Application Service Provider Security Requirements
... Protected data are any information that the University has deemed to be confidential or sensitive in nature and therefore require additional safeguards in its handling and use. This includes information protected by law such as social security number or credit card numbers. Also included is informat ...
... Protected data are any information that the University has deemed to be confidential or sensitive in nature and therefore require additional safeguards in its handling and use. This includes information protected by law such as social security number or credit card numbers. Also included is informat ...
Information Security in Real Business
... Configured Software is Downloaded from Ford Installed on Cars for Diagnostic Testing ...
... Configured Software is Downloaded from Ford Installed on Cars for Diagnostic Testing ...
Chapter 1: Introduction to security
... Security services/ characteristics • Information security services traditionally focused on confidentiality, integrity and authentication, but over the years the list has expanded to: ...
... Security services/ characteristics • Information security services traditionally focused on confidentiality, integrity and authentication, but over the years the list has expanded to: ...
Appendix *J* - Credit Plus
... ECOA, the credit reporting agency requires that you retain the credit application and, if applicable, a purchase agreement for a period of not less than 25 months. When conducting an investigation, particularly following a breach or a consumer complaint that your company impermissibly accessed their ...
... ECOA, the credit reporting agency requires that you retain the credit application and, if applicable, a purchase agreement for a period of not less than 25 months. When conducting an investigation, particularly following a breach or a consumer complaint that your company impermissibly accessed their ...
Principal Security Engineer– PAE4IT A. PRIMARY ROLE Working
... technology projects, and provides reports and recommendations on appropriate tactical and strategic security actions. Has expertise and provides input that could have a direct impact on important technology decisions made at the highest levels of the university. Participates in and leads computer em ...
... technology projects, and provides reports and recommendations on appropriate tactical and strategic security actions. Has expertise and provides input that could have a direct impact on important technology decisions made at the highest levels of the university. Participates in and leads computer em ...
"O brave new world, that has such people in`t
... Center for Business, Law, and Public Policy, recently addressed "Cyber Threats and Cyber Security." What they said was both terrifying--by some accounts international businesses are losing more than $1 trillion a year to digital crimes--and oddly reassuring--diligent organizations can pull from an a ...
... Center for Business, Law, and Public Policy, recently addressed "Cyber Threats and Cyber Security." What they said was both terrifying--by some accounts international businesses are losing more than $1 trillion a year to digital crimes--and oddly reassuring--diligent organizations can pull from an a ...
Fundamentals of Computer Security
... Active entities that access objects Passive entities that must be protected Examples: data, hardware, software and communication links ...
... Active entities that access objects Passive entities that must be protected Examples: data, hardware, software and communication links ...
D1S1_TSV404_Course_Intro_2011_v1
... right along with other project RM ■ Most RM that takes place was for compliance rather than as a tool to help secure the system ■ The Risk Assessments done now are of low quality and value – needs to correspond to impact level ■ RM must be part of the overall project plan for the application/archite ...
... right along with other project RM ■ Most RM that takes place was for compliance rather than as a tool to help secure the system ■ The Risk Assessments done now are of low quality and value – needs to correspond to impact level ■ RM must be part of the overall project plan for the application/archite ...
Applied Cybersecurity
... best protect their enterprises. In this course, experts from academia, the military, and industry share their knowledge to give participants the principles, the state of the practice, and strategies for the future. Sessions will address information security, ethical and legal practices, and mitigati ...
... best protect their enterprises. In this course, experts from academia, the military, and industry share their knowledge to give participants the principles, the state of the practice, and strategies for the future. Sessions will address information security, ethical and legal practices, and mitigati ...
Physician Office Staff Security Access Form Office Staff Information
... may log, access, review, and otherwise utilize information stored on or passing through its systems, including email, in order to manage systems and enforce security. I understand that violation of this Agreement may result in disciplinary action, up to and including termination of employment, suspe ...
... may log, access, review, and otherwise utilize information stored on or passing through its systems, including email, in order to manage systems and enforce security. I understand that violation of this Agreement may result in disciplinary action, up to and including termination of employment, suspe ...
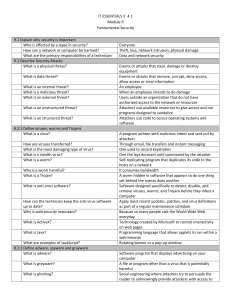
IT ESSENTIALS V. 4.1 Module 9 Fundamental Security 9.1 Explain
... personal information Monitors activity on the computer and sends this information to the organization responsible for launching the spyware A form of attack that prevents users from accessing normal services because the system is busy responding to abnormally large amounts of requests Ping of death; ...
