Chapter 2 - Slide DataComm file - Elearning-KL
... In developing the model, the designers distilled the process of transmitting data to its most fundamental elements. They identified which networking functions had related uses and collected those functions into discrete groups that became the layers. Each layers defines a family of functions disti ...
... In developing the model, the designers distilled the process of transmitting data to its most fundamental elements. They identified which networking functions had related uses and collected those functions into discrete groups that became the layers. Each layers defines a family of functions disti ...
GridNM Network Monitoring Architecture
... Rate of tank filling < rate of water flow out i.e. application not fast enough to fill socket buffer past threshold BUT - needs further investigation ...
... Rate of tank filling < rate of water flow out i.e. application not fast enough to fill socket buffer past threshold BUT - needs further investigation ...
Internet - Introduction
... networks which form and act as a single huge network for transport of data and messages across distances which can be anywhere from the same office to anywhere in the world. ...
... networks which form and act as a single huge network for transport of data and messages across distances which can be anywhere from the same office to anywhere in the world. ...
CMPT 880: Internet Architectures and Protocols
... Q: does the IP address of the host on which the process runs suffice for identifying the process? A: No, many processes can be running on same host ...
... Q: does the IP address of the host on which the process runs suffice for identifying the process? A: No, many processes can be running on same host ...
Web Server Administration - Edinboro University of
... TCP/IP – Transmission Control Protocol/Internet Protocol (language of the internet) IP Address – Internet Protocol Address ...
... TCP/IP – Transmission Control Protocol/Internet Protocol (language of the internet) IP Address – Internet Protocol Address ...
Chapter2R - Radford University
... Ethernet frame is broadcast by server NIC and captured by router NIC NIC examines protocol type field and then delivers packet to its IP layer IP layer examines IP packet destination address and determines IP packet should be routed to (2,2) Router’s table indicates (2,2) is directly connected via P ...
... Ethernet frame is broadcast by server NIC and captured by router NIC NIC examines protocol type field and then delivers packet to its IP layer IP layer examines IP packet destination address and determines IP packet should be routed to (2,2) Router’s table indicates (2,2) is directly connected via P ...
The Internet
... requires network to support quality of service of some sort hard to integrate into current architecture store-and-forward => shared buffers => traffic interaction => hard to provide service quality requires endpoint to signal to the network what it wants but Internet does not have a simple way ...
... requires network to support quality of service of some sort hard to integrate into current architecture store-and-forward => shared buffers => traffic interaction => hard to provide service quality requires endpoint to signal to the network what it wants but Internet does not have a simple way ...
Automation of Batch Vacuum Pans At D.R.B.C Sugar Factory
... If SH does not receive ACK, it assumes disconnection and changes the window size of the sender to 0 - Choking Maintain TCP end-to-end semantics Packet loss due to error bits is propagated to sender Freeze TCP True end-to-end scheme and does not require the involvement of any intermediaries (such as ...
... If SH does not receive ACK, it assumes disconnection and changes the window size of the sender to 0 - Choking Maintain TCP end-to-end semantics Packet loss due to error bits is propagated to sender Freeze TCP True end-to-end scheme and does not require the involvement of any intermediaries (such as ...
Network Architectures - Computing Sciences
... another packet. – Similar to placing an envelope containing a letter inside another envelope (which may have a different address). – sometimes the encapsulating packet is of a different protocol. ...
... another packet. – Similar to placing an envelope containing a letter inside another envelope (which may have a different address). – sometimes the encapsulating packet is of a different protocol. ...
Seminar - IEC 61850
... SSD Files : System Specification description Files , contains details of SLD , Logical Nodes & their type . ICD Files – These files contains IED description , map IED’s with Logical devices. ...
... SSD Files : System Specification description Files , contains details of SLD , Logical Nodes & their type . ICD Files – These files contains IED description , map IED’s with Logical devices. ...
15.1 Networking
... 3.1.2 Outline the importance of standards in the construction of networks. 2. Outline the importance of standards in the construction of networks. ...
... 3.1.2 Outline the importance of standards in the construction of networks. 2. Outline the importance of standards in the construction of networks. ...
File - Learning@NDGTA
... • Layer 5 provides the protocols that can be used to set up a call between specific individuals – eg like brining someone in an office over to answer the phone call • Layer 6 resolves the problem of language so that both caller and receiver are speaking the same language • Layer 7 gives the procedur ...
... • Layer 5 provides the protocols that can be used to set up a call between specific individuals – eg like brining someone in an office over to answer the phone call • Layer 6 resolves the problem of language so that both caller and receiver are speaking the same language • Layer 7 gives the procedur ...
First Deep Space Node on the Interplanetary Internet: the Deep
... • Clock synchronization and OWLT estimation errors of several seconds had no noticeable effect on network operation. ...
... • Clock synchronization and OWLT estimation errors of several seconds had no noticeable effect on network operation. ...
Network Auditing - Personal Web Pages
... If any ARP packets are received with same sender IP address, there is a conflict requests or responses ...
... If any ARP packets are received with same sender IP address, there is a conflict requests or responses ...
ch1_INTRO_0708
... Why layering ? Dealing with complex systems: explicit structure allows identification of functions, ...
... Why layering ? Dealing with complex systems: explicit structure allows identification of functions, ...
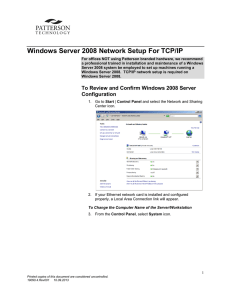
Windows Server 2008 Network Setup For TCP/IP
... 8. Select OK. You will be prompted to restart your computer. 9. Once you have restarted your computer, you can check your network connection by going to Network and Sharing Center and opening up the network. Any and all other computers in the same workgroup will be listed. ...
... 8. Select OK. You will be prompted to restart your computer. 9. Once you have restarted your computer, you can check your network connection by going to Network and Sharing Center and opening up the network. Any and all other computers in the same workgroup will be listed. ...
Powerpoint
... • Original spec said transport layer would set • Usually set to value of variable in IP layer that is incremented by one for each datagram sent from that host (regardless of destination) • Would wrap every 65535 datagrams ...
... • Original spec said transport layer would set • Usually set to value of variable in IP layer that is incremented by one for each datagram sent from that host (regardless of destination) • Would wrap every 65535 datagrams ...
HHS - Complete Table of Contents and Glossary
... Internet, analogous to a telephone conversation but using text-based, not voice-based, communication. interfaces – A boundary across which two independent systems meet and act on or communicate with each other. Internet Assigned Numbers Authority (IANA) – An organization working under the auspices o ...
... Internet, analogous to a telephone conversation but using text-based, not voice-based, communication. interfaces – A boundary across which two independent systems meet and act on or communicate with each other. Internet Assigned Numbers Authority (IANA) – An organization working under the auspices o ...
Internet protocol suite

The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP, because among many protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) is the accepted and most widely used protocol in Internet. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. This functionality is organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link); the internet layer, connecting hosts across independent networks, thus establishing internetworking; the transport layer handling host-to-host communication; and the application layer, which provides process-to-process application data exchange.The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF).