
Employing EM and Pool-Based Active Learning for Text Classification
... other ty pes of printers . ...
... other ty pes of printers . ...
Configuration of Universal Plug and Play (UPnP) on RV320 and RV325
... Universal Plug and Play (UPnP) is a set of networking protocols that allow devices to discover each other on the network. The discovered devices can establish network services for data sharing, communications, and entertainment. UPnP can be used to set up public services on your network. When the UP ...
... Universal Plug and Play (UPnP) is a set of networking protocols that allow devices to discover each other on the network. The discovered devices can establish network services for data sharing, communications, and entertainment. UPnP can be used to set up public services on your network. When the UP ...
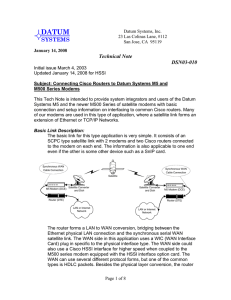
Tech Note - Datum Systems
... The modem clock settings are the default and simplest form of clocking. The Modem as DCE device supplies both the Send and Receive Timing signals to the router. Thus the Modulator Clock Source is set to "Internal" and the Demodulator Clock source is set to "Demod". This makes each link direction ind ...
... The modem clock settings are the default and simplest form of clocking. The Modem as DCE device supplies both the Send and Receive Timing signals to the router. Thus the Modulator Clock Source is set to "Internal" and the Demodulator Clock source is set to "Demod". This makes each link direction ind ...
3rd Edition: Chapter 3
... source IP address source port number dest IP address dest port number ...
... source IP address source port number dest IP address dest port number ...
Slide 1
... A network administrator manually enters route into the router's configuration When network only consists of a few routers -Network is connected to internet only through one ISP route entry manually updated whenever network topology changes Static routing reduces overhead Better security ...
... A network administrator manually enters route into the router's configuration When network only consists of a few routers -Network is connected to internet only through one ISP route entry manually updated whenever network topology changes Static routing reduces overhead Better security ...
Télécharger le fichier - Fichier
... Refer to the exhibit. A host is connected to hub 1. Which combination of IP address, subnet mask, and default gateway can allow th host to function in the network? IP address: 172.16.31.36 Subnet mask: 255.255.255.240 Default gateway: 172.16.31.35 IP address: 172.16.31.63 Subnet mask: 255.255.255.22 ...
... Refer to the exhibit. A host is connected to hub 1. Which combination of IP address, subnet mask, and default gateway can allow th host to function in the network? IP address: 172.16.31.36 Subnet mask: 255.255.255.240 Default gateway: 172.16.31.35 IP address: 172.16.31.63 Subnet mask: 255.255.255.22 ...
Defense in Depth / Firewalls Presentation
... First / last router under control of system administration. Demilitarized zone. Security is low, since not protected by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
... First / last router under control of system administration. Demilitarized zone. Security is low, since not protected by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
GigaVUE-420 // Data Sheet
... • Redundant hot-swappable load-sharing AC and DC power supplies, dual cooling fans for investment protection ...
... • Redundant hot-swappable load-sharing AC and DC power supplies, dual cooling fans for investment protection ...
Lecture 20: Transport layer
... – potential problem: may do the same thing two times, which can decrease the communication performance. ...
... – potential problem: may do the same thing two times, which can decrease the communication performance. ...
Computer Networking Devices Explained with Function DOCX Format
... the wire and found no signals, and each device places it’s signal on the wire. These signals would be collide in wire and a collision will occur. Before placing any signal in wire, NIC (Network Interface Card) examines wire for any existing signal. This method is known as CS (Carrier Sense). If two ...
... the wire and found no signals, and each device places it’s signal on the wire. These signals would be collide in wire and a collision will occur. Before placing any signal in wire, NIC (Network Interface Card) examines wire for any existing signal. This method is known as CS (Carrier Sense). If two ...
Emulab`s Current Support For IXPs
... other special hardware • Intel's network processors • StrongARM chip that runs Linux • Hosted as a PCI card in a PC • Serial line for control – We attach it to the host PC ...
... other special hardware • Intel's network processors • StrongARM chip that runs Linux • Hosted as a PCI card in a PC • Serial line for control – We attach it to the host PC ...
[] Distributed Architectures for Medical Systems
... What’s the Big Deal? Creating an IDL and the associated client/server code for the Polaris Tracker would prove the viability of replacing dedicated workstations with smaller and cheaper TINI boards. Using a JAVA implementation of the CORBA ORB and client/server functions would provide a strong impe ...
... What’s the Big Deal? Creating an IDL and the associated client/server code for the Polaris Tracker would prove the viability of replacing dedicated workstations with smaller and cheaper TINI boards. Using a JAVA implementation of the CORBA ORB and client/server functions would provide a strong impe ...
Sort-first
... We will call primitives that result from tessellation display primitives. If T is the tessellation ratio, there are nd = Tnr of these, with average size ad = ar /T. If there is no tessellation, T = 1, nd = nr , and ad = ar . Assume an image containing A pixels and need to compute S samples per pixel ...