... personal information Monitors activity on the computer and sends this information to the organization responsible for launching the spyware A form of attack that prevents users from accessing normal services because the system is busy responding to abnormally large amounts of requests Ping of death; ...
10 Tips for Website Safety
... 4. Do not use your web space for generic file storage. Private network file shares are available at no cost to faculty for network storage and backups of files that should not be publicly accessible. Department/group shares are also available for files that need to be shared between members of a tea ...
... 4. Do not use your web space for generic file storage. Private network file shares are available at no cost to faculty for network storage and backups of files that should not be publicly accessible. Department/group shares are also available for files that need to be shared between members of a tea ...
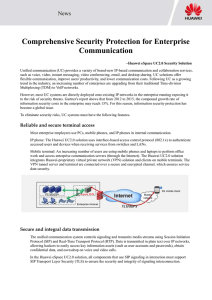
Comprehensive Security Protection for
... However, most UC systems are directly deployed onto existing IP networks in the enterprise running exposing it to the risk of security threats. Gartner's report shows that from 2012 to 2015, the compound growth rate of information security costs in the enterprise may reach 15%. For this reason, info ...
... However, most UC systems are directly deployed onto existing IP networks in the enterprise running exposing it to the risk of security threats. Gartner's report shows that from 2012 to 2015, the compound growth rate of information security costs in the enterprise may reach 15%. For this reason, info ...
KESB Advanced Presentation
... TODAY, BUSINESSES PROCESS AND STORE MASSIVE VOLUMES OF INFORMATION, INCLUDING: ...
... TODAY, BUSINESSES PROCESS AND STORE MASSIVE VOLUMES OF INFORMATION, INCLUDING: ...
file - ScholarSphere
... external intruders, and from both intentional or accidental disclosure or destruction? While network administrators take great pains to protect their networks from intruders from the outside, they frequently ignore or are unaware of the advantages possessed by intruders on the inside: Insiders have ...
... external intruders, and from both intentional or accidental disclosure or destruction? While network administrators take great pains to protect their networks from intruders from the outside, they frequently ignore or are unaware of the advantages possessed by intruders on the inside: Insiders have ...
HIPAA Security Standards
... There are several types of firewall techniques: • Packet filter: Looks at each packet entering or leaving the network and accepts or rejects it based on user-defined rules. Packet filtering is fairly effective and transparent to users, but it is difficult to configure. In addition, it is susceptible ...
... There are several types of firewall techniques: • Packet filter: Looks at each packet entering or leaving the network and accepts or rejects it based on user-defined rules. Packet filtering is fairly effective and transparent to users, but it is difficult to configure. In addition, it is susceptible ...
Why Cryptography is Harder Than It Looks
... prevented • Targeted attacks can only be withstood up to a point • The problems with cryptography are not in the algorithms and protocols, but the implementation – Weakness are found at human interaction level ...
... prevented • Targeted attacks can only be withstood up to a point • The problems with cryptography are not in the algorithms and protocols, but the implementation – Weakness are found at human interaction level ...
Phoenix SIEM (Security Information and Event
... Director and CTO at Kenindus Limited . Holds a Bachelor of Science degree in Computer Information Management from Life University in Atlanta, Georgia and a Masters in Small Business and Entrepreneurship from Plymouth State in Plymouth, New Hampshire. I have more than 10 years experience in cyber sec ...
... Director and CTO at Kenindus Limited . Holds a Bachelor of Science degree in Computer Information Management from Life University in Atlanta, Georgia and a Masters in Small Business and Entrepreneurship from Plymouth State in Plymouth, New Hampshire. I have more than 10 years experience in cyber sec ...
Privacy Legislation Update $1.7 Million Civil Penalty for a
... IPSec are specialists in information asset security; technology experts who know how to mitigate risk to business by implementing end-to-end solutions that protect invaluable intelligence, data and information. Their capabilities extend from assessing vulnerabilities and threats, to designing and im ...
... IPSec are specialists in information asset security; technology experts who know how to mitigate risk to business by implementing end-to-end solutions that protect invaluable intelligence, data and information. Their capabilities extend from assessing vulnerabilities and threats, to designing and im ...
Phishing Scams - Corner Stone Credit Union
... Online fraud takes many forms, but fraud scams known as phishing remain most prevalent. Phishing scams most often utilize emails or automated phone calls in an attempt to prompt a consumer into providing personal or account information that is then used by the perpetrators to commit fraud. The term ...
... Online fraud takes many forms, but fraud scams known as phishing remain most prevalent. Phishing scams most often utilize emails or automated phone calls in an attempt to prompt a consumer into providing personal or account information that is then used by the perpetrators to commit fraud. The term ...