What*s inside your network?
... If traffic is encrypted, only the basic routing information (packet header) can be monitored and processed by an IPS or an application firewall unless the encryption is broken Only the end host and the destination have the key to the ...
... If traffic is encrypted, only the basic routing information (packet header) can be monitored and processed by an IPS or an application firewall unless the encryption is broken Only the end host and the destination have the key to the ...
Internet and LAN Technology
... Ethernet • Varies in speed from 10 Mbps to 10 Gbps • An Ethernet card is designed to support the Ethernet protocols • Ethernet hubs link workstations via cables – Uplink port ...
... Ethernet • Varies in speed from 10 Mbps to 10 Gbps • An Ethernet card is designed to support the Ethernet protocols • Ethernet hubs link workstations via cables – Uplink port ...
Networking Concepts An Introduction to
... the largest or most significant digit is to the left. Digits in binary numbers have the special name, bit. The name bit is a contraction of binary and digit. In the computing world, we often refer to a grouping of 8 bits and call it a byte. In this course, we'll work exclusively with binary numbers ...
... the largest or most significant digit is to the left. Digits in binary numbers have the special name, bit. The name bit is a contraction of binary and digit. In the computing world, we often refer to a grouping of 8 bits and call it a byte. In this course, we'll work exclusively with binary numbers ...
Slide 1
... “A smart grid uses information technology to improve the reliability, availability and efficiency of the electric system: from large generation through the delivery system to electricity consumers and eventually to individual end‐uses or appliances. The information networks that are transforming ou ...
... “A smart grid uses information technology to improve the reliability, availability and efficiency of the electric system: from large generation through the delivery system to electricity consumers and eventually to individual end‐uses or appliances. The information networks that are transforming ou ...
ROB: Route Optimization Assisted by BGP
... • Considering mobility of an entire network, – it is possible to use Mobile IP to enable mobility for all the devices within the mobile network. – However, this would • require all the devices to be Mobile IP capable and • will incur significant overhead, – i.e, a storm of control packets as every d ...
... • Considering mobility of an entire network, – it is possible to use Mobile IP to enable mobility for all the devices within the mobile network. – However, this would • require all the devices to be Mobile IP capable and • will incur significant overhead, – i.e, a storm of control packets as every d ...
Survey of Active network
... —Active network involve the synthesis and extension of programming language ,operating systems ,and networking expertise — Protocol booster are a ideal application for an on-the-fly(dynamic) programmable network infrastructure — In place of protocol stack ,application may use protocol components tha ...
... —Active network involve the synthesis and extension of programming language ,operating systems ,and networking expertise — Protocol booster are a ideal application for an on-the-fly(dynamic) programmable network infrastructure — In place of protocol stack ,application may use protocol components tha ...
arpn-jeas-icstartemplate
... Based on our knowledge, there are not so many works in this area. The preliminary concept of network virtualization, which is called Telecom Application Server (TAS), have been developed by Rhino [1] and Aricent [2]. The TAS is a set of telecommunication processes that is ...
... Based on our knowledge, there are not so many works in this area. The preliminary concept of network virtualization, which is called Telecom Application Server (TAS), have been developed by Rhino [1] and Aricent [2]. The TAS is a set of telecommunication processes that is ...
for ResNet - University of Michigan
... • Efficient use of IP space • Students are not required to know the MAC address of their NIC • Contact/location info is gathered from reliable source rather than having students or consultants enter the data • Requires very little administration time beyond initial configuration of networks ...
... • Efficient use of IP space • Students are not required to know the MAC address of their NIC • Contact/location info is gathered from reliable source rather than having students or consultants enter the data • Requires very little administration time beyond initial configuration of networks ...
Slides for Penn Reading Project - the Department of Computer and
... The Internet: What is It? • The Internet is a massive network of connected but decentralized computers • Began as an experimental research NW of the DoD (ARPAnet) in the 1970s • All aspects (protocols, services, hardware, software) evolved over many years • Many individuals and organizations contri ...
... The Internet: What is It? • The Internet is a massive network of connected but decentralized computers • Began as an experimental research NW of the DoD (ARPAnet) in the 1970s • All aspects (protocols, services, hardware, software) evolved over many years • Many individuals and organizations contri ...
100% real exam questions answers
... A network device needs to be installed in the place of the icon labeled Network Device to accommodate a leased line attachment to the Internet. Which network device and interface configuration meets the minimum requirements for this installation? A. B. C. D. E. ...
... A network device needs to be installed in the place of the icon labeled Network Device to accommodate a leased line attachment to the Internet. Which network device and interface configuration meets the minimum requirements for this installation? A. B. C. D. E. ...
