Information Security in the New Millennium
... Those measures, procedures, or controls which provide an ...
... Those measures, procedures, or controls which provide an ...
Web tracking resolution
... Web tracking allows organisations to monitor almost every single aspect of user behaviour on the Web. The type of information that can be collected through tracking (e.g., IP addresses, device identi?iers, etc.) can lead to the identi?ication of a particular ...
... Web tracking allows organisations to monitor almost every single aspect of user behaviour on the Web. The type of information that can be collected through tracking (e.g., IP addresses, device identi?iers, etc.) can lead to the identi?ication of a particular ...
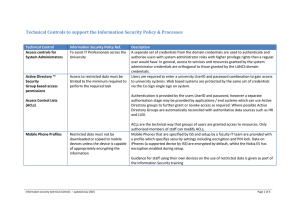
Technical Controls to support the Information
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
Victims who were Hacked PowerPoint Presentation
... Privacy and Security Issues Privacy and Security Issues related to Information and Communication Technology ...
... Privacy and Security Issues Privacy and Security Issues related to Information and Communication Technology ...
Crypto in data security
... • Planning the continuation of trade and reviews of electronic crimes, etc. ...
... • Planning the continuation of trade and reviews of electronic crimes, etc. ...
IEEE CONFERENCE ON COMMUNICATION TECHNOLOGIES
... Military College of Signals (MCS), a Campus of National University of Sciences and Technology (NUST), Pakistan, is dedicated to advancing knowledge and educating students in science and technology. As part of its continuing pursuit for excellence in the domains of Telecommunications, Information Sec ...
... Military College of Signals (MCS), a Campus of National University of Sciences and Technology (NUST), Pakistan, is dedicated to advancing knowledge and educating students in science and technology. As part of its continuing pursuit for excellence in the domains of Telecommunications, Information Sec ...
The Information Security Jigsaw The Technical Elements
... • There are solutions but not panaceas • You can only defend against that which you know • Technical security is not enough on its own • The future is uncertain - we can only do our best but it must be the best! ...
... • There are solutions but not panaceas • You can only defend against that which you know • Technical security is not enough on its own • The future is uncertain - we can only do our best but it must be the best! ...
Enter Title in Docm Properties
... This includes system design, code development, documentation, unit-tests, code-reviews, and bug-fixes. Depending on your skill level, this will evolve into leading a team to develop new product modules for the Tofino Industrial Security Solution product line. You should be a good team player that wo ...
... This includes system design, code development, documentation, unit-tests, code-reviews, and bug-fixes. Depending on your skill level, this will evolve into leading a team to develop new product modules for the Tofino Industrial Security Solution product line. You should be a good team player that wo ...
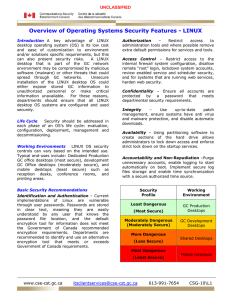
Overview of Operating Systems Security Features
... and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the GC network environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could ...
... and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the GC network environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could ...
Online dating Virtual gaming Twitter LinkedIn Facebook Google +
... THE RAPID EVOLUTION OF INFORMATION TECHNOLOGY • “The sharing of information, using technology as an enabler, is a culture change that has been fully embraced by political, military, and the business communities.” • “If we do not develop robust capabilities to detect, expose, and hold accountable ...
... THE RAPID EVOLUTION OF INFORMATION TECHNOLOGY • “The sharing of information, using technology as an enabler, is a culture change that has been fully embraced by political, military, and the business communities.” • “If we do not develop robust capabilities to detect, expose, and hold accountable ...
Management Information Systems Undergraduate Study Iowa State University – 2015-2016
... of the 48 credits are core business courses and the remaining 18 credits are graduate electives. Students may obtain a specialization in technology and innovation management within the M.B.A. program. The M.S.I.S. is a 30-credit (minimum) curriculum designed around three interrelated areas – busines ...
... of the 48 credits are core business courses and the remaining 18 credits are graduate electives. Students may obtain a specialization in technology and innovation management within the M.B.A. program. The M.S.I.S. is a 30-credit (minimum) curriculum designed around three interrelated areas – busines ...
The Role of Security in an Introductory Course
... • Depends • 2 or 4 year school • Course of study ...
... • Depends • 2 or 4 year school • Course of study ...
PPT
... but linkability • If I can link multiple queries, I might be able to infer the identity of the person issuing the query through one query, at which point, all anonymity is lost ...
