow” is a number in the IPv6 header that can be used by routers to see which packets belong to the ...
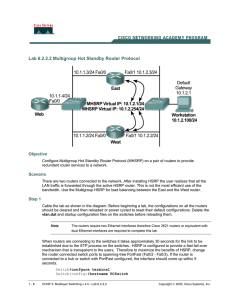
Lab 6.2.2.2 Multigroup Hot Standby Router Protocol
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
Product Description
... © 2015 ZTE Corporation. All rights reserved. ZTE CONFIDENTIAL: This document contains proprietary information of ZTE and is not to be disclosed or used without the prior written permission of ZTE. Due to update and improvement of ZTE products and technologies, information in this document is subject ...
... © 2015 ZTE Corporation. All rights reserved. ZTE CONFIDENTIAL: This document contains proprietary information of ZTE and is not to be disclosed or used without the prior written permission of ZTE. Due to update and improvement of ZTE products and technologies, information in this document is subject ...
Study on a Fast OSPF Route Reconstruction Method Under Network
... ISPs and the government reexamined the plan for disaster estimation and protection against disasters. According to this protection plan, commercial ISPs must reconstruct robust networks against disasters. Networks require high reliability and fast recovery. One of the important problems for these re ...
... ISPs and the government reexamined the plan for disaster estimation and protection against disasters. According to this protection plan, commercial ISPs must reconstruct robust networks against disasters. Networks require high reliability and fast recovery. One of the important problems for these re ...
Address Resolution Protocol
... ARP caching is the method of storing network addresses and the associated data-link addresses in memory for a period of time as the addresses are learned. This minimizes the use of valuable network resources to broadcast for the same address each time a datagram is sent. The cache entries must be ma ...
... ARP caching is the method of storing network addresses and the associated data-link addresses in memory for a period of time as the addresses are learned. This minimizes the use of valuable network resources to broadcast for the same address each time a datagram is sent. The cache entries must be ma ...
Reorder Density (RD): A Formal, Comprehensive Metric for Packet Reordering
... insufficient [15]. Percentage does not capture the amount by which a packet is out of order. The amount of displacement of a packet directly influences the complexity of hardware/software to recover from the reordering. In the case of a sequence such as (1,3,4,2,5), if buffers are available to store ...
... insufficient [15]. Percentage does not capture the amount by which a packet is out of order. The amount of displacement of a packet directly influences the complexity of hardware/software to recover from the reordering. In the case of a sequence such as (1,3,4,2,5), if buffers are available to store ...
The Network Layer - London South Bank University
... b) In Unicast routing, when a router receives a packet, it forwards the packet thru only one of its ports as defined in the routing table. The router may discard the packet if it cannot find the destination address c) Questions: In dynamic routing, how does the router decides to which network should ...
... b) In Unicast routing, when a router receives a packet, it forwards the packet thru only one of its ports as defined in the routing table. The router may discard the packet if it cannot find the destination address c) Questions: In dynamic routing, how does the router decides to which network should ...
TCP, IGP, EGP etc. - La Salle University
... The routing table contains a list of known routers, the addresses they can reach, and a cost for each path. ...
... The routing table contains a list of known routers, the addresses they can reach, and a cost for each path. ...
Lecture 3 TCP/IP model
... A: It depends on the application. TCP provides a connection-oriented, reliable, byte stream service (lots of overhead). UDP offers minimal datagram delivery service (as little overhead as possible). ...
... A: It depends on the application. TCP provides a connection-oriented, reliable, byte stream service (lots of overhead). UDP offers minimal datagram delivery service (as little overhead as possible). ...
ipv6 ospf - AfNOG 2017 Workshop on Network Technology
... External route Routes imported into OSPF from another routing protocol by an ASBR ...
... External route Routes imported into OSPF from another routing protocol by an ASBR ...
Powerpoint
... External route Routes imported into OSPF from another routing protocol by an ASBR ...
... External route Routes imported into OSPF from another routing protocol by an ASBR ...
the document - Support
... The encryption algorithms DES/3DES/SKIPJACK/RC2/RSA (RSA-1024 or lower)/MD2/MD4/MD5 (in digital signature scenarios and password encryption)/SHA1 (in digital signature scenarios) have a low security, which may bring security risks. If protocols allowed, using more secure encryption algorithms, such ...
... The encryption algorithms DES/3DES/SKIPJACK/RC2/RSA (RSA-1024 or lower)/MD2/MD4/MD5 (in digital signature scenarios and password encryption)/SHA1 (in digital signature scenarios) have a low security, which may bring security risks. If protocols allowed, using more secure encryption algorithms, such ...
RARP / BOOTP / DHCP
... must complete the DHCP transaction to be compliant with the DHCP protocol (steps 3. & 4.). The DHCPOFFER packet contains the DHCP option 43 (vendor specific information) carrying a list of boot server IP addresses. 5. DHCPREQUEST to selected boot server: The client sends a DHCPREQUEST with the same ...
... must complete the DHCP transaction to be compliant with the DHCP protocol (steps 3. & 4.). The DHCPOFFER packet contains the DHCP option 43 (vendor specific information) carrying a list of boot server IP addresses. 5. DHCPREQUEST to selected boot server: The client sends a DHCPREQUEST with the same ...
