Understanding Computers, Chapter 7
... – Specialty hardware for specific purposes • 3G mobile broadband routers, femtocells, etc. Understanding Computers: Today and Tomorrow, 13th Edition ...
... – Specialty hardware for specific purposes • 3G mobile broadband routers, femtocells, etc. Understanding Computers: Today and Tomorrow, 13th Edition ...
wireless broadband router base station-g
... medium business (SMB) network device that complies with the 2.4GHz IEEE 802..11g standard as well as the IEEE 802.11b standard specification on wireless LANs. IEEE 802.11g technology features longer range than IEEE 802.11a and greater bandwidth with data rates up to 54 Mbps. The AirStation supports ...
... medium business (SMB) network device that complies with the 2.4GHz IEEE 802..11g standard as well as the IEEE 802.11b standard specification on wireless LANs. IEEE 802.11g technology features longer range than IEEE 802.11a and greater bandwidth with data rates up to 54 Mbps. The AirStation supports ...
User Manual PowerLine AV500 Wireless N Mini Extender Starter Kit
... your home - the electrical wiring. Share Internet connections and experience smooth file transfers, streaming multimedia, online gaming and more. The Powerline AV500 Wireless N Mini Extender features easy plug-and-play installation and can be connected to any Ethernet-enabled device. The PowerLine P ...
... your home - the electrical wiring. Share Internet connections and experience smooth file transfers, streaming multimedia, online gaming and more. The Powerline AV500 Wireless N Mini Extender features easy plug-and-play installation and can be connected to any Ethernet-enabled device. The PowerLine P ...
trial_lecture
... across various interfaces and media for vehicular users – ISO TC204/WG16 – Wide Area Communications – IEEE 802.11/11p/15/16e/20, 2G/3G, and ITS systems ...
... across various interfaces and media for vehicular users – ISO TC204/WG16 – Wide Area Communications – IEEE 802.11/11p/15/16e/20, 2G/3G, and ITS systems ...
security engineering
... 802.15 Wireless Personal Area Networks (e.g. Bluetooth) 802.16 Wireless Broadband ...
... 802.15 Wireless Personal Area Networks (e.g. Bluetooth) 802.16 Wireless Broadband ...
STA-UI-A0037s (BlueW_2310 USB version) User`s Manual
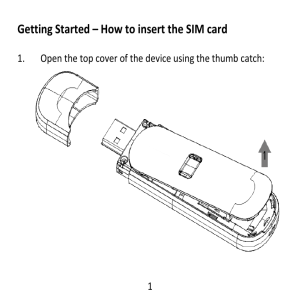
... In a small environment, you can set up a wireless network using a single Access Point and one or more Wireless USB dongle. This type of network provides a coverage area sufficient to satisfy the network requirements for many homes and small businesses. The Access Point connects your network computer ...
... In a small environment, you can set up a wireless network using a single Access Point and one or more Wireless USB dongle. This type of network provides a coverage area sufficient to satisfy the network requirements for many homes and small businesses. The Access Point connects your network computer ...
User Manual Powerline AV 500 Wireless N Mini Extender DHP-W310AV
... see that router’s network name (SSID) here. Extended Wi-Fi When you are browsing for available wireless Network Name: networks, this is the name that will appear in the list. You can choose to extend the same network that your hybrid router is broadcasting (listed above) for convenient whole-home ac ...
... see that router’s network name (SSID) here. Extended Wi-Fi When you are browsing for available wireless Network Name: networks, this is the name that will appear in the list. You can choose to extend the same network that your hybrid router is broadcasting (listed above) for convenient whole-home ac ...
... This equipment and troubleshooting guide is intended to help customers of Broadband Digital Solutions with basic troubleshooting of network connections. The same steps are performed by Broadband Digital Solutions’ own support personnel to establish where the issue may be. In this document the most c ...
WirelessLANs
... o every frame consists of N mini-slots and x data-slots o every station has its own mini-slot and can reserve up to k data-slots using this mini-slot (i.e. x = N * k). o other stations can send data in unused data-slots according to a round-robin sending scheme (best-effort traffic) ...
... o every frame consists of N mini-slots and x data-slots o every station has its own mini-slot and can reserve up to k data-slots using this mini-slot (i.e. x = N * k). o other stations can send data in unused data-slots according to a round-robin sending scheme (best-effort traffic) ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... Otherwise they would be unprofitable for the carriers or it would take too much time until the new communication networks would cover a large area. And maybe until then other communication networks would be developed. That’s what happened to the 3rd generation telecommunication networks. They are st ...
... Otherwise they would be unprofitable for the carriers or it would take too much time until the new communication networks would cover a large area. And maybe until then other communication networks would be developed. That’s what happened to the 3rd generation telecommunication networks. They are st ...
Lecture 2: WPAN
... TCP/IP based applications, for instance information transfer using the Wireless Application Protocol (WAP), can be extended to Bluetooth devices by using the Pointto-Point Protocol (PPP) on top of RFCOMM. ...
... TCP/IP based applications, for instance information transfer using the Wireless Application Protocol (WAP), can be extended to Bluetooth devices by using the Pointto-Point Protocol (PPP) on top of RFCOMM. ...
Huawei HG532e Manual
... If a wireless network adapter is available on your computer, you can connect your computer to the HG532e over a wireless connection. The method for installing the wireless adapter and its driver varies according to different vendors. For details, see the installation guide provided by the vendor of ...
... If a wireless network adapter is available on your computer, you can connect your computer to the HG532e over a wireless connection. The method for installing the wireless adapter and its driver varies according to different vendors. For details, see the installation guide provided by the vendor of ...
IP Camera - Spy Shop
... IPCAM wireless cameras allow you anywhere in the wireless coverage area by using a wireless connection to access the network. However, the wireless signal is required to pass through the walls, ceilings and other objects in the number, thickness, and position will limit its scope. Usually coverage c ...
... IPCAM wireless cameras allow you anywhere in the wireless coverage area by using a wireless connection to access the network. However, the wireless signal is required to pass through the walls, ceilings and other objects in the number, thickness, and position will limit its scope. Usually coverage c ...
W301A User Guide
... W301A is a wireless Access Point based on the latest IEEE802.11n standard while at the same time being backwards compatible with IEEE802.11b/g devices. Adopting the advanced “Multiple in and Multiple out” (MIMO) technology, it can provide a maximum of 300Mbps stable transmitting rate for wireless us ...
... W301A is a wireless Access Point based on the latest IEEE802.11n standard while at the same time being backwards compatible with IEEE802.11b/g devices. Adopting the advanced “Multiple in and Multiple out” (MIMO) technology, it can provide a maximum of 300Mbps stable transmitting rate for wireless us ...
Chapter 5 Lectures Notes
... • Of course, keep in mind that user mobility can change the results. A highly mobile user may be hidden for a short period of time, perhaps when you perform the testing, then be closer to other stations most of the time. If collisions are occurring between users within range of each other, the probl ...
... • Of course, keep in mind that user mobility can change the results. A highly mobile user may be hidden for a short period of time, perhaps when you perform the testing, then be closer to other stations most of the time. If collisions are occurring between users within range of each other, the probl ...
User Guide
... Installing the HG659 on an Ethernet Broadband Network In some communities, network service providers use Ethernet interfaces as Internet interfaces. On this network, your PC is directly connected to the Internet through the Ethernet interface provided by the network service provider. If you have sub ...
... Installing the HG659 on an Ethernet Broadband Network In some communities, network service providers use Ethernet interfaces as Internet interfaces. On this network, your PC is directly connected to the Internet through the Ethernet interface provided by the network service provider. If you have sub ...
Chapter 6 slides, Computer Networking, 3rd edition
... 2.4-2.485 GHz range up to 54 Mbps 802.11n: multiple antennae 2.4-5 GHz range up to 200 Mbps ...
... 2.4-2.485 GHz range up to 54 Mbps 802.11n: multiple antennae 2.4-5 GHz range up to 200 Mbps ...
TL-WN7200N 150Mbps High Power Wireless USB Adapter - TP-Link
... antenna or transmitter. This equipment has been SAR-evaluated for use in hand. SAR measurements are based on a 5mm spacing from the body and that compliance is achieved at that distance. ...
... antenna or transmitter. This equipment has been SAR-evaluated for use in hand. SAR measurements are based on a 5mm spacing from the body and that compliance is achieved at that distance. ...
AirLive AC.TOP Manual
... Federal Communication Commission Interference Statement This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential inst ...
... Federal Communication Commission Interference Statement This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential inst ...
User Guide
... • Avoid using the modem in areas that emit electromagnetic waves or in enclosed metallic structures eg lifts. • The modem is not waterproof. Please keep it dry and store it in a cool, dry place. • Don’t use the modem immediately after a sudden temperature change eg from an air conditioned environmen ...
