Database System Implementation Proposal
... TCP/IP is based on a four-layer reference model. All protocols that belong to the TCP/IP protocol suite are located in the top three layers of this model. ...
... TCP/IP is based on a four-layer reference model. All protocols that belong to the TCP/IP protocol suite are located in the top three layers of this model. ...
Lesson 11
... Corresponds to datagram mechanism in packet switched network Each NPDU treated separately Network layer protocol common to all ESs and routers Known generically as the internet protocol ...
... Corresponds to datagram mechanism in packet switched network Each NPDU treated separately Network layer protocol common to all ESs and routers Known generically as the internet protocol ...
Chapter 1 - William Stallings, Data and Computer Communications
... • simulating the effects of a sudden burst in traffic • a DoS attack on a network service • test new networking protocols or changes to existing protocols in a controlled and reproducible environment • With the help of simulators one can design hierarchical networks using various types of nodes like ...
... • simulating the effects of a sudden burst in traffic • a DoS attack on a network service • test new networking protocols or changes to existing protocols in a controlled and reproducible environment • With the help of simulators one can design hierarchical networks using various types of nodes like ...
Competencies for ITNW 2413.doc
... • Define and install the necessary hardware required to communicate over a computer network • Demonstrate the mathematical skills required to work with integer decimal, binary, and hexadecimal numbers and simple binary logic • Define the structure, components, and technologies of modern computer net ...
... • Define and install the necessary hardware required to communicate over a computer network • Demonstrate the mathematical skills required to work with integer decimal, binary, and hexadecimal numbers and simple binary logic • Define the structure, components, and technologies of modern computer net ...
Slide 1
... – Web, e-mail, etc. do have ports assigned by the IANA – BitTorrent, Gnutella, Napster, etc. do not ...
... – Web, e-mail, etc. do have ports assigned by the IANA – BitTorrent, Gnutella, Napster, etc. do not ...
View
... Not every device plugs directly into the central hub. The majority of devices connect to secondary hub that in turn is connected to the central hub The advantages and disadvantages of tree topology are generally the same as those of star. The addition of secondary hubs bring more advantage: ...
... Not every device plugs directly into the central hub. The majority of devices connect to secondary hub that in turn is connected to the central hub The advantages and disadvantages of tree topology are generally the same as those of star. The addition of secondary hubs bring more advantage: ...
Job Class: 158814 Rev: 04/15 Exempt Page: 1
... Incumbent in this position is responsible for assisting in the design, installation, upgrade, and support of the Campus Enterprise Backbone Network and the Network Management. This position reviews network logs to check for hardware or software abnormalities, creates and maintains advanced network s ...
... Incumbent in this position is responsible for assisting in the design, installation, upgrade, and support of the Campus Enterprise Backbone Network and the Network Management. This position reviews network logs to check for hardware or software abnormalities, creates and maintains advanced network s ...
Information Systems and Networking I
... (D) To synchronize sequence numbers prior to data transmission. 19. TCP is a connection-oriented protocol. Which correctly describes TCP? (A) Data is sent using best-effort delivery. (B) Data is sent after a virtual connection is established at both ends. (C) Data is sent as soon as it is requested ...
... (D) To synchronize sequence numbers prior to data transmission. 19. TCP is a connection-oriented protocol. Which correctly describes TCP? (A) Data is sent using best-effort delivery. (B) Data is sent after a virtual connection is established at both ends. (C) Data is sent as soon as it is requested ...
Introduction to Transport Layer
... Now, the transport layer needs a way to determine which application the packet needs to be delivered. This is the demultiplexing problem. ...
... Now, the transport layer needs a way to determine which application the packet needs to be delivered. This is the demultiplexing problem. ...
Networking
... If only one vlan is required on the port they can assign a vlan that applies to all traffic. Untagged means no vlan embedded in them, port assigns vlan Tagged Packets have the vlan imbedded in the packet using 802.1q ...
... If only one vlan is required on the port they can assign a vlan that applies to all traffic. Untagged means no vlan embedded in them, port assigns vlan Tagged Packets have the vlan imbedded in the packet using 802.1q ...
Slide 1
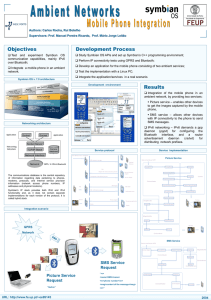
... ambient network, by providing two services: Picture service – enables other devices to get the images captured by the mobile phone, SMS service – allows other devices with IP connectivity to the phone to send SMS messages. ...
... ambient network, by providing two services: Picture service – enables other devices to get the images captured by the mobile phone, SMS service – allows other devices with IP connectivity to the phone to send SMS messages. ...
1998-11-19-MIEM-WirelessWANs
... Forwards or doesn’t forward information based upon the destination MAC address of the network packet Maintains a table of which MAC address is on which side (wireless or Ethernet) Will not forward traffic across the WAN link if it knows the recipient computer is on its own network Modern units do mo ...
... Forwards or doesn’t forward information based upon the destination MAC address of the network packet Maintains a table of which MAC address is on which side (wireless or Ethernet) Will not forward traffic across the WAN link if it knows the recipient computer is on its own network Modern units do mo ...
1-ITN-chap-3g
... that governs the way a web server and a web client interact. Transport Protocol - Transmission Control Protocol (TCP) is the transport protocol that manages the individual conversations between web servers and web clients. Internet Protocol - IP is responsible for assigning the appropriate addre ...
... that governs the way a web server and a web client interact. Transport Protocol - Transmission Control Protocol (TCP) is the transport protocol that manages the individual conversations between web servers and web clients. Internet Protocol - IP is responsible for assigning the appropriate addre ...
Chapter 12
... point-to-point configuration to a central hub • Hub can route messages from one node to another or a subset of nodes ...
... point-to-point configuration to a central hub • Hub can route messages from one node to another or a subset of nodes ...
Computer Networking - Electronic, Electrical and Systems Engineering
... can all read and write to each others computers. In the past, such networks were not connected to the Internet (the ultimate security solution?) Medium Networks Between 10 and 200 users, often with a single server. Still managed by one administrator who controls everything. Users still know ...
... can all read and write to each others computers. In the past, such networks were not connected to the Internet (the ultimate security solution?) Medium Networks Between 10 and 200 users, often with a single server. Still managed by one administrator who controls everything. Users still know ...
IP_review
... Segmenting upper-layer application data Establishing end-to-end operations Sending segments from one end host to another end host Ensuring data reliability Providing flow control ...
... Segmenting upper-layer application data Establishing end-to-end operations Sending segments from one end host to another end host Ensuring data reliability Providing flow control ...
Chapter 1 THE INFORMATION AGE IN WHICH YOU LIVE Changing
... Virus – software written with malicious intent to cause annoyance or damage Worm – spreads itself from computer to computer via e-mail and other network traffic Spyware – collects information about you and reports it to someone else without your permission ...
... Virus – software written with malicious intent to cause annoyance or damage Worm – spreads itself from computer to computer via e-mail and other network traffic Spyware – collects information about you and reports it to someone else without your permission ...
Introduction
... Segmenting upper-layer application data Establishing end-to-end operations Sending segments from one end host to another end host Ensuring data reliability Providing flow control ...
... Segmenting upper-layer application data Establishing end-to-end operations Sending segments from one end host to another end host Ensuring data reliability Providing flow control ...