... We will call primitives that result from tessellation display primitives. If T is the tessellation ratio, there are nd = Tnr of these, with average size ad = ar /T. If there is no tessellation, T = 1, nd = nr , and ad = ar . Assume an image containing A pixels and need to compute S samples per pixel ...
The Announcement Layer: Beacon Coordination for
... implemented as an overlay network. – Nodes primarily use structured overlay network (SON) IDs as network endpoints. ...
... implemented as an overlay network. – Nodes primarily use structured overlay network (SON) IDs as network endpoints. ...
Basics of TCP/IP, Switching, Routing and Firewalling. Why this article ?
... The ability that your computer can run at OSI-layer 4 using TCP/IP makes it possible to use this device to run a firewall on it. Most of you will have at least one firewall running on the computer when having installed Windows XP SP2. This firewall is active by default and could be a possible cause ...
... The ability that your computer can run at OSI-layer 4 using TCP/IP makes it possible to use this device to run a firewall on it. Most of you will have at least one firewall running on the computer when having installed Windows XP SP2. This firewall is active by default and could be a possible cause ...
Title
... Load automatically distributed across scalable DirectorBlade modules Scale to satisfy growing number of clients Any DirectorBlade module can access any file Slide in a new DB, instantly get more NFS ops/sec into the same data ...
... Load automatically distributed across scalable DirectorBlade modules Scale to satisfy growing number of clients Any DirectorBlade module can access any file Slide in a new DB, instantly get more NFS ops/sec into the same data ...
Review For Final - Eastern Illinois University
... Yes, you can (e.g. Digital Video Service or DVS). Noise used to be a limiting factor. ...
... Yes, you can (e.g. Digital Video Service or DVS). Noise used to be a limiting factor. ...
Review For Final - Eastern Illinois University
... Yes, you can (e.g. Digital Video Service or DVS). Noise used to be a limiting factor. ...
... Yes, you can (e.g. Digital Video Service or DVS). Noise used to be a limiting factor. ...
Intrusion detection systems
... A packet sniffer allows for the examination of any or all of the traffic passing through a network cable or wireless space ...
... A packet sniffer allows for the examination of any or all of the traffic passing through a network cable or wireless space ...
SX6506 - Mellanox Technologies
... Scaling-Out Data Centers with Fourteen Data Rate (FDR) InfiniBand Faster servers based on PCIe 3.0 combined with high-performance storage and applications that use increasingly complex computations, are causing data bandwidth requirements to spiral upward. As servers are deployed with next generatio ...
... Scaling-Out Data Centers with Fourteen Data Rate (FDR) InfiniBand Faster servers based on PCIe 3.0 combined with high-performance storage and applications that use increasingly complex computations, are causing data bandwidth requirements to spiral upward. As servers are deployed with next generatio ...
sudo mn --topo single,4 --mac --switch ovsk -
... • Start controller and check OF messages on wireshark (enabling OFP decode) – Openflow messages exchanged between switch and controller: openflow/include/openflow/openflow.h /* Header on all OpenFlow packets. */ struct ofp_header { uint8_t version; /* OFP_VERSION. */ uint8_t type; /* one of the OFPT ...
... • Start controller and check OF messages on wireshark (enabling OFP decode) – Openflow messages exchanged between switch and controller: openflow/include/openflow/openflow.h /* Header on all OpenFlow packets. */ struct ofp_header { uint8_t version; /* OFP_VERSION. */ uint8_t type; /* one of the OFPT ...
XLesson 4 - Multiplexing UDP
... segments may be: lost delivered out of order to app connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
... segments may be: lost delivered out of order to app connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
Security
... capacity of a network by sending more information requests than it can handle-a classic denial of service. Sending a large amount of requests to a single port is Flooding. When the requests are sent to all network stations, it's called broadcasting. Attackers will often use flood attacks to gain ...
... capacity of a network by sending more information requests than it can handle-a classic denial of service. Sending a large amount of requests to a single port is Flooding. When the requests are sent to all network stations, it's called broadcasting. Attackers will often use flood attacks to gain ...
Parallel port

A parallel port is a type of interface found on computers (personal and otherwise) for connecting peripherals. In computing, a parallel port is a parallel communication physical interface. It is also known as a printer port or Centronics port. It was an industry de facto standard for many years, and was finally standardized as IEEE 1284 in the late 1990s, which defined the Enhanced Parallel Port (EPP) and Extended Capability Port (ECP) bi-directional versions. Today, the parallel port interface is seeing decreasing use because of the rise of Universal Serial Bus (USB) devices, along with network printing using Ethernet.The parallel port interface was originally known as the Parallel Printer Adapter on IBM PC-compatible computers. It was primarily designed to operate a line printer that used IBM's 8-bit extended ASCII character set to print text, but could also be used to adapt other peripherals. Graphical printers, along with a host of other devices, have been designed to communicate with the system.










![[] Distributed Architectures for Medical Systems](http://s1.studyres.com/store/data/008584341_1-44a2410e4fe4804aaa9c92ca6e1df529-300x300.png)