... but linkability • If I can link multiple queries, I might be able to infer the identity of the person issuing the query through one query, at which point, all anonymity is lost ...
50 Word Company Description 100 Word
... solutions to protect your sensitive data from loss, theft and abuse whether it rests within, or is transmitted outside, of your organization. Over 2000 companies worldwide trust us to secure their most valuable information while we provide them with assurance their data is secured to the highest lev ...
... solutions to protect your sensitive data from loss, theft and abuse whether it rests within, or is transmitted outside, of your organization. Over 2000 companies worldwide trust us to secure their most valuable information while we provide them with assurance their data is secured to the highest lev ...
Information Systems and Business Intelligence
... This module will give students the opportunity to understand the nature of information and business intelligence, the global role of information systems within organizations and, in particular, how they relate to the IS Strategy and the overall corporate strategy. It is intended to equip students to ...
... This module will give students the opportunity to understand the nature of information and business intelligence, the global role of information systems within organizations and, in particular, how they relate to the IS Strategy and the overall corporate strategy. It is intended to equip students to ...
Proposed Part 73 Fuel Cycle Facility Security Rulemaking
... • 10 CFR Part 73, Physical Protection of Plants and Materials, has been revised subpart-by-subpart over the last 25 years • Lessons learned ((e.g., g threat and implementation)) • Commission directed engagement of a “broad” range of stakeholders ...
... • 10 CFR Part 73, Physical Protection of Plants and Materials, has been revised subpart-by-subpart over the last 25 years • Lessons learned ((e.g., g threat and implementation)) • Commission directed engagement of a “broad” range of stakeholders ...
Security Requirements
... not been altered. “The tribunal in Fiji could not prove the integrity of an email message claimed to be originated from a government employee which stated that one of Fiji’s former Finance Minister ( Mr. Ah Koy) was one of the people behind the Fiji coup in 2000.” ...
... not been altered. “The tribunal in Fiji could not prove the integrity of an email message claimed to be originated from a government employee which stated that one of Fiji’s former Finance Minister ( Mr. Ah Koy) was one of the people behind the Fiji coup in 2000.” ...
Computer Security: Principles and Practice, 1/e
... order to attain the applicable objectives of preserving the integrity, availability and confidentiality of information system resources (includes hardware, software, firmware, information/data, and telecommunications). • 3 - Passive attacks have to do with eavesdropping on, or monitoring, transmissi ...
... order to attain the applicable objectives of preserving the integrity, availability and confidentiality of information system resources (includes hardware, software, firmware, information/data, and telecommunications). • 3 - Passive attacks have to do with eavesdropping on, or monitoring, transmissi ...
Importance of Information Management in Human Services
... How do we engage in advocacy and public awareness of societal issues? Gathering information (information literacy) ◦ Research ◦ Data mining ...
... How do we engage in advocacy and public awareness of societal issues? Gathering information (information literacy) ◦ Research ◦ Data mining ...
Chapter 1: Security Problems in Computing
... good guys come”. In the arena of physical security, nothing can be absolutely protected. The only answer is to make a successful attack costly and time-consuming. We often apply the same idea to the protection of computer and information assets”. The Great Diamond Heist This is a true story dating f ...
... good guys come”. In the arena of physical security, nothing can be absolutely protected. The only answer is to make a successful attack costly and time-consuming. We often apply the same idea to the protection of computer and information assets”. The Great Diamond Heist This is a true story dating f ...
Estimation Schemes Based on Distributed Observations
... In the second part of the talk, I will consider information transmission and maximum likelihood estimation in a GLM network as a simplified model for the spiking activity of a neural population. It turns out that for large neural populations carrying a finite total amount of information, the asympto ...
... In the second part of the talk, I will consider information transmission and maximum likelihood estimation in a GLM network as a simplified model for the spiking activity of a neural population. It turns out that for large neural populations carrying a finite total amount of information, the asympto ...
Security - UTRGV Faculty Web
... anyone with a public key. But the message was sent by only one who has the private key. Digital certificates are used to authenticate the source of a file. ...
... anyone with a public key. But the message was sent by only one who has the private key. Digital certificates are used to authenticate the source of a file. ...
Course Schedule
... 133b F. Roosevelt & Omonoia Ave 3011, Limassol, Cyprus Tel. +357 25029300, Fax: +357 25029301 ...
... 133b F. Roosevelt & Omonoia Ave 3011, Limassol, Cyprus Tel. +357 25029300, Fax: +357 25029301 ...