ETERNITY Technical Specifications
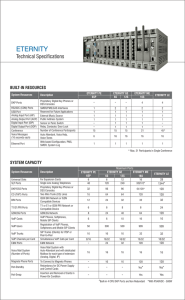
... Feature Rich Digital Key Phone; 6x24 LCD with Swivel, Backlit and Contrast Control, 17 Touch Sense and 16 Programmable Keys ...
... Feature Rich Digital Key Phone; 6x24 LCD with Swivel, Backlit and Contrast Control, 17 Touch Sense and 16 Programmable Keys ...
virtio-vsock - Stefan Hajnoczi
... Sockets API – standard for communication The familiar Berkeley/POSIX sockets API: ...
... Sockets API – standard for communication The familiar Berkeley/POSIX sockets API: ...
CAS: Central Authentication Service
... service=url-where-user-will-log-in! • CAS sends user back to the service url to log in with a parameter ticket=hash-of-something! • your login code sends this back to ...
... service=url-where-user-will-log-in! • CAS sends user back to the service url to log in with a parameter ticket=hash-of-something! • your login code sends this back to ...
Examining port scan methods - Analysing Audible
... instantaneous identification of an open or closed port. If the connect() call returns true, the port is open, else the port is closed. Since this technique issues a three-way handshake to connect to an arbitrary host, a spoofed connection is impossible, that is to say a client can not manipulate the ...
... instantaneous identification of an open or closed port. If the connect() call returns true, the port is open, else the port is closed. Since this technique issues a three-way handshake to connect to an arbitrary host, a spoofed connection is impossible, that is to say a client can not manipulate the ...
jgunders_Sem_2v2_Ch_9_FTP
... the different conversations that cross the network at the same time. Application software developers have agreed to use the well-known port numbers that are defined in RFC 1700. For example, any conversation bound for an FTP application uses the standard port number 21. Conversations that do not inv ...
... the different conversations that cross the network at the same time. Application software developers have agreed to use the well-known port numbers that are defined in RFC 1700. For example, any conversation bound for an FTP application uses the standard port number 21. Conversations that do not inv ...
LINUX System (English
... Clients can envision the structure and the functionality in the finished system Developers have a structure to work toward Technical writers who have to provide documentation and help files can understand what they’re writing about Your are ready for reuse ...
... Clients can envision the structure and the functionality in the finished system Developers have a structure to work toward Technical writers who have to provide documentation and help files can understand what they’re writing about Your are ready for reuse ...
Case Study: Infiniband
... • Each QP has a send queue and a receive queue. • Users can post send requests to the send queue and receive requests to the receive queue. • Three types of send operations: SEND, RDMA(WRITE, READ, ATOMIC), MEMORY-BINDING • One receive operation (matching SEND) ...
... • Each QP has a send queue and a receive queue. • Users can post send requests to the send queue and receive requests to the receive queue. • Three types of send operations: SEND, RDMA(WRITE, READ, ATOMIC), MEMORY-BINDING • One receive operation (matching SEND) ...
Middleboxes
and
Tunneling
Reading:
Sect
8.5,
9.4.1,
4.5
COS
461:
Computer
Networks
Spring
2011
... VPN A / Site 2 VPN B / Site 1 ...
... VPN A / Site 2 VPN B / Site 1 ...
CS 105 - HMC Computer Science
... Fact: Al Gore introduced and supported many bills funding the shift from a primarily US research network to a worldwide commercial one Farber: “The guy used an inappropriate word. If he had said he was instrumental in the development of what it is now, he'd be accurate.” ...
... Fact: Al Gore introduced and supported many bills funding the shift from a primarily US research network to a worldwide commercial one Farber: “The guy used an inappropriate word. If he had said he was instrumental in the development of what it is now, he'd be accurate.” ...
Cisco Discovery 1 Module 05 Quiz Picture Descriptions
... if a bit is a zero (0), its column value is not counted. The value of each bit in an octet is twice that of the bit to its right. The rightmost bit in an octet has a value of 0 when it is turned on. A host looks at every bit of an IP address as it is received by the host NIC. If all of the bits in a ...
... if a bit is a zero (0), its column value is not counted. The value of each bit in an octet is twice that of the bit to its right. The rightmost bit in an octet has a value of 0 when it is turned on. A host looks at every bit of an IP address as it is received by the host NIC. If all of the bits in a ...
SCORE: A Scalable Architecture for Implementing Resource
... • Resolution of name need not point to object itself, but can point to its delegate – Resolution can point to intermediaries who process packets on behalf of the named target ...
... • Resolution of name need not point to object itself, but can point to its delegate – Resolution can point to intermediaries who process packets on behalf of the named target ...
Internetworking - HMC Computer Science
... Fact: Al Gore introduced and supported many bills funding the shift from a primarily US research network to a worldwide commercial one Farber: “The guy used an inappropriate word. If he had said he was instrumental in the development of what it is now, he'd be accurate.” ...
