SIS-DTN_Green Book v0.6-v0.7 changes
... continuing to extend this model so that agencies can share resources such as ground stations for crosssupport. This sharing is implemented by tunneling the space data link from the ground station across the terrestrial communications infrastructure to the control center, so that the ground station a ...
... continuing to extend this model so that agencies can share resources such as ground stations for crosssupport. This sharing is implemented by tunneling the space data link from the ground station across the terrestrial communications infrastructure to the control center, so that the ground station a ...
An Overlay-Based Data Mining Architecture
... and service availability are critical issues for parallel data mining architecture. As a remedy for improving scalability, an overlay-based parallel data mining architecture has been proposed. Since all the nodes execute both management and processing functions by using overlay network, this archite ...
... and service availability are critical issues for parallel data mining architecture. As a remedy for improving scalability, an overlay-based parallel data mining architecture has been proposed. Since all the nodes execute both management and processing functions by using overlay network, this archite ...
Philip Schoene, PBS
... Overview of the PBS DDMS Use of open internet for transport stream delivery for PBS Diversity site Comparison to dedicated EPL connection for ...
... Overview of the PBS DDMS Use of open internet for transport stream delivery for PBS Diversity site Comparison to dedicated EPL connection for ...
- IEEE Mentor
... ・ spectrum resource measurements and network performance metrics, such as packet error ratio, delay, etc, ・ information elements and data structures to capture these measurements, ・ procedures for collecting and exchanging spectrum resource measurement information with higher layers or other devices ...
... ・ spectrum resource measurements and network performance metrics, such as packet error ratio, delay, etc, ・ information elements and data structures to capture these measurements, ・ procedures for collecting and exchanging spectrum resource measurement information with higher layers or other devices ...
ppt
... [15a] "All Quiet on the Internet Front" [15b] "DARPA: Nobody's Safe on the Internet" [17a] "Rapidly Recovering from the Catastrophic Loss of a Major Telecommunications Office" ...
... [15a] "All Quiet on the Internet Front" [15b] "DARPA: Nobody's Safe on the Internet" [17a] "Rapidly Recovering from the Catastrophic Loss of a Major Telecommunications Office" ...
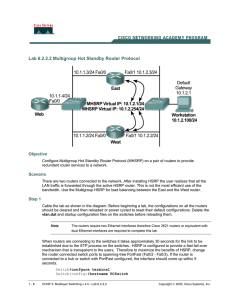
Lab 6.2.2.2 Multigroup Hot Standby Router Protocol
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
Network Performance Troubleshooting
... (2) Kernel hands the data to the IP stack to encapsulate it in a PDU (3) Kernel puts the PDU on a transmit queue for the device in question (4) Device driver picks PDUs from the queue and copies them to the NIC (5) NIC sends the PDU over the wire (6) NIC notifies the kernel about the transmissio ...
... (2) Kernel hands the data to the IP stack to encapsulate it in a PDU (3) Kernel puts the PDU on a transmit queue for the device in question (4) Device driver picks PDUs from the queue and copies them to the NIC (5) NIC sends the PDU over the wire (6) NIC notifies the kernel about the transmissio ...
IOSR Journal of Computer Engineering (IOSRJCE)
... A network interface card that supports a TCP/IP stack Same Linux distribution and version as the server node All clients must have the same architecture Monitors and keyboards may be helpful but not required 1.4 Cluster computing implementation using MPI: Message passing is a model for interactions ...
... A network interface card that supports a TCP/IP stack Same Linux distribution and version as the server node All clients must have the same architecture Monitors and keyboards may be helpful but not required 1.4 Cluster computing implementation using MPI: Message passing is a model for interactions ...
Peer-to-Peer Algorithms and Systems
... – If file is found in multiple nodes, user can select parallel downloading – Most likely HTTP byte-range header used to request different portions of the file from different nodes – Automatic recovery when server peer stops sending file ...
... – If file is found in multiple nodes, user can select parallel downloading – Most likely HTTP byte-range header used to request different portions of the file from different nodes – Automatic recovery when server peer stops sending file ...
Cloud Computing-OpenStack-Lecture 7
... Management of compute resources i.e. CPU, memory, disk, and network interfaces. Management of Local Area Networks API with rate limiting and Authentication to manage who has access to compute resources and prevent users from impacting each other with excessive API utilization Distributed and ...
... Management of compute resources i.e. CPU, memory, disk, and network interfaces. Management of Local Area Networks API with rate limiting and Authentication to manage who has access to compute resources and prevent users from impacting each other with excessive API utilization Distributed and ...
Ethernet
... We would have run out of version 4 addresses some time ago if we still used only classful addresses. ...
... We would have run out of version 4 addresses some time ago if we still used only classful addresses. ...
fw_detect
... have their Pro's and Con's. Application Proxies are far more strict on letting packets into the network, as well as being harsh for any packets sent outward. Packet Filtering Gateways can be found on large corporate networks, they have high performance and inbound traffic requirements. Firewalls hav ...
... have their Pro's and Con's. Application Proxies are far more strict on letting packets into the network, as well as being harsh for any packets sent outward. Packet Filtering Gateways can be found on large corporate networks, they have high performance and inbound traffic requirements. Firewalls hav ...
