comm3380-Notes05-Routing_B
... distance to the destination (in hops). A router can represent all the information in its routing table as a list of pairs of destination and distance values. At regular intervals each router sends its routing table as distance vector values to each of its neighbouring routers. The list of distanceve ...
... distance to the destination (in hops). A router can represent all the information in its routing table as a list of pairs of destination and distance values. At regular intervals each router sends its routing table as distance vector values to each of its neighbouring routers. The list of distanceve ...
Mobility System Software Release Notes 8.0.3.6
... receiver. TxBF can increase the Signal-to-Noise Ratio (SNR) at the receiver and improve performance. This feature is supported on the WLA532,WLA321, and WLA322. ...
... receiver. TxBF can increase the Signal-to-Noise Ratio (SNR) at the receiver and improve performance. This feature is supported on the WLA532,WLA321, and WLA322. ...
NFD-Android: NDN Networking Stack for Android Platform
... Haitao Zhang, Alex Afanasyev, Lixia Zhang (UCLA) NDNComm 2017 March 23-26, 2017 ...
... Haitao Zhang, Alex Afanasyev, Lixia Zhang (UCLA) NDNComm 2017 March 23-26, 2017 ...
Practical Far-End NAT Traversal for VoIP Whitepaper PDF
... requirements of the more restrictive firewalls, as long as the firewalls themselves are configured to support Reflexive UDP Admission. If, at any time during the call, the caller behind the firewall stops sending media outbound for a sufficient amount of time, there is no guarantee that the firewall ...
... requirements of the more restrictive firewalls, as long as the firewalls themselves are configured to support Reflexive UDP Admission. If, at any time during the call, the caller behind the firewall stops sending media outbound for a sufficient amount of time, there is no guarantee that the firewall ...
What is Wireless Mesh Network?
... A single-radio router shares bandwidth between users and the backhaul. If two radios are used, one is dedicated to the frontside clients and the other to the backhaul. In three-radio routers, two radios are used for the backhaul and can transmit and receive simultaneously over different Wi-Fi channe ...
... A single-radio router shares bandwidth between users and the backhaul. If two radios are used, one is dedicated to the frontside clients and the other to the backhaul. In three-radio routers, two radios are used for the backhaul and can transmit and receive simultaneously over different Wi-Fi channe ...
QNX® real-time operating system
... The QNX Micro kernel supports three essential types of IPC: • Messages - the fundamental form of IPC in QNX. They provide synchronous communication between cooperating processes where the process sending the message requires proof of receipt and potentially a reply to the message. • Proxies - a spec ...
... The QNX Micro kernel supports three essential types of IPC: • Messages - the fundamental form of IPC in QNX. They provide synchronous communication between cooperating processes where the process sending the message requires proof of receipt and potentially a reply to the message. • Proxies - a spec ...
Chapter 2: How LAN and WAN Communications Work
... another. No single node has priority over another node. The nodes listen for any packet traffic on the cable. If a packet is detected, the nonsending nodes go into “defer” mode. The Ethernet protocol permits only one node to transmit at a time. Transmission is accomplished by sending a carrier signa ...
... another. No single node has priority over another node. The nodes listen for any packet traffic on the cable. If a packet is detected, the nonsending nodes go into “defer” mode. The Ethernet protocol permits only one node to transmit at a time. Transmission is accomplished by sending a carrier signa ...
TD-W8951ND 150Mbps Wireless N ADSL2+ Modem Router Rev: 3.0.1
... ADSL connection is made using ordinary telephone line with standard connectors. Multiple workstations can be networked and connected to the Internet using a single Wide Area Network (WAN) interface and single global IP address. The advanced security enhancements, IP/MAC Filter, Application Filter an ...
... ADSL connection is made using ordinary telephone line with standard connectors. Multiple workstations can be networked and connected to the Internet using a single Wide Area Network (WAN) interface and single global IP address. The advanced security enhancements, IP/MAC Filter, Application Filter an ...