... • Avoid using the modem in areas that emit electromagnetic waves or in enclosed metallic structures eg lifts. • The modem is not waterproof. Please keep it dry and store it in a cool, dry place. • Don’t use the modem immediately after a sudden temperature change eg from an air conditioned environmen ...
Chapter 6 slides, Computer Networking, 3rd edition
... 2.4-5 GHz range up to 54 Mbps 802.11n (multiple antennae) 2.4-5 GHz range up to 200 Mbps ...
... 2.4-5 GHz range up to 54 Mbps 802.11n (multiple antennae) 2.4-5 GHz range up to 200 Mbps ...
No Slide Title
... There are two kinds of wireless networks: 1) An ad-hoc, or peer-to-peer wireless networks •Each computer communicates directly with each other to: send files, share printers, work collaboratively •They may not be able to access wired LAN resources, unless one of the computers acts as a bridge to th ...
... There are two kinds of wireless networks: 1) An ad-hoc, or peer-to-peer wireless networks •Each computer communicates directly with each other to: send files, share printers, work collaboratively •They may not be able to access wired LAN resources, unless one of the computers acts as a bridge to th ...
lecture10 - Computer and Information Sciences
... up to 300Mbps 5Ghz and/or 2.4Ghz ~230ft range ...
... up to 300Mbps 5Ghz and/or 2.4Ghz ~230ft range ...
VPN Routers - D-Link
... (GRE) tunnels, empowering your mobile users by providing remote access to a central corporate database. Site-to-site VPN tunnels use IP Security (IPSec) Protocol, Point-toPoint Tunneling Protocol (PPTP), or Layer 2 Tunneling Protocol (L2TP) to facilitate branch office connectivity through encrypted ...
... (GRE) tunnels, empowering your mobile users by providing remote access to a central corporate database. Site-to-site VPN tunnels use IP Security (IPSec) Protocol, Point-toPoint Tunneling Protocol (PPTP), or Layer 2 Tunneling Protocol (L2TP) to facilitate branch office connectivity through encrypted ...
Zigbee - K.f.u.p.m. OCW
... The responsibilities of the Zigbee NWK layer include: Starting a network: The ability to successfully establish a new network. Joining and leaving a network: The ability to gain membership (join) or relinquish membership (leave) a network. Configuring a new device: The ability to sufficientl ...
... The responsibilities of the Zigbee NWK layer include: Starting a network: The ability to successfully establish a new network. Joining and leaving a network: The ability to gain membership (join) or relinquish membership (leave) a network. Configuring a new device: The ability to sufficientl ...
Wi-Fi
Wi-Fi (or WiFi) is a local area wireless computer networking technology that allows electronic devices to network, mainly using the 2.4 gigahertz (12 cm) UHF and 5 gigahertz (6 cm) SHF ISM radio bands.The Wi-Fi Alliance defines Wi-Fi as any ""wireless local area network"" (WLAN) product based on the Institute of Electrical and Electronics Engineers' (IEEE) 802.11 standards. However, the term ""Wi-Fi"" is used in general English as a synonym for ""WLAN"" since most modern WLANs are based on these standards. ""Wi-Fi"" is a trademark of the Wi-Fi Alliance. The ""Wi-Fi Certified"" trademark can only be used by Wi-Fi products that successfully complete Wi-Fi Alliance interoperability certification testing.Many devices can use Wi-Fi, e.g. personal computers, video-game consoles, smartphones, digital cameras, tablet computers and digital audio players. These can connect to a network resource such as the Internet via a wireless network access point. Such an access point (or hotspot) has a range of about 20 meters (66 feet) indoors and a greater range outdoors. Hotspot coverage can be as small as a single room with walls that block radio waves, or as large as many square kilometres achieved by using multiple overlapping access points. Wi-Fi can be less secure than wired connections, such as Ethernet, precisely because an intruder does not need a physical connection. Web pages that use TLS are secure, but unencrypted internet access can easily be detected by intruders. Because of this, Wi-Fi has adopted various encryption technologies. The early encryption WEP proved easy to break. Higher quality protocols (WPA, WPA2) were added later. An optional feature added in 2007, called Wi-Fi Protected Setup (WPS), had a serious flaw that allowed an attacker to recover the router's password. The Wi-Fi Alliance has since updated its test plan and certification program to ensure all newly certified devices resist attacks.