... Fact: Al Gore introduced and supported many bills funding the shift from a primarily US research network to a worldwide commercial one Farber: “The guy used an inappropriate word. If he had said he was instrumental in the development of what it is now, he'd be accurate.” ...
HRG Series DVR Helpful Network Setup Tips
... © 2012 Honeywell International Inc. All rights reserved. No part of this publication may be reproduced by any means without written permission from Honeywell. The information in this publication is believed to be accurate in all respects. However, Honeywell cannot assume responsibility for any conse ...
... © 2012 Honeywell International Inc. All rights reserved. No part of this publication may be reproduced by any means without written permission from Honeywell. The information in this publication is believed to be accurate in all respects. However, Honeywell cannot assume responsibility for any conse ...
Lotus and Cognos Business Lotus and Cognos Business
... © Copyright IBM Corporation 2008 All rights reserved. The information contained in these materials is provided for informational purposes only, and is provided AS IS without warranty of any kind, express or implied. IBM shall not be responsible for any damages arising out of the use of, or otherwis ...
... © Copyright IBM Corporation 2008 All rights reserved. The information contained in these materials is provided for informational purposes only, and is provided AS IS without warranty of any kind, express or implied. IBM shall not be responsible for any damages arising out of the use of, or otherwis ...
access control list
... A. You should place standard ACLS as close as possible to the source of traffic to be denied. B. You should place extended ACLS as close as possible to the source of traffic to be denied. C. You should place standard ACLS as close as possible to the destination of traffic to be denied. D. You should ...
... A. You should place standard ACLS as close as possible to the source of traffic to be denied. B. You should place extended ACLS as close as possible to the source of traffic to be denied. C. You should place standard ACLS as close as possible to the destination of traffic to be denied. D. You should ...
Computer Network Unit-V
... Checksum: An optional 16-bit checksum computed over the entire UDP datagram plus a special “pseudo header” of fields. See below for more information. ...
... Checksum: An optional 16-bit checksum computed over the entire UDP datagram plus a special “pseudo header” of fields. See below for more information. ...
ppt
... • Customer needs to be reachable from everyone – Provider tells all neighbors how to reach the customer ...
... • Customer needs to be reachable from everyone – Provider tells all neighbors how to reach the customer ...
Spanning Tree Protocol
... root bridge in terms of path cost – The root bridge sends BPDUs that are more useful than the ones that any other bridge can send. – The root bridge is the only bridge in the network that does not have a root port. ...
... root bridge in terms of path cost – The root bridge sends BPDUs that are more useful than the ones that any other bridge can send. – The root bridge is the only bridge in the network that does not have a root port. ...
COS 461: Computer Networks Course Review (12 weeks in 80 minutes)
... – MulVple instances of a service share same IP address – Each instance announces IP address / prefix in BGP / IGP – RouVng infrastructure directs packets to nearest instance of the service • Can use same selecVon criteria as installing routes in the FIB ...
... – MulVple instances of a service share same IP address – Each instance announces IP address / prefix in BGP / IGP – RouVng infrastructure directs packets to nearest instance of the service • Can use same selecVon criteria as installing routes in the FIB ...
571Lecture7
... Per-Packet Processing in IP Routers 1. Accept packet arriving on an incoming link. 2. Lookup packet destination address in the forwarding table, to identify outgoing port(s). 3. Manipulate packet header: e.g., update header checksum. 4. Send packet to the outgoing port(s). 5. Classify and buffer pa ...
... Per-Packet Processing in IP Routers 1. Accept packet arriving on an incoming link. 2. Lookup packet destination address in the forwarding table, to identify outgoing port(s). 3. Manipulate packet header: e.g., update header checksum. 4. Send packet to the outgoing port(s). 5. Classify and buffer pa ...
Internet Programming - Seneca
... This sends discrete messages rather than a stream of bytes Each message can be sent to a different computer UDP is much more efficient than TCP/IP UDP is used for sending audio and video ...
... This sends discrete messages rather than a stream of bytes Each message can be sent to a different computer UDP is much more efficient than TCP/IP UDP is used for sending audio and video ...
Parallel port

A parallel port is a type of interface found on computers (personal and otherwise) for connecting peripherals. In computing, a parallel port is a parallel communication physical interface. It is also known as a printer port or Centronics port. It was an industry de facto standard for many years, and was finally standardized as IEEE 1284 in the late 1990s, which defined the Enhanced Parallel Port (EPP) and Extended Capability Port (ECP) bi-directional versions. Today, the parallel port interface is seeing decreasing use because of the rise of Universal Serial Bus (USB) devices, along with network printing using Ethernet.The parallel port interface was originally known as the Parallel Printer Adapter on IBM PC-compatible computers. It was primarily designed to operate a line printer that used IBM's 8-bit extended ASCII character set to print text, but could also be used to adapt other peripherals. Graphical printers, along with a host of other devices, have been designed to communicate with the system.