Link Layer Protocols
... error detection (no correction) connection liveness: detect, signal link failure to network layer network layer address negotiation: endpoint can learn/configure each other’s network address 5: DataLink Layer ...
... error detection (no correction) connection liveness: detect, signal link failure to network layer network layer address negotiation: endpoint can learn/configure each other’s network address 5: DataLink Layer ...
Introduction - Aaron Striegel
... KaZaA (Kazaa) • In 2001, Kazaa created by Dutch company KaZaA BV. • Single network called FastTrack used by other clients as well: Morpheus, giFT, etc. • Eventually protocol changed so other clients could no longer talk to it. • 2004: 2nd most popular file sharing network, 1-5million at any given t ...
... KaZaA (Kazaa) • In 2001, Kazaa created by Dutch company KaZaA BV. • Single network called FastTrack used by other clients as well: Morpheus, giFT, etc. • Eventually protocol changed so other clients could no longer talk to it. • 2004: 2nd most popular file sharing network, 1-5million at any given t ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... A wireless sensor network refers to a group of spatially dispersed and dedicated sensors for monitoring and recording the physical conditions of the environment and organizing the collected data at a central location. Wireless sensor network monitor physical or environmental conditions, such as temp ...
... A wireless sensor network refers to a group of spatially dispersed and dedicated sensors for monitoring and recording the physical conditions of the environment and organizing the collected data at a central location. Wireless sensor network monitor physical or environmental conditions, such as temp ...
General
... The main core of the IMS is the session control protocol realized with the SIP protocol. SIP is easy in use and smoothly cooperates with internet protocols such as the HTTP. Also SIP is modifiable in terms of supported messages and procedures With the exception of the Media Gateways, all IMS compone ...
... The main core of the IMS is the session control protocol realized with the SIP protocol. SIP is easy in use and smoothly cooperates with internet protocols such as the HTTP. Also SIP is modifiable in terms of supported messages and procedures With the exception of the Media Gateways, all IMS compone ...
CS610 Final term MAGA file.. all paperz are in 1 file..pages 1 to 42
... data unit through a parity generator, which counts the 1’s and appends the parity bit (1) to the end The total number of 1’s is now 4, an even number The system now transfers the entire expanded across the network link When it reaches its destination, the RX puts all 8 bits through an even parity ch ...
... data unit through a parity generator, which counts the 1’s and appends the parity bit (1) to the end The total number of 1’s is now 4, an even number The system now transfers the entire expanded across the network link When it reaches its destination, the RX puts all 8 bits through an even parity ch ...
Network Management Integration Options
... outage. Also, integrated into this module, is the ability to locate the controllers deployed in different parts of the world and view their sessions. This heartbeat mechanism allows the Pronto OSS to manage private networks that may reside behind firewall or Network Access Translation routers, etc. ...
... outage. Also, integrated into this module, is the ability to locate the controllers deployed in different parts of the world and view their sessions. This heartbeat mechanism allows the Pronto OSS to manage private networks that may reside behind firewall or Network Access Translation routers, etc. ...
TL-WR542G 54M Wireless Router
... administrators can establish restricted access policies for children or staff. It has built-in NAT and DHCP server supporting static IP address distributing. It also supports Virtual Server and DMZ host for Port Triggering needs, and remote management and log so that network administrators can manag ...
... administrators can establish restricted access policies for children or staff. It has built-in NAT and DHCP server supporting static IP address distributing. It also supports Virtual Server and DMZ host for Port Triggering needs, and remote management and log so that network administrators can manag ...
Classification of Artificial Neural Networks
... rules. Researchers are explored different neural network architectures and used for various applications. Therefore the classification of artificial neural networks (ANN) can be done based on structures and based on type of data. A single neuron can perform a simple pattern classification, but the p ...
... rules. Researchers are explored different neural network architectures and used for various applications. Therefore the classification of artificial neural networks (ANN) can be done based on structures and based on type of data. A single neuron can perform a simple pattern classification, but the p ...
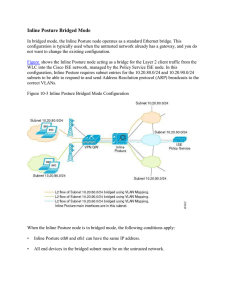
15360608-Inline Posture Bridged Mode
... device, or the MAC address and IP address of the device on which to filter. You can use MAC and subnet filters to bypass Inline Posture enforcement to certain endpoints or devices on the untrusted side of the network. For example, if VPN or WLC management traffic is required to pass through Inline P ...
... device, or the MAC address and IP address of the device on which to filter. You can use MAC and subnet filters to bypass Inline Posture enforcement to certain endpoints or devices on the untrusted side of the network. For example, if VPN or WLC management traffic is required to pass through Inline P ...
Fault Management for Multiservice Interworking, Version 2.0
... High Order Domain Specific Part End System Identifier ...
... High Order Domain Specific Part End System Identifier ...
Reference Manual for the 108 Mbps Wireless Firewall Router WGT624
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiat ...
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiat ...