SweetBait: Zero-Hour Worm Detection and Containment Using Honeypots
... and blocking bona fide traffic may result in unleashing a denial of service attack by the defence mechanism. 2. Individuals rather than families. Most existing systems extract the signature of an individual worm with no attempt to check whether this is a variation of a worm that was previously detec ...
... and blocking bona fide traffic may result in unleashing a denial of service attack by the defence mechanism. 2. Individuals rather than families. Most existing systems extract the signature of an individual worm with no attempt to check whether this is a variation of a worm that was previously detec ...
Static Routes
... forward or route the packets. Routers forward, or route, packets defined by routed protocols. Examples include IP and IPX (a part of the Novell NetWare protocol model). ...
... forward or route the packets. Routers forward, or route, packets defined by routed protocols. Examples include IP and IPX (a part of the Novell NetWare protocol model). ...
Document
... • Describe the objects and components of Active Directory that relate to the physical structure • Understand how to plan the physical structure of Active Directory and consider how the topology of your network will affect your design ...
... • Describe the objects and components of Active Directory that relate to the physical structure • Understand how to plan the physical structure of Active Directory and consider how the topology of your network will affect your design ...
TD-W8960N 300Mbps Wireless N ADSL2+ Modem Router Rev: 5.0.0
... The TD-W8960N 300Mbps Wireless N ADSL2+ Modem Router integrates 4-port Switch, Firewall, NAT-Router and Wireless AP. Powered by 2x2 MIMO technology, the Wireless N Router delivers exceptional range and speed, which can fully meet the need of Small Office/Home Office (SOHO) networks and the users dem ...
... The TD-W8960N 300Mbps Wireless N ADSL2+ Modem Router integrates 4-port Switch, Firewall, NAT-Router and Wireless AP. Powered by 2x2 MIMO technology, the Wireless N Router delivers exceptional range and speed, which can fully meet the need of Small Office/Home Office (SOHO) networks and the users dem ...
Awesome PowerPoint Background Template
... conflicts by polling hosts in the network. Timeout delays and retry constants are limiting when the size/shape of network is unknown. – If multiple hosts request an IP concurrently, PMWRS may assign two hosts the same IP. – Much of the 169.254.*.* address block is reserved by IETF for future use. ...
... conflicts by polling hosts in the network. Timeout delays and retry constants are limiting when the size/shape of network is unknown. – If multiple hosts request an IP concurrently, PMWRS may assign two hosts the same IP. – Much of the 169.254.*.* address block is reserved by IETF for future use. ...
White Paper
... reach multi-vendor interoperability as well. It seems it is not trivial to retrofit existing IP/MPLS protocols to the new MPLS-TP suite. On the Carrier Ethernet service side of things, performance monitoring based on Y.1731 showed great progress once more. Four of the Ethernet OAM ...
... reach multi-vendor interoperability as well. It seems it is not trivial to retrofit existing IP/MPLS protocols to the new MPLS-TP suite. On the Carrier Ethernet service side of things, performance monitoring based on Y.1731 showed great progress once more. Four of the Ethernet OAM ...
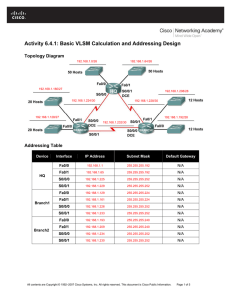
Activity 6.4.1: Basic VLSM Calculation and Addressing Design
... 4. What is the maximum number of host IP addresses that are needed for a single subnet? _______ 5. What is the least number of host IP addresses that are needed for a single subnet? _______ 6. How many IP addresses are needed for the East portion of the network? Be sure to include the WAN links betw ...
... 4. What is the maximum number of host IP addresses that are needed for a single subnet? _______ 5. What is the least number of host IP addresses that are needed for a single subnet? _______ 6. How many IP addresses are needed for the East portion of the network? Be sure to include the WAN links betw ...
ppt
... Ning Weng, Tilman Wolf, “Profiling and mapping of parallel workloads on network processors”, ACM Symposium of Applied Computing (SAC 2005), pp. 890-896 Ning Weng, Tilman Wolf, “Analytic modeling of network processors for parallel workload ...
... Ning Weng, Tilman Wolf, “Profiling and mapping of parallel workloads on network processors”, ACM Symposium of Applied Computing (SAC 2005), pp. 890-896 Ning Weng, Tilman Wolf, “Analytic modeling of network processors for parallel workload ...
DRCP - Telcordia
... For macro-mobility it uses rules similar to HAWAII as far as border router is concerned. It uses two parallel cache system , routing and paging, for location update. Handoff is initiated by the mobile host Proposes a 2-layer method for binding protocol. Uses Mobile IP for global mobility. ...
... For macro-mobility it uses rules similar to HAWAII as far as border router is concerned. It uses two parallel cache system , routing and paging, for location update. Handoff is initiated by the mobile host Proposes a 2-layer method for binding protocol. Uses Mobile IP for global mobility. ...
Advanced Networking Concepts & Troubleshooting
... Each router in OSPF needs to be uniquely identified to properly arrange them in the Neighbor tables. © Wiley Inc. 2006. All Rights Reserved. ...
... Each router in OSPF needs to be uniquely identified to properly arrange them in the Neighbor tables. © Wiley Inc. 2006. All Rights Reserved. ...
Distance Vector Routing Protocols
... If the route is already in the table, the existing entry is replaced if the new entry has a better hop count. The startup router then sends a triggered update out all RIP-enabled interfaces containing its own routing table so that RIP neighbors can be informed of any new routes. ...
... If the route is already in the table, the existing entry is replaced if the new entry has a better hop count. The startup router then sends a triggered update out all RIP-enabled interfaces containing its own routing table so that RIP neighbors can be informed of any new routes. ...
S4.2 Contemporary Network Management
... MIBs: Management Information Bases • A MIB defines the variables that reside in a managed node Defined according to SMI (Structure of Management ...
... MIBs: Management Information Bases • A MIB defines the variables that reside in a managed node Defined according to SMI (Structure of Management ...
CentreVu® Explorer
... Every effort was made to ensure that the information in this document was complete and accurate at the time of printing. However, information is subject to change. Your Responsibility for Your System’s Security Toll fraud is the unauthorized use of your telecommunications system by an unauthorized p ...
... Every effort was made to ensure that the information in this document was complete and accurate at the time of printing. However, information is subject to change. Your Responsibility for Your System’s Security Toll fraud is the unauthorized use of your telecommunications system by an unauthorized p ...
now
... • For large networks, a full mesh topology is seldom affordable. • The issue is not with the cost of the hardware, but because there is a theoretical limit of less than 1,000 VCs per link. In practice, the limit is less than that. • For this reason, larger networks are generally configured in a part ...
... • For large networks, a full mesh topology is seldom affordable. • The issue is not with the cost of the hardware, but because there is a theoretical limit of less than 1,000 VCs per link. In practice, the limit is less than that. • For this reason, larger networks are generally configured in a part ...
ISDN deployments
... SmartNode™ VoIP Gateways Power inode’s Converged Services for ISDN Business Subscribers over-Internet Protocol (VoIP) services for ISDN subscribers. With ISDN Private Business was booming… Broadband Internet access, web hosting, manBranch Exchange (PBX) equipment installed in nearly every office in ...
... SmartNode™ VoIP Gateways Power inode’s Converged Services for ISDN Business Subscribers over-Internet Protocol (VoIP) services for ISDN subscribers. With ISDN Private Business was booming… Broadband Internet access, web hosting, manBranch Exchange (PBX) equipment installed in nearly every office in ...