NetCom Specifications - Mitsubishi Electric Power Products, Inc.
... to provide RS-232 to SNMP gateway capability as well as http web browser support. The NetCom can be attached to a UPS or other device to allow a network supervisor to monitor and control the UPS via the SNMP protocol (Simple Network management protocol) over TCP/IP networks. The product can be view ...
... to provide RS-232 to SNMP gateway capability as well as http web browser support. The NetCom can be attached to a UPS or other device to allow a network supervisor to monitor and control the UPS via the SNMP protocol (Simple Network management protocol) over TCP/IP networks. The product can be view ...
SIP messages
... up IPsec security associations supports both Pre-Shared Key (PSK) and Public Key (PKI) based authentication. Because the IP addresses of the SIP user agents will be mostly dynamic and taking into account that IKE Main Mode in that case does not work with pre-shared secrets and that IKE Aggressive Mo ...
... up IPsec security associations supports both Pre-Shared Key (PSK) and Public Key (PKI) based authentication. Because the IP addresses of the SIP user agents will be mostly dynamic and taking into account that IKE Main Mode in that case does not work with pre-shared secrets and that IKE Aggressive Mo ...
M.Tech (Information Technology) - National Institute Of Engineering
... Congestion-Avoidance Mechanisms, DEC bit, Random Early Detection (RED), Source-Based Congestion Avoidance. The Domain Name System(DNS),Electronic Mail(SMTP,POP,IMAP,MIME),World Wide Web(HTTP) Self learning component: Network Management(SNMP) . LABORATORY WORK PART A: Implement the following using C/ ...
... Congestion-Avoidance Mechanisms, DEC bit, Random Early Detection (RED), Source-Based Congestion Avoidance. The Domain Name System(DNS),Electronic Mail(SMTP,POP,IMAP,MIME),World Wide Web(HTTP) Self learning component: Network Management(SNMP) . LABORATORY WORK PART A: Implement the following using C/ ...
Cellular IP: A New Approach to Internet Host Mobility
... is needed in each office or office floor. On the other hand, Cellular IP can also be implemented on top of regular IP routers to allow for easy migration from existing installations. Another key design consideration is scalability. The Cellular IP distributed location management makes it possible to ...
... is needed in each office or office floor. On the other hand, Cellular IP can also be implemented on top of regular IP routers to allow for easy migration from existing installations. Another key design consideration is scalability. The Cellular IP distributed location management makes it possible to ...
Prestige 645M
... mechanical, magnetic, optical, chemical, photocopying, manual, or otherwise, without the prior written permission of ZyXEL Communications Corporation. Published by ZyXEL Communications Corporation. All rights reserved. Disclaimer ZyXEL does not assume any liability arising out of the application or ...
... mechanical, magnetic, optical, chemical, photocopying, manual, or otherwise, without the prior written permission of ZyXEL Communications Corporation. Published by ZyXEL Communications Corporation. All rights reserved. Disclaimer ZyXEL does not assume any liability arising out of the application or ...
Network Centric Bridges to Legacy Systems
... • Key Successes: •Bowman signals an improvement over Clansman, particularly by: • Providing secure communications over greater ranges • Enhanced situational awareness, though not down to individual platform level •But it has been plagued by a series of significant technological, training and deploym ...
... • Key Successes: •Bowman signals an improvement over Clansman, particularly by: • Providing secure communications over greater ranges • Enhanced situational awareness, though not down to individual platform level •But it has been plagued by a series of significant technological, training and deploym ...
Implementing PCI — A Guide for Network Security Engineers
... Injection and Web application attacks have become very prevalent as tools for both internal and external attack vectors. These exploits are frequently coupled with the inclusion of polymorphic malware that is used to siphon and extract sensitive data from within victim organizations. In response to ...
... Injection and Web application attacks have become very prevalent as tools for both internal and external attack vectors. These exploits are frequently coupled with the inclusion of polymorphic malware that is used to siphon and extract sensitive data from within victim organizations. In response to ...