Unit 3 Internet Basics_3.01 Networks-Travel Back in
... – Take a screenshot at the end of video • Save to your F Drive in your Unit 3 Folder as – 3.01 How Networks Work ...
... – Take a screenshot at the end of video • Save to your F Drive in your Unit 3 Folder as – 3.01 How Networks Work ...
Connectrix B-Series Management Simplified and Automated Network Management
... Fabric Performance Impact Automatically monitors and detects network congestion in the fabric and identifies which devices are impacted by a bottleneck port. Port Profiles: Easily configures network policies for ports with risk tolerance-based templates, including server ports, storage ports and E_P ...
... Fabric Performance Impact Automatically monitors and detects network congestion in the fabric and identifies which devices are impacted by a bottleneck port. Port Profiles: Easily configures network policies for ports with risk tolerance-based templates, including server ports, storage ports and E_P ...
Technology and Convergence Looking Back and Looking
... Consumer perspective: freedom to use broadband to access content, applications and devices of their choice Company perspective: broadband networks may not “discriminate” in favor of their own or affiliated content, applications or devices ...
... Consumer perspective: freedom to use broadband to access content, applications and devices of their choice Company perspective: broadband networks may not “discriminate” in favor of their own or affiliated content, applications or devices ...
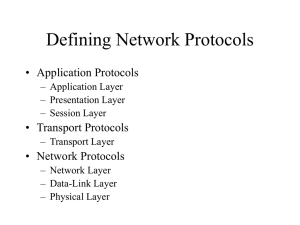
Defining Network Protocols
... • Dynamic Host Configuration Protocol • Assigns IP address, gateway (router) address, name server, netmask, time server, and other configuration information based on a NIC’s MAC address • IP addresses may be fixed or taken from a pool of available addresses • Allows assigning temporary addresses for ...
... • Dynamic Host Configuration Protocol • Assigns IP address, gateway (router) address, name server, netmask, time server, and other configuration information based on a NIC’s MAC address • IP addresses may be fixed or taken from a pool of available addresses • Allows assigning temporary addresses for ...
Week One
... • At each layer, protocols are used to communicate • Control information is added to user data at each layer • Transport layer may fragment user data • Each fragment has a transport header added – Destination SAP – Sequence number – Error detection code ...
... • At each layer, protocols are used to communicate • Control information is added to user data at each layer • Transport layer may fragment user data • Each fragment has a transport header added – Destination SAP – Sequence number – Error detection code ...
Software*Defined Networking (SDN)
... The control plane and the data plane are joined together in a network device. ...
... The control plane and the data plane are joined together in a network device. ...
IEEE Communications-2017 - Levine Lectronics and Lectric
... • Up to 127 devices can connect to the host, either directly or by way of USB hubs. • Individual USB cables can run as long as 5 meters; with hubs, devices can be up to 30 meters away from the host. • With USB 2.,the bus has a maximum data rate of 480 Mb per second. • With USB 3.,the bus has a maxim ...
... • Up to 127 devices can connect to the host, either directly or by way of USB hubs. • Individual USB cables can run as long as 5 meters; with hubs, devices can be up to 30 meters away from the host. • With USB 2.,the bus has a maximum data rate of 480 Mb per second. • With USB 3.,the bus has a maxim ...
Introduction to HTML - Department of Computing and Software
... Review of basic concepts Internet: is a wide area network connecting many smaller heterogeneous networks extending to most countries in the world. It has become the primary vehicle for computer to computer communication and has in access of ten million computers connected to it directly. Peer to Pe ...
... Review of basic concepts Internet: is a wide area network connecting many smaller heterogeneous networks extending to most countries in the world. It has become the primary vehicle for computer to computer communication and has in access of ten million computers connected to it directly. Peer to Pe ...
iRX Data Sheet
... • GPS loop-back to user defined server • Store, hold and forward for GPS and telemetry data • Internal battery charging control circuit for remote operations Integration For Various Applications The stand-alone unit is an easy-to-integrate, cost-effective, 24/7 communication solution for applications ...
... • GPS loop-back to user defined server • Store, hold and forward for GPS and telemetry data • Internal battery charging control circuit for remote operations Integration For Various Applications The stand-alone unit is an easy-to-integrate, cost-effective, 24/7 communication solution for applications ...
Network Evolution in Coming 10 Years: How We Will Communicate
... Eventually population growth in machine will force enhancement of communication Human ability to communicate (to human or to machine) limited to: ...
... Eventually population growth in machine will force enhancement of communication Human ability to communicate (to human or to machine) limited to: ...
Modem
... • communication device to link LAN to WAN • decides on the best path for data through the network – receives data and forwards it to the correct location ...
... • communication device to link LAN to WAN • decides on the best path for data through the network – receives data and forwards it to the correct location ...