TECHNOLOGY-DRIVEN METRICS
... SANS Critical Control 4: Continuous Vulnerability Assessment Run vulnerability scans on all systems at least weekly, preferably daily. Problem fixes are verified through additional scans. Vulnerability scanning tools (updated) for: wireless, server, endpoint, etc. Automated patch management too ...
... SANS Critical Control 4: Continuous Vulnerability Assessment Run vulnerability scans on all systems at least weekly, preferably daily. Problem fixes are verified through additional scans. Vulnerability scanning tools (updated) for: wireless, server, endpoint, etc. Automated patch management too ...
Better manage and secure your infrastructure
... Auditor Core starts by collecting data, in real-time, from your infrastructure. Using this accurate, up-to-date source of information, Auditor Core can then relate this to users, what kind of device they are using and which location they are in. It also has a powerful policy sub-system which allows ...
... Auditor Core starts by collecting data, in real-time, from your infrastructure. Using this accurate, up-to-date source of information, Auditor Core can then relate this to users, what kind of device they are using and which location they are in. It also has a powerful policy sub-system which allows ...
Chapter 1 THE INFORMATION AGE IN WHICH YOU LIVE Changing
... Availability – a service or resource is available when it's supposed to be ...
... Availability – a service or resource is available when it's supposed to be ...
What Is Highly Critical Wireless Networking (HCWN)
... A Highly Critical Wireless Network (HCWN) may consist of several interconnected communications devices used to support a critical function. HCWN are commercial wireless systems that use the TCPIP digital protocols, which are beginning to dominate our communications infrastructure and reshape our ind ...
... A Highly Critical Wireless Network (HCWN) may consist of several interconnected communications devices used to support a critical function. HCWN are commercial wireless systems that use the TCPIP digital protocols, which are beginning to dominate our communications infrastructure and reshape our ind ...
The Network Layer
... packet size of 8 payload bytes plus header. (c) Fragments after passing through a size 5 gateway. ...
... packet size of 8 payload bytes plus header. (c) Fragments after passing through a size 5 gateway. ...
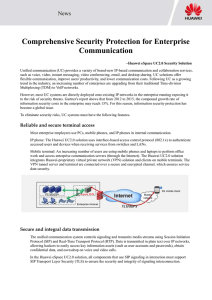
Comprehensive Security Protection for
... and emails. The Huawei UC2.0 solution classifies user information into personal and public information based on data sensitivity levels. Users (especially senior executives) can set refined and level-based information access policies, preventing enterprise address book information leak. ...
... and emails. The Huawei UC2.0 solution classifies user information into personal and public information based on data sensitivity levels. Users (especially senior executives) can set refined and level-based information access policies, preventing enterprise address book information leak. ...
Local Area Networks: Internetworking
... Identify the main characteristics of asynchronous transfer mode, including the roles of the virtual path connection and the virtual channel connection. Discuss the importance of the classes of service available with asynchronous transfer mode as well as the ATM’s advantages and disadvantages. Identi ...
... Identify the main characteristics of asynchronous transfer mode, including the roles of the virtual path connection and the virtual channel connection. Discuss the importance of the classes of service available with asynchronous transfer mode as well as the ATM’s advantages and disadvantages. Identi ...
426Introduction
... Used analog transmission system Requires setting up a connection before transfer of information can take place (called “circuit switching”) ...
... Used analog transmission system Requires setting up a connection before transfer of information can take place (called “circuit switching”) ...
Networks 1 (LAN)
... Watch: http://www.youtube.com/watch?v=o4rMFxgETus In Word create a revision poster to tell someone what each network type is, how it works and an example diagram. (Use a screenshot from the video) ...
... Watch: http://www.youtube.com/watch?v=o4rMFxgETus In Word create a revision poster to tell someone what each network type is, how it works and an example diagram. (Use a screenshot from the video) ...
Guide to Operating System Security
... Make sure IPChains is turned off Start IPTables service and ensure that it starts automatically each time OS is booted Configure firewall to deny incoming, outgoing, and forwarded packets Make sure all configured options are saved and reused each time computer is booted ...
... Make sure IPChains is turned off Start IPTables service and ensure that it starts automatically each time OS is booted Configure firewall to deny incoming, outgoing, and forwarded packets Make sure all configured options are saved and reused each time computer is booted ...
