Convergence of Wireline IP and Wireless Networks
... of Unified Communication. That trend will continue with SIP forming a common foundation. Data convergence is following WiFi and Edge/GPRS deployment. Hosted ...
... of Unified Communication. That trend will continue with SIP forming a common foundation. Data convergence is following WiFi and Edge/GPRS deployment. Hosted ...
Congestion Control Algorithm - Computer Science and Engineering
... the kernel (i.e., Ethernet driver) must know the hardware address to send the data. ...
... the kernel (i.e., Ethernet driver) must know the hardware address to send the data. ...
computer networking - BSNL Durg SSA(Connecting India)
... capability and responsibility on the network. That is to say, that each machine serves a dual purpose or role, i.e. they are both clients and servers to some extent. ...
... capability and responsibility on the network. That is to say, that each machine serves a dual purpose or role, i.e. they are both clients and servers to some extent. ...
Chap 3
... The primary purpose of DoS attacks is to steal vital information. (T/F) Name three types of DoS attack. The ping of death works based on using very large ICMP packets that must be fragmented to send and when reassembled are too large for the receiver’s buffer. (T/F) How can a router stop packets fro ...
... The primary purpose of DoS attacks is to steal vital information. (T/F) Name three types of DoS attack. The ping of death works based on using very large ICMP packets that must be fragmented to send and when reassembled are too large for the receiver’s buffer. (T/F) How can a router stop packets fro ...
CSCI6268L10 - Computer Science
... ports – Establish a connection with listen() and connect() • IP and UDP were “stateless” protocols ...
... ports – Establish a connection with listen() and connect() • IP and UDP were “stateless” protocols ...
G-Lab Deep: Cross-layer Composition and
... Based on the specific user intent to make an emergency call a workflow of services within the service and network layer must be triggered which together form the emergency call. This workflow may invoke auxiliary services like “get location”, “make a call” and “reserve line” to support the nature of ...
... Based on the specific user intent to make an emergency call a workflow of services within the service and network layer must be triggered which together form the emergency call. This workflow may invoke auxiliary services like “get location”, “make a call” and “reserve line” to support the nature of ...
CV - Emitac – Enterprise Solutions
... Successful migration from Legacy Email Security Gateway to Barracuda SPAM and Virus Firewall at PTA (Pakistan Telecommunication Authority) Islamabad, Pakistan. Waseela Bank Islamabad, Pakistan migration from Microsoft TMG to SOPOS XG Firewall First Women Bank Karachi Pakistan migration from Microsof ...
... Successful migration from Legacy Email Security Gateway to Barracuda SPAM and Virus Firewall at PTA (Pakistan Telecommunication Authority) Islamabad, Pakistan. Waseela Bank Islamabad, Pakistan migration from Microsoft TMG to SOPOS XG Firewall First Women Bank Karachi Pakistan migration from Microsof ...
Network Emulation - School of Computer Science
... – validation of traffic models (traffic aggregation) – protocol testing (TCP congestion/flow control) – QoS support (flows, IntServe/DiffServe behaviours) – distributed applications • Current evaluation environments – simulation (most common) • Software based model of the underlying network. – “live ...
... – validation of traffic models (traffic aggregation) – protocol testing (TCP congestion/flow control) – QoS support (flows, IntServe/DiffServe behaviours) – distributed applications • Current evaluation environments – simulation (most common) • Software based model of the underlying network. – “live ...
Networks & Telecommunications
... • Network interface card (NIC): Device that – provides a computer with unique address – Converts data into signal for transmission ...
... • Network interface card (NIC): Device that – provides a computer with unique address – Converts data into signal for transmission ...
DCE - WordPress.com
... the server without considering whether they run on the same or different architecture, or have same or different byte ordering. ...
... the server without considering whether they run on the same or different architecture, or have same or different byte ordering. ...
Intrusion Detection Systems:
... Complete installation of Snort makes use of other software packages ...
... Complete installation of Snort makes use of other software packages ...
Ip addressing
... With services to translate private addresses to public addresses, hosts on a privately ...
... With services to translate private addresses to public addresses, hosts on a privately ...
The CyberFence Difference
... Operators of industrial control networks often opt to secure communications by tunneling protocols over TLS. While doing so may seem a straightforward solution, it often introduces unanticipated impacts. TLS has a higher overhead relative to VPN or V-LAN encryption, which reduces network performance ...
... Operators of industrial control networks often opt to secure communications by tunneling protocols over TLS. While doing so may seem a straightforward solution, it often introduces unanticipated impacts. TLS has a higher overhead relative to VPN or V-LAN encryption, which reduces network performance ...