THE OPTIMIZATION OF STEPPING STONE DETECTION: PACKET CAPTURING STEPS MOHD NIZAM OMAR
... (Intrusion Response System) can be defined as IDS that detects an attack and immediately responds to remove the intruder from the network [4]. IDS and IRS are related. Both of these systems can use packet capturing program as their main source to detect and respond. IDS detects intrusion while IRS r ...
... (Intrusion Response System) can be defined as IDS that detects an attack and immediately responds to remove the intruder from the network [4]. IDS and IRS are related. Both of these systems can use packet capturing program as their main source to detect and respond. IDS detects intrusion while IRS r ...
Packet Tracer Network Simulator
... brief description on other end devices such as tablets and televisions. End devices are the ones used by end users, with desktops and laptops being the most common ones. Chapter 4, Creating a Network Topology, explains different connectors, creating network topologies, and configuring them with Cisc ...
... brief description on other end devices such as tablets and televisions. End devices are the ones used by end users, with desktops and laptops being the most common ones. Chapter 4, Creating a Network Topology, explains different connectors, creating network topologies, and configuring them with Cisc ...
Motorola 2247-62-10NA AdminHandbookV782
... This Administrator’s Handbook covers the advanced features of the Motorola Netopia® 2200- 3300and 7000-Series Gateway family. Your Motorola Netopia® equipment offers advanced configuration features accessed through the Webbased interface screens and the Command Line Interface (CLI). This Administrat ...
... This Administrator’s Handbook covers the advanced features of the Motorola Netopia® 2200- 3300and 7000-Series Gateway family. Your Motorola Netopia® equipment offers advanced configuration features accessed through the Webbased interface screens and the Command Line Interface (CLI). This Administrat ...
router isis as42
... Integrated IS-IS carries CLNS and IPv4 address families RFC5308 adds IPv6 address family support RFC5120 adds multi-topology support ...
... Integrated IS-IS carries CLNS and IPv4 address families RFC5308 adds IPv6 address family support RFC5120 adds multi-topology support ...
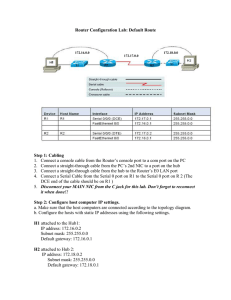
3 Router Configuration - Cisco Networking Academy
... b. Use some show commands to look around in your neighbor’s R1. c. Exit out of their R1 by typing exit Note: If you can NOT telnet to your neighbor’s Router, it is because the routing protocols and network numbers might not be configured properly, or the host names might not be configured properly. ...
... b. Use some show commands to look around in your neighbor’s R1. c. Exit out of their R1 by typing exit Note: If you can NOT telnet to your neighbor’s Router, it is because the routing protocols and network numbers might not be configured properly, or the host names might not be configured properly. ...
Multiprotocol Label Switching (MPLS)
... Comparison of MPLS versus ATM • While the underlying protocols and technologies are different, both MPLS and ATM provide a connection-oriented service for transporting data across computer networks. • Excluding differences in the signaling protocols there still remain significant differences in the ...
... Comparison of MPLS versus ATM • While the underlying protocols and technologies are different, both MPLS and ATM provide a connection-oriented service for transporting data across computer networks. • Excluding differences in the signaling protocols there still remain significant differences in the ...
No Slide Title
... of a node without a server or manual configuration: 1. Upon startup, a node create link-local addresses for each IPv6 interface from MAC address 2. Test uniqueness by sending a Neighbor Solicitation to the created address ...
... of a node without a server or manual configuration: 1. Upon startup, a node create link-local addresses for each IPv6 interface from MAC address 2. Test uniqueness by sending a Neighbor Solicitation to the created address ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... packet losses than a standard TCP flow, and therefore maintains fairness to other competing regular TCP flows. So it also improves the RTT fairness compared to standard TCP. ...
... packet losses than a standard TCP flow, and therefore maintains fairness to other competing regular TCP flows. So it also improves the RTT fairness compared to standard TCP. ...
Wireless Router Setup Manual
... How to Set Up and Test Basic Wireless Connectivity Follow the instructions below to set up and test basic wireless connectivity. Once you have established basic wireless connectivity, you can enable security settings appropriate to your needs. 1. Log in to the router at http://www.routerlogin.net wi ...
... How to Set Up and Test Basic Wireless Connectivity Follow the instructions below to set up and test basic wireless connectivity. Once you have established basic wireless connectivity, you can enable security settings appropriate to your needs. 1. Log in to the router at http://www.routerlogin.net wi ...
document
... Version number - OSPF version number, most recent version 2 Type - OSPF packet type following the header 1 - Hello - Establishes and maintains neighbor relationships. 2 - Database description - contents of the topological database upon adjacency formation 3 - Link State request - Requests pieces of ...
... Version number - OSPF version number, most recent version 2 Type - OSPF packet type following the header 1 - Hello - Establishes and maintains neighbor relationships. 2 - Database description - contents of the topological database upon adjacency formation 3 - Link State request - Requests pieces of ...