Traffic Monitoring using sFlow
... Security and Audit Trail Analysis Gartner estimates that 70% of security incidents that actually cause loss to enterprises involve insiders, while service providers and other organizations are constantly bombarded with various other (external) attacks. A comprehensive security strategy involves pro ...
... Security and Audit Trail Analysis Gartner estimates that 70% of security incidents that actually cause loss to enterprises involve insiders, while service providers and other organizations are constantly bombarded with various other (external) attacks. A comprehensive security strategy involves pro ...
Introduction to Internet
... • The network traffic is the packets • When sending a file, it is broken up into packets • Packet size ranges from 100 bytes to 1500 bytes • Packet has a header (filename, origin & destination, order number of packet 5 of ...
... • The network traffic is the packets • When sending a file, it is broken up into packets • Packet size ranges from 100 bytes to 1500 bytes • Packet has a header (filename, origin & destination, order number of packet 5 of ...
Working Group on Social Inclusion
... The Technical Secretariat will play the role of Administrative and Communications Coordinator and will be managed by the Fundación Secretariado Gitano. Its main functions will include: •Participation in the Management Committee meetings, taking charge of prior distribution of the meeting agenda and ...
... The Technical Secretariat will play the role of Administrative and Communications Coordinator and will be managed by the Fundación Secretariado Gitano. Its main functions will include: •Participation in the Management Committee meetings, taking charge of prior distribution of the meeting agenda and ...
Introduction - COW :: Ceng
... It simplifies the implementation of multi-agent systems through a middle-ware that complies with the FIPA -Foundation for Intelligent Physical Agents specifications and through a set of graphical tools that supports the debugging and deployment phases. ...
... It simplifies the implementation of multi-agent systems through a middle-ware that complies with the FIPA -Foundation for Intelligent Physical Agents specifications and through a set of graphical tools that supports the debugging and deployment phases. ...
CIS6930: Advanced Topics in Networking
... – Select a node as the root – Build a spanning tree from the root – Nodes are partitioned into layers based on the position in the spanning tree – The channel from a lower layer node to a higher layer node is the up link, the channel from a higher layer node to a lower layer node is a down link, cha ...
... – Select a node as the root – Build a spanning tree from the root – Nodes are partitioned into layers based on the position in the spanning tree – The channel from a lower layer node to a higher layer node is the up link, the channel from a higher layer node to a lower layer node is a down link, cha ...
What Is Security Metadata?
... Who and what’s on my network? Are devices on my network secure? Is user/device behavior appropriate? ...
... Who and what’s on my network? Are devices on my network secure? Is user/device behavior appropriate? ...
THE INFORMATION AGE IN WHICH YOU LIVE Changing the Face
... cable Internet service in a home or small office – One port to plug into DSL or cable connection to connect to the Internet – Usually several ports to build a network for home computers or printers and share Internet connection ...
... cable Internet service in a home or small office – One port to plug into DSL or cable connection to connect to the Internet – Usually several ports to build a network for home computers or printers and share Internet connection ...
Chapter 1 THE INFORMATION AGE IN WHICH YOU LIVE Changing
... capable of providing high-speed Internet service All Internet access methods on the previous slide are broadband except the dialup modem ...
... capable of providing high-speed Internet service All Internet access methods on the previous slide are broadband except the dialup modem ...
View File - University of Engineering and Technology, Taxila
... communication networks easy Competition among providers of transmission facilities reduced the cost of data circuits ...
... communication networks easy Competition among providers of transmission facilities reduced the cost of data circuits ...
slides - Microsoft Research
... We are also seeing emerging needs to isolate subnets for purposes such as security, QoS, sensitive data, special AUPs, etc. Existing options (like firewalls) are inadequate ...
... We are also seeing emerging needs to isolate subnets for purposes such as security, QoS, sensitive data, special AUPs, etc. Existing options (like firewalls) are inadequate ...
Networks
... connected together by what are called gateways - these make the system act as if it was one huge network. Many networks in industry, business, higher education and government institutions are all connected to the Internet although anybody can now get connected to the system with the appropriate hard ...
... connected together by what are called gateways - these make the system act as if it was one huge network. Many networks in industry, business, higher education and government institutions are all connected to the Internet although anybody can now get connected to the system with the appropriate hard ...