Avaya™ G700 Media Gateway Security - Issue 1.0
... phones or to relatively secure phones on the public network and are not carried over the LAN. 14) For backup recovery reasons, transferring the files via FTP to a local PC as the only location for backups is not recommended, unless the local PC is secure. However, backing up to a remote storage devi ...
... phones or to relatively secure phones on the public network and are not carried over the LAN. 14) For backup recovery reasons, transferring the files via FTP to a local PC as the only location for backups is not recommended, unless the local PC is secure. However, backing up to a remote storage devi ...
Network - Blog Universitas Udayana
... • IPX/SPX and NWLink (NetWare) • Allows Windows computers to communicate with Novell based networks • Available as of Windows 95 and NT 4.0 ...
... • IPX/SPX and NWLink (NetWare) • Allows Windows computers to communicate with Novell based networks • Available as of Windows 95 and NT 4.0 ...
Sisteme cu microprocesoare
... Other Application layer protocols DNS (Domain Name System) - is a service that allows addressing messages based on symbolic names, the protocol allows transformation of symbolic names for network addresses (IP addresses) - NFS (Network File System) - is a mapping service that allows remote file fol ...
... Other Application layer protocols DNS (Domain Name System) - is a service that allows addressing messages based on symbolic names, the protocol allows transformation of symbolic names for network addresses (IP addresses) - NFS (Network File System) - is a mapping service that allows remote file fol ...
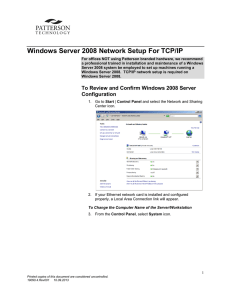
Windows Server 2008 Network Setup For TCP/IP
... Windows Server 2008 Network Setup For TCP/IP For offices NOT using Patterson branded hardware, we recommend a professional trained in installation and maintenance of a Windows Server 2008 system be employed to set up machines running a Windows Server 2008. TCP/IP network setup is required on Windows ...
... Windows Server 2008 Network Setup For TCP/IP For offices NOT using Patterson branded hardware, we recommend a professional trained in installation and maintenance of a Windows Server 2008 system be employed to set up machines running a Windows Server 2008. TCP/IP network setup is required on Windows ...
ch 11 Data Network Connectivity
... system to another. Internet gateway - allows and manages access between LANs and the Internet. LAN gateway - allows segments of a LAN running different protocols, network access methods, or transmission types to ...
... system to another. Internet gateway - allows and manages access between LANs and the Internet. LAN gateway - allows segments of a LAN running different protocols, network access methods, or transmission types to ...
Data Network Connectivity
... of e-mail system to another. Internet gateway - allows and manages access between LANs and the Internet. LAN gateway - allows segments of a LAN running different protocols, network access methods, or transmission types to communicate with each other. Voice/data gateway - allows a data network to iss ...
... of e-mail system to another. Internet gateway - allows and manages access between LANs and the Internet. LAN gateway - allows segments of a LAN running different protocols, network access methods, or transmission types to communicate with each other. Voice/data gateway - allows a data network to iss ...
Ch 2: Exploring Control Types and Methods
... If wires allow traffic to flow in loops, this can lead to a broadcast storm To prevent this, switches use – STP (Spanning Tree Protocol) or ...
... If wires allow traffic to flow in loops, this can lead to a broadcast storm To prevent this, switches use – STP (Spanning Tree Protocol) or ...
1-Introduction :
... Network Access Devices (Hubs, Bridges ,Switches, and wireless access points that call “Repeaters”) Internetworking Devices (Routers) Communication Servers and Modems Security Devices (Firewalls) The management of data as it flows through the network is also a role of the intermediary devices ...
... Network Access Devices (Hubs, Bridges ,Switches, and wireless access points that call “Repeaters”) Internetworking Devices (Routers) Communication Servers and Modems Security Devices (Firewalls) The management of data as it flows through the network is also a role of the intermediary devices ...
1 - Portal UniMAP
... a. Mesh topology: If one connection fails, the other connections will still be working. b. Star topology: The other devices will still be able to send data through the hub; there will be no access to the device which has the failed connection to the hub. c. Bus Topology: All transmission stops if t ...
... a. Mesh topology: If one connection fails, the other connections will still be working. b. Star topology: The other devices will still be able to send data through the hub; there will be no access to the device which has the failed connection to the hub. c. Bus Topology: All transmission stops if t ...
Lecture 1 - WordPress.com
... Authentication - assurance that communicating entity is the one claimed ...
... Authentication - assurance that communicating entity is the one claimed ...