XAPP941 - 参考系统:PLB 三态以太网 MAC
... © 2007 Xilinx, Inc. All rights reserved. All Xilinx trademarks, registered trademarks, patents, and further disclaimers are as listed at http://www.xilinx.com/legal.htm. PowerPC is a trademark of IBM Inc. All other trademarks and registered trademarks are the property of their respective owners. All ...
... © 2007 Xilinx, Inc. All rights reserved. All Xilinx trademarks, registered trademarks, patents, and further disclaimers are as listed at http://www.xilinx.com/legal.htm. PowerPC is a trademark of IBM Inc. All other trademarks and registered trademarks are the property of their respective owners. All ...
the document - Support
... within the purchase scope or the usage scope. Unless otherwise specified in the contract, all statements, information, and recommendations in this document are provided "AS IS" without warranties, guarantees or representations of any kind, either express or implied. The information in this document ...
... within the purchase scope or the usage scope. Unless otherwise specified in the contract, all statements, information, and recommendations in this document are provided "AS IS" without warranties, guarantees or representations of any kind, either express or implied. The information in this document ...
IP CIP compared to other NonStop TCP/IP products – Technical
... There are two different modes in which data provider namespaces are maintained: A mode where multiple providers are supported (MULTIPROV ON) and a “compatibility mode” where the CLIM operates as it did previously with only a single provider configured (MULTIPROV OFF). The mode is configured by the u ...
... There are two different modes in which data provider namespaces are maintained: A mode where multiple providers are supported (MULTIPROV ON) and a “compatibility mode” where the CLIM operates as it did previously with only a single provider configured (MULTIPROV OFF). The mode is configured by the u ...
Word - ITU
... The ASL-ELCP provides plural complementary communication control protocols such as a clientserver type communication control and/or a bulk transmission control. The ASL-NCP realizes the interface with plural network protocols and could treat various types of network specifications. The ASL-ELCP also ...
... The ASL-ELCP provides plural complementary communication control protocols such as a clientserver type communication control and/or a bulk transmission control. The ASL-NCP realizes the interface with plural network protocols and could treat various types of network specifications. The ASL-ELCP also ...
roomplayer guide
... When you connect a NAS to your home network, it’s a good idea to give it a fixed IP address. Many NAS instruction manuals recommend this too. You see, most products (like an iPhone) are, by default, allocated a dynamic IP address by your router; dynamic IP addresses change all the time. Your NAS dri ...
... When you connect a NAS to your home network, it’s a good idea to give it a fixed IP address. Many NAS instruction manuals recommend this too. You see, most products (like an iPhone) are, by default, allocated a dynamic IP address by your router; dynamic IP addresses change all the time. Your NAS dri ...
2 Synchronisation of networks
... Limitations were highlighted in document ECC PT1(11)113: “New protocols like IEEE1588/PTPv2 (Precision Time Protocol) are currently under study by ITU-T in order to provide accurate phase/time synchronisation, but this type of solution is not fully mature today. Moreover, it will require new hardwar ...
... Limitations were highlighted in document ECC PT1(11)113: “New protocols like IEEE1588/PTPv2 (Precision Time Protocol) are currently under study by ITU-T in order to provide accurate phase/time synchronisation, but this type of solution is not fully mature today. Moreover, it will require new hardwar ...
user manual - CNET Content Solutions
... with remote monitoring and motion detection features for a complete and cost-efective home security solution. C ...
... with remote monitoring and motion detection features for a complete and cost-efective home security solution. C ...
MA-100 Media Adaptor
... This EMS SFP provides the management interface back to the NetComplete EMS. Since the management interface both reads and writes information to it, the EMS SFP must always be a JMEP. Typically, the JMEP EMS SFP is installed in the default network port, and this network port is designated as the EMS ...
... This EMS SFP provides the management interface back to the NetComplete EMS. Since the management interface both reads and writes information to it, the EMS SFP must always be a JMEP. Typically, the JMEP EMS SFP is installed in the default network port, and this network port is designated as the EMS ...