ICMP
... – The sending and receiving devices must have the TCP/IP protocol stack properly configured. – This includes the installation of the TCP/IP protocol and proper configuration of IP address and subnet mask. – A default gateway must also be configured if datagrams are to travel outside of the local net ...
... – The sending and receiving devices must have the TCP/IP protocol stack properly configured. – This includes the installation of the TCP/IP protocol and proper configuration of IP address and subnet mask. – A default gateway must also be configured if datagrams are to travel outside of the local net ...
ccna3 3.0-04 Introduction to LAN Switching
... To the network this appears as a single one way bridge. Both devices are contending for the right to use the single shared medium. The CD (collision detection) circuit on each node contends for the use of the network when the two nodes attempt to transmit at the same time. After a collision occurs, ...
... To the network this appears as a single one way bridge. Both devices are contending for the right to use the single shared medium. The CD (collision detection) circuit on each node contends for the use of the network when the two nodes attempt to transmit at the same time. After a collision occurs, ...
Configuring Juniper Networks SSL VPN Security
... resources of a private enterprise network taking advantage of the inherent SSL functionality built into standard Web browsers. Secure access to the enterprise network from a Web browser accommodates most users’ application needs operating at the application-layer, i.e., e-mail, web browsing and file ...
... resources of a private enterprise network taking advantage of the inherent SSL functionality built into standard Web browsers. Secure access to the enterprise network from a Web browser accommodates most users’ application needs operating at the application-layer, i.e., e-mail, web browsing and file ...
ccna1-mod10-Routing
... Routing Information Protocol (RIP) was originally specified in RFC 1058. • It is a distance vector routing protocol. • Hop count is used as the metric for path selection. • If the hop count is greater than 15, the packet is discarded. • Routing updates are broadcast every 30 seconds, by default. Int ...
... Routing Information Protocol (RIP) was originally specified in RFC 1058. • It is a distance vector routing protocol. • Hop count is used as the metric for path selection. • If the hop count is greater than 15, the packet is discarded. • Routing updates are broadcast every 30 seconds, by default. Int ...
20110310-OSG-NPW-Tools
... – Name and address of remote host – Maximum number of link before giving up ...
... – Name and address of remote host – Maximum number of link before giving up ...
irewall Presentation F Mike Shinn Casey Priester
... • At Defcon 19 (Dec 2011), Palo Alto firewall demonstrated to have fatal design flaw 1. Pescatore, J. & Young, G. (2009, October 19). Defining the Next-Generation Firewall. Gartner RAS Core Research Group. Retrieved from: http://img1.custompublish.com/getfile.php/1434855.1861.sqqycbrdwq/Defining+the ...
... • At Defcon 19 (Dec 2011), Palo Alto firewall demonstrated to have fatal design flaw 1. Pescatore, J. & Young, G. (2009, October 19). Defining the Next-Generation Firewall. Gartner RAS Core Research Group. Retrieved from: http://img1.custompublish.com/getfile.php/1434855.1861.sqqycbrdwq/Defining+the ...
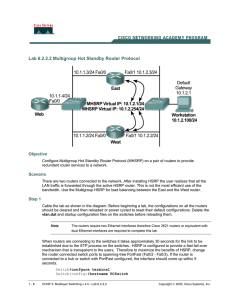
Lab 6.2.2.2 Multigroup Hot Standby Router Protocol
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
Literature Library - Rockwell Automation
... be used as well. Contact SIGMA Support if you need to use one of these. The driver is specified in the file :sd:/rmx386/config/tcpstart.csd Note: The reason you are changing the driver is probably because you can't get the Ethernet to work, preventing using FTP. The following is an example of copyin ...
... be used as well. Contact SIGMA Support if you need to use one of these. The driver is specified in the file :sd:/rmx386/config/tcpstart.csd Note: The reason you are changing the driver is probably because you can't get the Ethernet to work, preventing using FTP. The following is an example of copyin ...